Zero trust access control, achieved by integrating Illumio Core with FileFlex Enterprise, allows organizations to effectively mitigate data breaches and ransomware risks, ensuring enhanced security, visibility, and operational efficiency through centralized management and strict access controls.
How to Enforce Zero Trust Access Control to Mitigate Data Breach and Ransomware
Estimated reading time: 4 minutes
Table of Contents
-
-
- Introduction: Enhancing Data Security through Zero Trust Access Control with Illumio Core and FileFlex Enterprise
- Understanding Illumio Core
- Understanding FileFlex Enterprise
- Steps to Achieve Zero Trust Enforced Access
- Benefits of This Approach
- Conclusion: Achieving Robust Data Security with Zero Trust Access Control
-
Introduction: Enhancing Data Security through Zero Trust Access Control with Illumio Core and FileFlex Enterprise

Understanding Illumio Core
Illumio Core is a zero-trust micro-segmentation and security platform that enables organizations to visualize, segment, and control network traffic across their environments. It allows for the implementation of fine-grained security policies to control how applications and users interact with different network segments and resources.
Understanding FileFlex Enterprise
FileFlex Enterprise is a secure zero-trust data access and sharing solution that enables organizations to centrally control and manage access to their files across diverse storage environments.
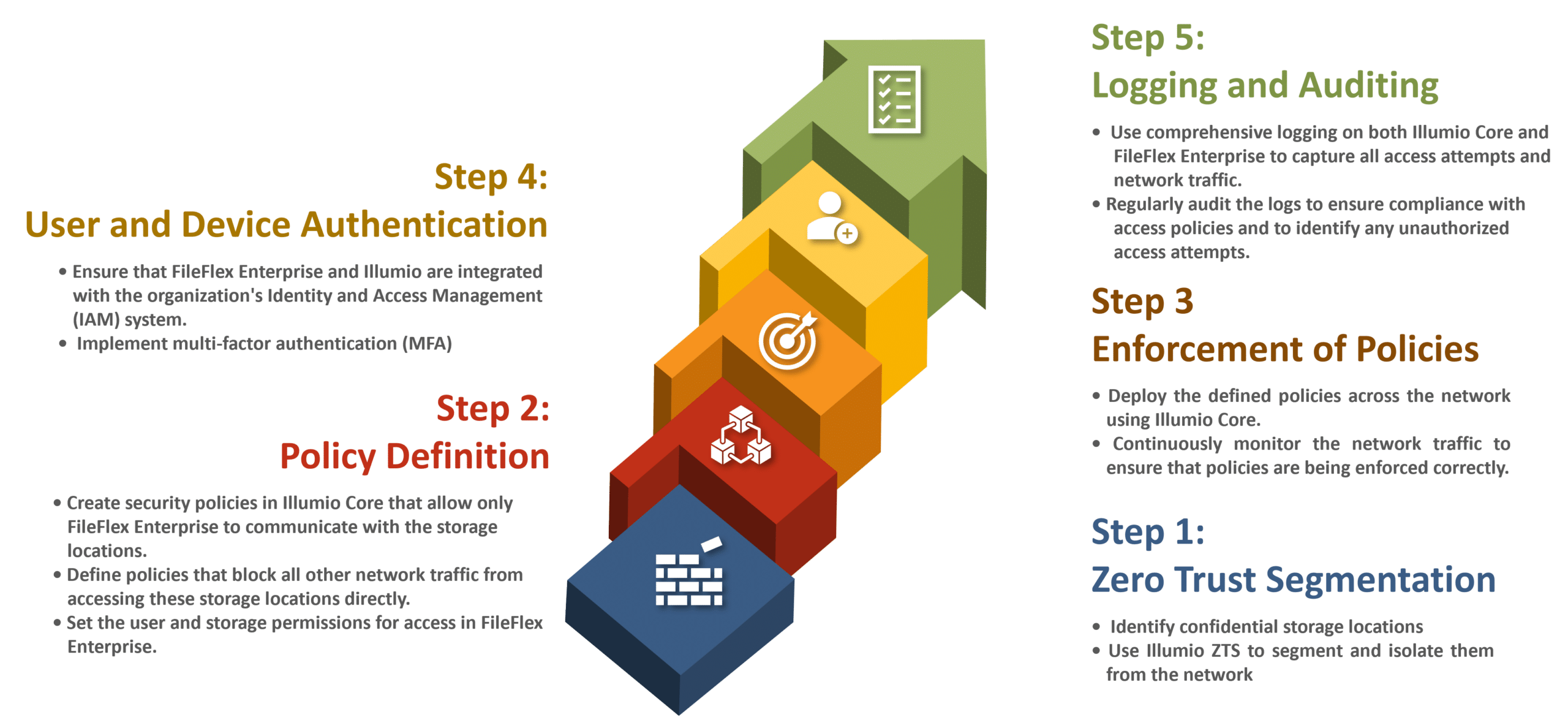
Steps to Achieve Zero Trust Enforced Access
By integrating Illumio Core with FileFlex Enterprise, organizations can direct all user data access requests through a secure channel, preventing unauthorized access to storage locations and potential breaches. Here’s how this can be achieved:
- Identify Storage Locations: Identify all the storage locations (on-premises or private cloud) that users need to access via FileFlex Enterprise.
