A zero-trust secure content collaboration platform safeguards data through stringent access controls, reducing the risk of ransomware, and enhancing overall cybersecurity, ensuring a resilient and secure platform for collaborative work.
Secure Content Collaboration Using Zero Trust Data Access
Estimated reading time: 5 minutes
Table of Contents
-
- What is collaboration in the digital age?
- What is enterprise content or document collaboration?
- Why do teams and organizations want to use an enterprise content collaboration (document collaboration) platform?
- Why is a Zero Trust Architecture Important for a Content Collaboration Platform?
- What is the Difference Between a First Generation and a Zero Trust Generation Content Collaboration Platform?
- Top 15 Reasons to Adopt an Enterprise Content Collaboration Platform Built on a Zero Trust Architecture
- Conclusion: The Advantages of Empowering Secure Content Collaboration via a Zero Trust Architecture

What is collaboration in the digital age?
Collaboration in the digital age refers to the way people work together using digital tools and technologies. It’s about leveraging technology to enhance communication, coordination, and cooperation among individuals or groups, regardless of their physical location. This can include online platforms, project management tools, video conferencing, cloud computing, and various other digital solutions that facilitate teamwork. The goal is to streamline processes, improve efficiency, and enable seamless collaboration in a virtual or distributed environment.
What is enterprise content or document collaboration?
Enterprise content collaboration (document collaboration) involves a shared effort among individuals to contribute, review, and refine a document over a period of time. It typically follows a sequential process where different team members take turns making revisions, providing feedback, or adding content to the document. Collaboration in this context may include tasks such as version control, where different versions of the document are managed to track changes and ensure a coherent progression.
Why do teams and organizations want to use an enterprise content collaboration (document collaboration) platform?
Enterprise content collaboration (or document collaboration) offers several benefits that make it valuable for organizations and teams:
-
Efficiency:
- It streamlines the document creation and editing process, reducing the time required to produce a final version.
-
Version Control:
- Collaborative tools often include versioning features, ensuring that teams are working on the latest iteration of a document and allowing for easy tracking of changes.
-
Accessibility:
- Team members can access and work on documents from anywhere with an internet connection, promoting flexibility and remote collaboration.
-
Reduced Email Overload:
- Instead of relying on email exchanges for document sharing and feedback, collaboration platforms provide a centralized and organized space for all relevant discussions.
-
Enhanced Accuracy:
- With multiple eyes on a document, errors and inconsistencies are more likely to be caught and corrected, leading to higher-quality outputs.
-
Integration with Workflows:
- Many collaboration tools integrate with other project management and communication tools, creating a seamless workflow for teams.
-
Collaboration Across Time Zones:
- Teams spread across different time zones can work on the same document without the constraints of traditional working hours.
-
Cost Savings:
- Digital collaboration reduces the need for physical meetings, travel, and printed materials, contributing to cost savings for organizations.
-
Knowledge Sharing:
- It facilitates the sharing of expertise and insights among team members, promoting a collaborative learning environment.
In essence, document collaboration fosters a more agile, connected, and efficient working environment, aligning with the demands of the modern workplace.
Why is a Zero Trust Architecture Important for a Secure Content Collaboration Platform?
The adoption of a zero-trust architectural framework aligns with the principles of zero-trust access control, as outlined in NIST SP-800-171v2. Within the context of a zero-trust architecture applied to access, sharing, and collaboration in a content collaboration platform, a policy server plays a crucial role in verifying user identities and permissions. It efficiently delivers requested files to users without allowing direct shared access to the source location.
