Secure the Data Layer
of Zero Trust
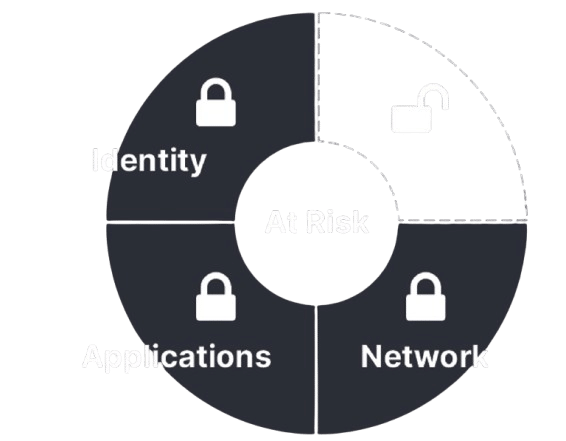
80% of All Corporate Data is Unstructured:
Identity Locked | Network Locked | Application Locked
Data Remains Wide Open See how it works
Hackers Don't Steal Your Network.
They Steal Your Data.
The Problem:
Today’s Zero Trust Security Infrastructure Falls Short. Today Zero Trust compliance stops at identity, networks, and applications. Unstructured Data remains at risk.
The Solution:
Zero Trust Data Security.
Zero Trust Data Access completes your Zero Trust strategy in the data layer.
It applies least privilege, just-in-time, and governance controls directly
to files wherever they re-side — without moving them.
Meet FileFlex Enterprise: An easy to implement overlay service that applies Zero Trust Data Access to the data layer.
What it is
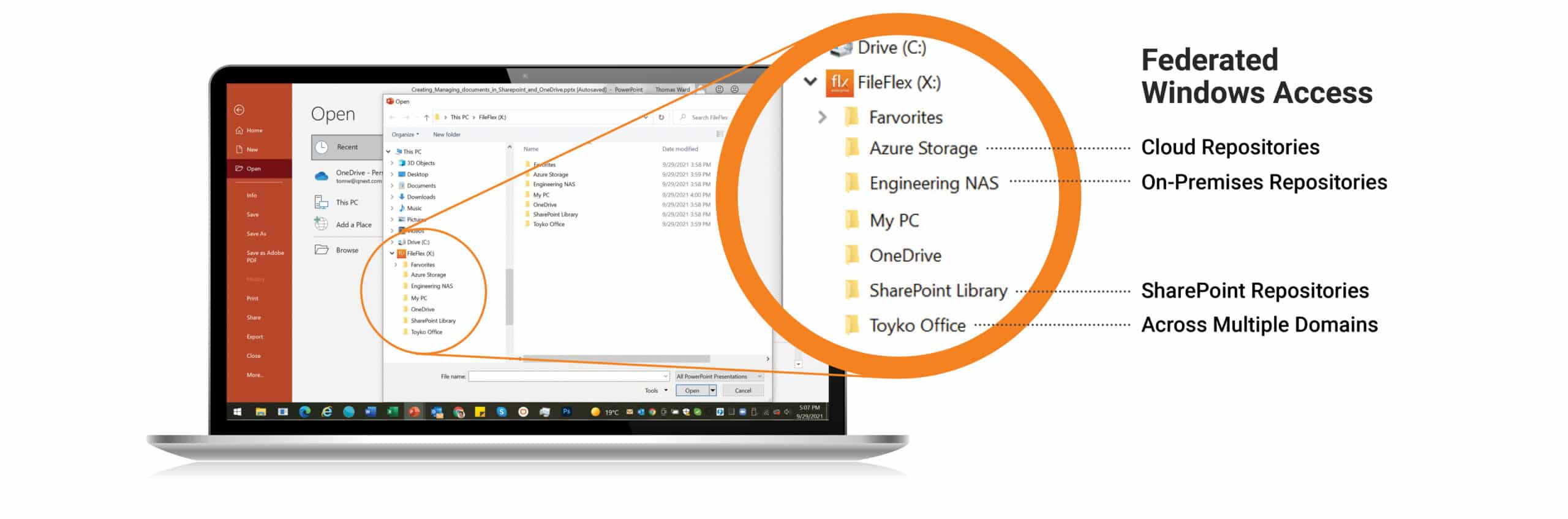
- FileFlex Enterprise is a data security and productivity platform that overlays your existing infrastructure. It federates access across on-premises, Cloud, SharePoint, FTP, and NAS storage, enforcing Zero Trust Data Access policies without data migration.
- Overlay service for hybrid data storage environments
- Zero Trust enforcement at the unstructured data layer
- Secure access, sharing, and collaboration without data duplication
- Supports modern workflows like Virtual Data Rooms, large file access, and legacy system integration
Zero Trust Access for Unstructured Data
- Built for Zero Trust Data
A true Zero Trust platform and modern replacement for VPNs. - Access data, not infrastructure
Users see only the files they’re authorized to use—nothing more. - Data never moves
No copying, syncing, or migration. Lower costs. No data sprawl. - End-to-end encrypted
Encrypted in transit, never at rest outside the source. - Full visibility and auditability
Real-time logging of every file transaction, anywhere. - Plug-and-play Windows integration
Driver-level integration delivers seamless Zero Trust Data Access. - Total control. Fast deployment.
100% centralized control over unstructured data—installed in a day
Trusted by Organizations to Deliver Real Outcomes
Transforming Data Workflows with Zero Trust Data Access
Collaboration & Sharing
Collaboration & Sharing secures internal and external collaboration without duplication or risky email attachments
Read More →Zero Trust Virtual Data Rooms
Governed environments for sensitive workflows like mortgage approvals and M&A. Reduce/Replace VPN with Zero Trust Data Access — an IT-controlled alternative.
Read More →FTP/MFP Replacement
Modernize legacy file transfer systems with Zero Trust Data Access secure access.
Read More →Replace VPN
A VPN alternative that delivers an IT-controlled chain of command using Zero Trust Data Access.
Read More →Key Capabilities
Data Governance
Data Governance Maintains complete control over your organization’s data—where it lives, who can access it, and what they can do with it—through centralized policies, activity visibility, and on-demand auditability.
Read More →Regulatory Compliance
Regulatory Compliance Reduces compliance risk by enforcing least-privilege access, eliminating uncontrolled file sharing, and providing detailed audit trails that align with GDPR, HIPAA, DORA, FFIEC, GLBA, NIST, CMMC and other standards.
Read More →Federated Hybrid Access
Federated Hybrid Access Single-pane-of-glass seamless, policy-controlled data access to files across on-premises storage, private cloud, legacy systems, and remote offices—without migration, VPNs, or exposure of your network.
Read More →Complete Zero Trust Security
Complete Zero Trust Security Protects sensitive data with true Zero Trust Data Access— verifying every user, device, and request while ensuring files are never copied, synced, or exposed beyond what policies explicitly allow.
Read More →