
Achieving NIST compliance requires granular, auditable control over how sensitive data is accessed and shared.
Zero Trust Data Access (ZTDA) complements NIST cybersecurity guidelines—especially NIST SP 800-53 and SP 800-207—by enforcing strict access controls at the file level, verifying identity continuously, and logging all interactions for auditability. While NIST defines what’s needed, ZTDA provides a practical path to meet those requirements.
Zero Trust Data Access for NIST Compliance
Estimated reading time: 6 minutes
Table of Contents
-
- What is NIST?
- What are the NIST Publications Relevant to Cybersecurity Standards for Government and Contractors?
- What is the Relationship Between NIST and Cybersecurity Standards for the Federal, State and Municipal Governments?
- Why a Zero Trust Architecture Matters for NIST Compliance
- How Zero Trust Data Access Helps with NIST Compliance for the Access, Sharing and Collaboration of Unstructured Data
- Use Cases for Zero Trust Data Access in the NIST-Compliant Organization
- Summary

What is NIST?
NIST stands for the National Institute of Standards and Technology. It’s a non-regulatory federal agency within the United States Department of Commerce. NIST is particularly well-known for its work in developing cybersecurity frameworks and standards, such as the Cybersecurity Framework and publications like the NIST Special Publication 800 series, which covers various aspects of information security.
What are the NIST Publications Relevant to Cybersecurity Standards for Government and Contractors?
Here are some key NIST publications that provide guidance, best practices, and standards that help organizations effectively manage cybersecurity risk:
- NIST Special Publication (SP) 800-53: This publication provides a comprehensive catalog of security controls for federal information systems and organizations.
- NIST Special Publication (SP) 800-171: SP 800-171 outlines security requirements for protecting Controlled Unclassified Information (CUI) in non-federal systems and organizations. It provides guidelines for contractors and other non-federal entities that handle CUI on behalf of the government, specifying security controls necessary to safeguard this information.
- NIST Cybersecurity Framework (CSF): The Cybersecurity Framework is a voluntary framework designed to help organizations manage and reduce cybersecurity risk.
- NIST Special Publication (SP) 800-171A: This publication provides assessment procedures for evaluating the effectiveness of security controls outlined in NIST SP 800-171.
- NIST Special Publication (SP) 800-161: SP 800-161 focuses on supply chain risk management (SCRM) for federal information systems and organizations.
- NIST Special Publication (SP) 800-137: This publication provides guidelines for implementing continuous monitoring programs for federal information systems and organizations.
These are the main examples of the many NIST publications relevant to cybersecurity standards for government agencies and contractors. NIST continually updates and expands its publications to address emerging cybersecurity challenges and developments in technology and best practices.
What is the Relationship Between NIST and Cybersecurity Standards for the Federal, State and Municipal Governments?
Federal Government: NIST is responsible for developing cybersecurity standards and guidelines that federal agencies must adhere to.
State Governments: While states are not legally bound to follow NIST guidelines, many choose to adopt them voluntarily. Examples are California, New York, Texas, Virginia and Michigan.
Local and Municipal Governments: Similar to state governments, local and municipal governments can choose to adopt NIST cybersecurity standards voluntarily. Examples are Los Angeles, Seattle, Austin, New York, and San Francisco.
What is the Relationship Between NIST Guidelines and Federal Contractors?
The relationship between NIST guidelines and federal contractors can be characterized in several ways:
- Compliance Requirements: Federal contractors are often required to comply with specific cybersecurity standards and guidelines outlined by NIST. These requirements are typically included in contracts, regulations, or policy directives, such as the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS).
- Security Frameworks: Federal contractors may voluntarily adopt the NIST Cybersecurity Framework to enhance their cybersecurity posture and align with the expectations of their government clients.
- Risk Management: Federal contractors are expected to implement risk-based approaches to cybersecurity in line with NIST recommendations, considering factors such as the sensitivity of the data they handle and the potential impact of security breaches on government operations.
- Supply Chain Security: Contractors are expected to implement NIST supply chain risk management measures to ensure the integrity and confidentiality of products and services delivered to the government.