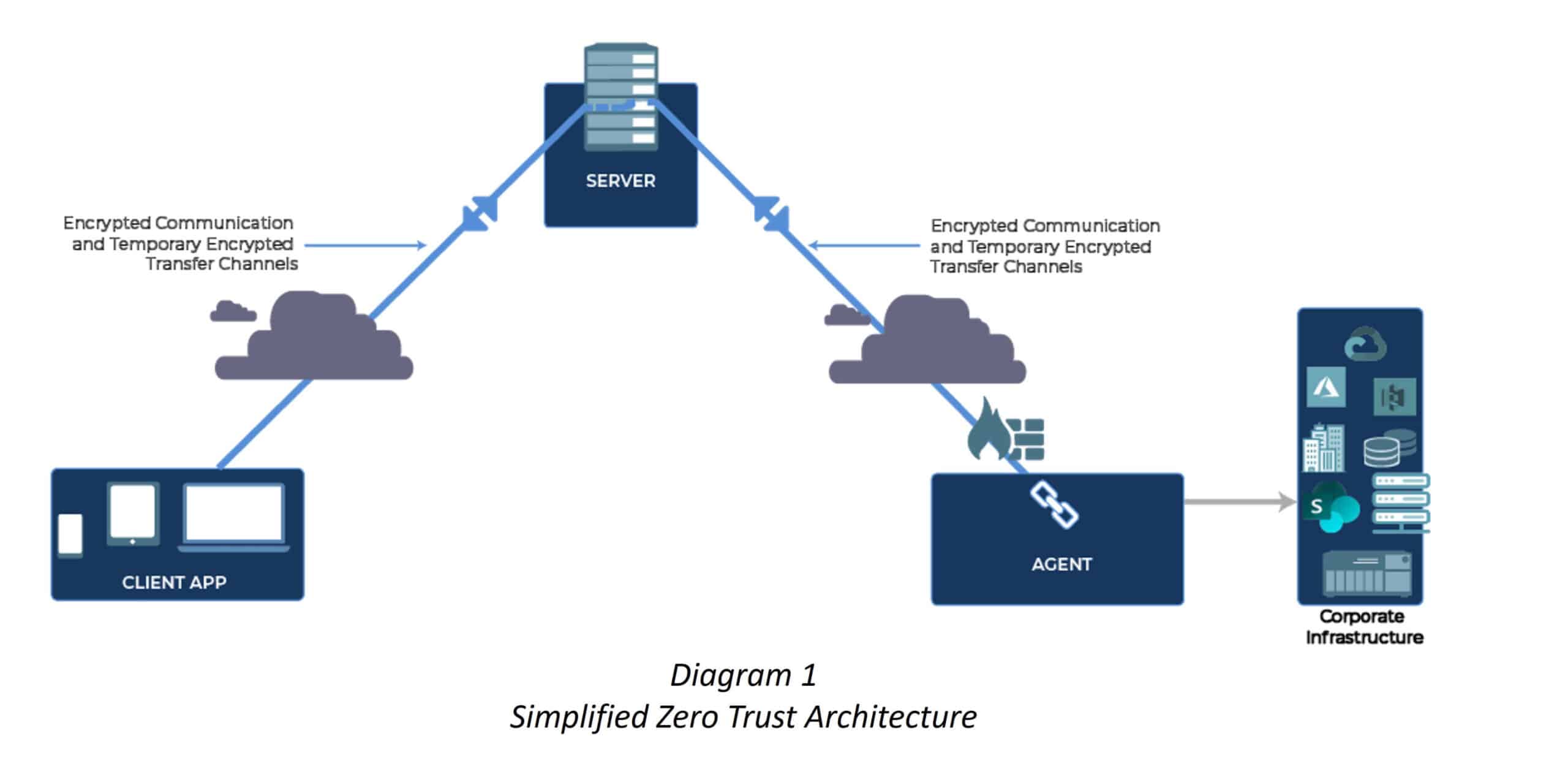

This zero-trust approach is specifically designed to enhance cybersecurity by minimizing the attack surface and mitigating the risk of unauthorized access or data breaches within the content collaboration platform. For deeper insights into zero-trust principles and architecture, please refer to resources on Zero Trust Data Access and Zero Trust Access Methods.
What is the Difference Between a First Generation and a Zero Trust Generation Content Collaboration Platform?
First-generation content collaboration platforms, such as AWS WorkDocs, Dropbox, Box, Citrix, Kiteworks, OneDrive and Google Docs emphasize collaborative access and file management from their centralized servers and storage. This means duplicating or synchronizing files to a server controlled by the service provider and does not extend collaboration capabilities to files stored in other locations.