- Segment the Network: Use the zero trust segmentation ability of Illumio Core to create segments for these storage locations, isolating them from the rest of the network.
-
Step 2: Policy Definition:
- Define Security Policies for ZTDA Access: Create security policies in Illumio Core that allow only the FileFlex Enterprise ZTDA server(s) to communicate with the storage locations.
- Block Direct Access: Define policies that block all other network traffic from accessing these storage locations directly. This includes traffic originating from user devices or other applications that are not part of the FileFlex Enterprise infrastructure.
- Set ZTDA Permissions: Set the user and storage repository permissions for access and sharing in FileFlex Enterprise.
-
Step 3: Enforcement of Policies:
- Apply Policies: Deploy the defined policies across the network using Illumio Core, ensuring that the enforcement is consistent and robust.
- Monitor and Adjust: Continuously monitor the network traffic to ensure that policies are being enforced correctly. Make adjustments as needed to address any bypass attempts or unintended access.
-
Step 4: User and Device Authentication:
- Integrate with IAM: Ensure that FileFlex Enterprise and Illumio core are integrated with the organization’s Identity and Access Management (IAM) system to authenticate users and devices before granting access to storage locations.
- Enforce 2FA/MFA: Implement multi-factor authentication (MFA) to enhance security for user access via Illumio/FileFlex.
-
Step 5: Logging and Auditing:
- Logging: Use comprehensive logging on both Illumio Core and FileFlex Enterprise to capture all access attempts and network traffic.
- Audit Access: Regularly audit the logs to ensure compliance with access policies and to identify any unauthorized access attempts.
Benefits of This Approach
Using Illumio Core to prevent direct access to sensitive data repositories and push all requests through FileFlex Enterprise offers several benefits to organizations by enhancing their security framework through zero trust principles. Here are the key advantages:
-
Enhanced Zero Trust Security
- Expanded Micro-Segmentation: Illumio’s micro-segmentation now includes data access control, reducing attack surfaces. See Why You Need Zero Trust Data Access Micro-Segmentation.
- Centralized Access Control: All data requests are funneled through FileFlex, ensuring centralized monitoring and control. See The Top 7 Benefits of Network File Access Control Using Zero Trust Data Access
- Ransomware Mitigation: Combined defenses prevent lateral movement during the infiltration phase and data activity monitoring to detect ransomware during the data extraction phase. See How to Reduce Ransomware Risk Using Zero Trust Data Access (ZTDA).
-
Improved Visibility and Control
- Real-Time Monitoring: Organizations gain real-time visibility into network traffic and data activity.
- Detailed Activity Logs: FileFlex provides comprehensive logs of all data access and sharing activities, aiding in threat detection and behavior monitoring.
-
Policy Creation and Enforcement
- Granular Policies: IT managers can create and enforce detailed access policies based on user roles and permissions, enhancing data governance. See Embracing Zero Trust Data Access for IT-Controlled Chain-of-Command
- Compliance and Auditing: The integration aids in meeting regulatory requirements through extensive auditing and reporting capabilities. See Using Zero Trust Data Access for NIST Compliance, CMMC Compliance for File Sharing, Access and Collaboration of CUI Using Zero Trust Data Access, and GDPR Compliant File Sharing Using Zero Trust Data Access
-
Operational Efficiency
- Unified Access and Sharing: Simplifies management by providing a unified control solution across diverse storage environments, including on-premises and cloud-hosted data.
- Reduced Complexity: Streamlines access management, reducing the complexity of handling multiple access methods and diverse storage locations.
-
Enhanced User Experience
- Seamless Integration: Provides a user-friendly experience by integrating with existing workflows and federating storage access within Windows.
- Secure File Sharing and Collaboration: Facilitates secure data sharing and collaboration by implementing strict access controls. See Zero Trust Data Access for Secure File-Sharing and Content Collaboration Using Zero Trust Data Access
-
Scalability and Infrastructure Efficiency
- Scalable Access Control: Can scale to accommodate growing data volumes without significantly increasing infrastructure load.
- Reduced Infrastructure Demand: Centralized access and sharing reduce the need for multiple data copies, optimizing storage and bandwidth usage.
-
Simplified Vendor Management
- Consistent Security Approach: Offers a uniform security strategy across different storage solutions, simplifying vendor management and reducing the need for multiple sharing and VPN platforms.
Use Cases
Zero Trust Data Access (ZTDA), as implemented by FileFlex Enterprise, combined with Illumio core offers a secure, cost-effective alternative to traditional VPNs, FTP, MFT, virtual data room, and content collaboration platforms. It enhances security with micro-segmentation, simplifies access management, improves user experience, and ensures compliance ultimately reducing operational costs while safeguarding sensitive data.
Conclusion: Achieving Robust Data Security with Zero Trust Access Control
In conclusion, by integrating Illumio Core with FileFlex Enterprise, organizations can effectively implement a Zero Trust access control strategy to mitigate data breaches and ransomware risks, ensuring enhanced security, visibility, and operational efficiency. This setup enhances security by preventing direct access to storage locations and ensures that all access is authenticated, authorized, and logged through a centralized system. This approach not only strengthens data protection but also simplifies management and compliance efforts.
*CSO
Learn More About FileFlex Sign Up for a Free Trial