- Cybersecurity Assessments and Audits: Federal contractors may undergo cybersecurity assessments and audits to evaluate their compliance with NIST guidelines when specified in their contracts.
What are the NIST Requirements for User Access, Sharing and Collaboration of Unstructured Data?
Here’s a summary of key considerations based on NIST’s recommendations:
-
Access Control:
- Implement granular access controls to ensure that users only have access to the unstructured data necessary for their job functions. Use role-based access controls (RBAC), attribute-based access controls (ABAC), and other mechanisms to enforce the principle of least privilege.
-
Authentication and Authorization:
- Require strong authentication mechanisms, such as multi-factor authentication (MFA), to verify the identity of users accessing unstructured data. Implement dynamic authorization mechanisms based on contextual factors like user identity, device posture, and behavior to adapt access privileges.
-
Encryption and Protection:
- Encrypt unstructured data both in transit and at rest to protect it from unauthorized access. Use encryption mechanisms like Transport Layer Security (TLS) for data in transit and encryption algorithms for data at rest. Implement data loss prevention (DLP) measures to prevent unauthorized data disclosure.
-
Monitoring and Auditing:
- Continuously monitor access to unstructured data and maintain detailed audit logs of user activities. Use logging and monitoring tools to detect unauthorized access attempts, suspicious behavior, and data breaches. Regularly review audit logs to ensure compliance with access control policies and regulatory requirements.
-
Secure Collaboration and Sharing:
- Implement secure mechanisms for collaboration and sharing of unstructured data with internal and external parties. Use secure file transfer protocols, encryption, and access controls to ensure that data shared externally remains protected. Educate users on secure collaboration practices and data-sharing policies.
-
Policy-Based Controls:
- Define and enforce access control policies tailored to the organization’s risk management strategy and regulatory obligations. Establish clear policies and procedures for user access, sharing, and collaboration of unstructured data, and regularly review and update them to address evolving threats and compliance requirements.
Why a Zero Trust Architecture Matters for NIST Compliance
A Zero Trust Architecture (ZTA) aligns closely with the cybersecurity standards outlined by NIST and in particular the principles outlined in NIST SP-800-171v2, specifically emphasizing zero trust access control. (See How to Meet NIST Guidelines for Zero Trust for Remote Data Access.)
Within this framework, a central server plays a critical role in verifying user identities and authenticating permissions. Instead of allowing direct access to the original resource location, requested files are delivered after verification and authentication by the server. This is illustrated in Diagram 1, a simplified zero-trust architecture.
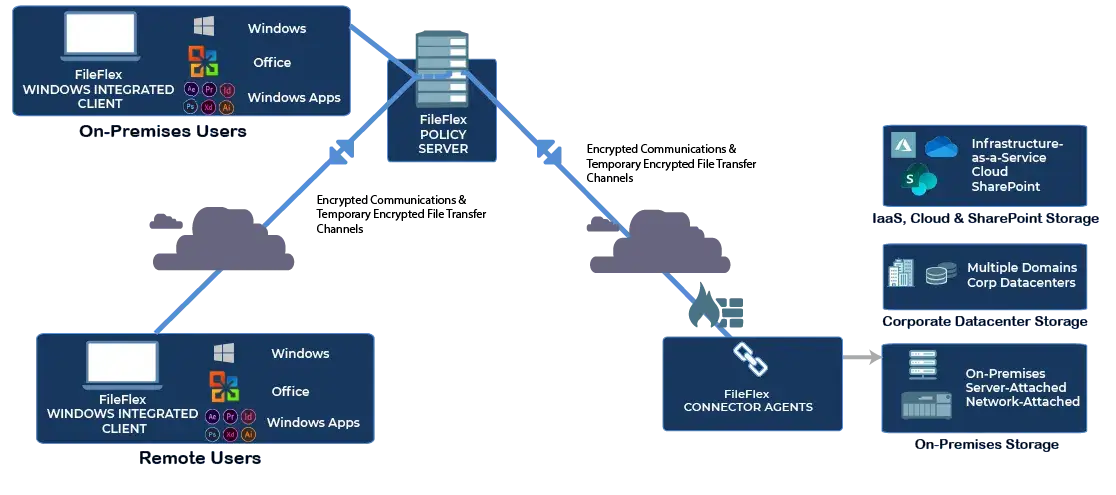 Diagram 1
Diagram 1
Simplified Zero Trust Architecture for NIST Compliance
- Users have no direct access to infrastructure
- All users are verified and all requests are authenticated against permissions
- Creates an IT-controlled chain of command
- Delivers least privilege access
- Provides a log of all activities
A Zero Trust Architecture enables access, sharing, collaboration, and management of files and folders across multiple repositories—be it cloud-based, FTP, SharePoint, or on-premises storage.
Management retains detailed control over access and restrictions, aligning with the principle of Least Privilege and the established IT hierarchy. Additionally, by centralizing all actions through the zero-trust server, records of activities are maintained, aiding forensic investigations and for output to the SIEM to detect ransomware attacks in progress (see How to Reduce Ransomware Risk Using Zero Trust Data Access).
Implementing zero trust principles via a ZTA is the key to achieving NIST compliance regarding secure access, sharing, and collaboration.
How Zero Trust Data Access Helps with NIST Compliance for the Access, Sharing and Collaboration of Unstructured Data
Zero Trust Data Access (ZTDA) as implemented by FileFlex Enterprise can play a significant role in helping organizations achieve NIST compliance for the access, sharing, and collaboration of unstructured data by implementing a more granular and secure approach to data access. Here’s how ZTDA aligns with NIST principles and can assist with compliance:
-
Implements Granular Access Control:
- ZTDA emphasizes the principle of least privilege, where users are only granted access to the specific data they need to perform their job functions. This aligns with NIST’s access control requirements, ensuring that unauthorized users cannot access sensitive unstructured data.
-
Enforces User Verification:
- ZTDA aligns with NIST’s recommendations for multi-factor authentication (MFA) and risk-based access controls, helping organizations verify the identity of users accessing unstructured data and adapt access privileges based on changing risk conditions.
-
Includes Activity Monitoring and Auditing:
- ZTDA provides visibility into data access and usage through its activity monitoring and auditing capabilities. This enables organizations to track access to unstructured data, detect unauthorized activities, and generate audit trails for compliance purposes, addressing NIST’s requirements for audit and accountability.
-
Provides Data Encryption and Protection:
- ZTDA incorporates in-transit encryption of both the data microchannel and the data itself.
-
Delivers Secure Collaboration and Sharing:
- ZTDA enables secure collaboration and sharing of unstructured data by providing controlled and audited methods for sharing data with external parties.
Overall, Zero Trust Data Access can help organizations achieve NIST compliance for the access, sharing, and collaboration of unstructured data. By implementing Zero Trust Data Access as implemented by FileFlex Enterprise, organizations can strengthen their cybersecurity posture and demonstrate adherence to NIST guidelines for protecting sensitive information.
| NIST Requirement | How Zero Trust Data Access Helps |
| Least privilege access (AC-6) | Enforces per-file access rules per user/device |
| Access control policy (AC-1) | Centralized enforcement of granular data permissions |
| Audit logging (AU-2, AU-6) | Real-time file activity logs for audits and compliance |
| Session controls (AC-12) | Validates every file access, even within a session |
| Data integrity (SI-7) | Ensures only authorized changes and access |
| Continuous monitoring (CA-7) | Real-time monitoring of file access and movement |
Use Cases for Zero Trust Data Access in the NIST-Compliant Organization
Some practical use cases for the implementation of Zero Trust Data Access as implemented by FileFlex Enterprise for organizations that need to implement NIST cybersecurity standards are as follows:
NIST Compliant VPN Alternative
-
-
-
- ZTDA can be used as a NIST-compliant VPN alternative that delivers cutting-edge security, simplified access management, IT-controlled chain of command, file sharing/collaboration functionality, and with Windows integration, enhanced user experience. See 19 Advantages of the Zero Trust Data Access VPN Alternative.
-
-
NIST Compliant Secure File Sharing
-
-
-
- ZTDA provides NIST-compliant file-sharing that delivers data protection, and efficient sharing of federated storage, simplifies the user experience, enhances data privacy and compliance, and provides exemplary data governance and an IT-controlled chain of command with no duplication or syncing. See Zero Trust Data Access for Secure File-Sharing.
-
-
NIST Compliant FTP Alternative
-
-
-
- ZTDA is a NIST-compliant FTP alternative that offers cutting-edge security, ransomware prevention, regulatory compliance, simplified management, enhanced user experience, and more. Read Zero Trust Data Access as an FTP Alternative.
-
-
NIST Compliant MFT Alternative
-
-
-
- ZTDA is a contemporary alternative that addresses the security vulnerabilities of MFT. It offers granular file and folder micro-segmentation, has unique federated storage management, encompasses distinctive granular contractor access and brings an IT-controlled chain of command. For more see, Zero Trust Data Access as a Managed File Transfer Alternative.
-
-
NIST Compliant Zero Trust Content Collaboration
-
-
-
- ZTDA can be used as a NIST-compliant zero trust content collaboration platform that safeguards files through micro-segmentation and stringent access to elevate security, streamline workflows, reduce the risk of ransomware and more, providing a cost-effective, adaptable, and user-friendly solution. See Content Collaboration Using Zero Trust Data Access.
-
-
NIST Compliant Virtual Data Rooms
-
-
-
- Delivers NIST-compliant Zero Trust Virtual Data Rooms that offer superior data security, robust protection against ransomware, superior governance and chain-of-command and comprehensive insider threat prevention, while also ensuring compliance, reducing the attack surface, and providing a cost-effective, future-proof approach. Read Top 13 Reasons to Adopt Zero Trust Secure Virtual Data Rooms.
-
-
NIST Compliant Enhancement for Microsoft 365
-
-
-
- Integrating into Microsoft 365 E5, particularly for remote and external users, elevates security posture, reduces the risk of data breaches, enhances regulatory compliance, and mitigates insider threats, ultimately fortifying data protection and access management within the Microsoft ecosystem. See 21 Reasons to Supplement Microsoft 365 E5 Security with Zero Trust Data Access.
-
-
NIST Compliant SharePoint Add-in
-
-
-
- As a SharePoint add-in, it delivers robust security, flexible data access, and compliance capabilities, making it indispensable for modern organizations prioritizing data protection and efficient collaboration, particularly for remote and external users. See 19 Reasons Why Zero Trust Data Access is an Essential SharePoint Add-in.
-
-
Reduces Your Costs
-
-
-
- Zero Trust Data Access technology as implemented by FileFlex reduces your VPN, FTP, MFT, file sharing, content collaboration, virtual data room and cloud storage setup, maintenance and use to dramatically reduce your costs. See How Zero Trust Data Access Cuts Costs in Organizational Operations.
-
-
Summary
In conclusion, adhering to the National Institute of Standards and Technology (NIST) cybersecurity standards is fundamental to governmental organizations. Zero Trust Data Access has emerged as a central technology, as it aligns with NIST guidelines and offers organizations a framework that strengthens data security, compliance, and resilience against evolving threats.

Watch
Meeting NIST Standards for Remote Data Access & Sharing
* Congressional Research Service
Learn More About FileFlex Sign Up for a Free Trial
Frequently Asked Questions
Does Zero Trust Data Access meet NIST requirements?
ZTDA is not a certification, but it enforces many of the principles in NIST SP 800-53 and 800-207—such as least privilege, access control, and audit logging.
What role does ZTDA play in a NIST-aligned strategy?
ZTDA controls how users and devices access sensitive data, making it a critical part of enforcing NIST’s access control, audit, and identity verification requirements.
Can ZTDA support continuous monitoring as required by NIST?
Yes. ZTDA provides real-time visibility into file access, sharing, and movement, which supports continuous monitoring and response per NIST guidance.
Is ZTDA suitable for federal or regulated environments?
Yes. ZTDA works with on-premises, hybrid, and FedRAMP-certified environments to enforce secure access aligned with federal cybersecurity standards like NIST.