In contrast, the adoption of Zero Trust Data Access, as implemented by FileFlex, ushers in a new era for secure content collaboration platforms. This innovative approach empowers organizations to securely establish content collaboration across their entire infrastructure, including on-premises, cloud-hosted, and SharePoint storage. Zero Trust Data Access excels in delivering enhanced access control, micro-segmentation, adherence to least privilege principles, robust activity monitoring and authentication, compliance with privacy regulations, adaptability, scalability, heightened insider threat mitigation, reduced ransomware risk, and comprehensive support for data governance throughout the organizational infrastructure, extending beyond files stored in managed silos.
The distinctions between the two can be succinctly summarized as follows:
-
-
Difference Between Centralized vs. Decentralized Storage:
- Traditional content collaboration platforms adopt a centralized model, requiring file replication or synchronization to a central server. Zero Trust Data Access follows a decentralized strategy, enabling users to access files directly from their original storage locations, fostering flexibility, resource efficiency, heightened security, and cost reductions.
-
Differences in File Sharing and Collaboration:
- Both traditional platforms and FileFlex’s implementation of Zero Trust Data Access offer file-sharing and collaboration capabilities like file locking, version control, redaction, watermarking, e-signatures and creation of virtual data rooms among teams, however traditional platforms are confined to sharing and collaborating on files stored within their platforms, while Zero Trust Data Access enables collaboration with files located anywhere within the organizational infrastructure.
-
Difference in Windows File Explorer Integration:
- While some traditional platforms integrate with Windows File Explorer, this integration is limited to files stored within their centralized servers. Zero Trust Data Access takes a federated approach to all hybrid storage types such as cloud storage, on-premises storage, SharePoint storage and FTP storage, incorporating all diverse storage locations into the Windows environment, providing full Windows functionality for accessed storage and enabling in-app file collaboration operations directly from remote repositories.
-
Disparities in Network File Access, Network File Access Control, and Network Security:
- It is beyond the scope of traditional platforms to provide network file access, network file access control, and network security. Zero Trust Data Access extends capabilities with granular access control while restricting access to data VLANs. Through monitoring and control of user network access, FileFlex minimizes the attack surface, aligns with compliance requirements, and aids in mitigating insider threats.
-
Differentiations in Data Governance:
- Traditional platforms primarily apply governance measures to files confined to their platforms. Zero Trust Data Access reinforces cybersecurity through comprehensive data governance standards across the entire organizational storage infrastructure, aligning with access controls, data segmentation, user tracking and authentication, adherence to least privilege principles, and other protective measures.
-
Contrasts in IT Control:
- First-generation content collaboration platforms cannot provide IT control over the intricate organizational structure of unstructured data. Zero Trust Data Access empowers centralized control over file access and facilitates distributed administration, ensuring consistent and secure governance throughout the entire file ecosystem.
-
Distinctions in Regulatory Compliance:
- Traditional platforms focus on aiding compliance for files stored exclusively within their platforms. Zero Trust Data Access offers a comprehensive solution to safeguard access to all unstructured data storage repositories, aiding in compliance with regulatory requirements across the entire infrastructure through detailed provisions for authentication, authorization, access control, monitoring, encryption, activity logs, auditing, and data governance.
-
-
Divergencies in Reducing the Risk of Ransomware:
- It is beyond the scope of first-generation platforms to reduce the risk of ransomware. Zero Trust Data Access however provides access controls, constraints on lateral movement, and activity monitoring designed to detect and reduce the risk of ransomware attacks.
To understand more read File Sharing and Collaboration Evolution from First Generation Platforms to Zero Trust Data Access.
Top 15 Reasons to Adopt a Secure Enterprise Content Collaboration Platform Built on a Zero Trust Architecture
A secure enterprise content collaboration platform (document collaboration platform) built on a zero-trust architecture offers enhanced security and several benefits for organizations over traditional cloud-based enterprise content collaboration (document collaboration):
-
Enhances Security:
- The zero-trust model operates on the premise that threats may originate from both external and internal sources. Requiring authentication and authorization for each user seeking access to the collaboration platform markedly diminishes the likelihood of unauthorized entry, thereby strengthening overall security.
-
Reduces Ransomware Risk:
-
- Content collaboration platforms employing the Zero Trust model counteract ransomware by controlling shared access to sensitive data, diligently monitoring user activities, and curbing lateral movement within the network. This proactive approach assists in the prevention of ransomware attacks and helps protect the integrity of data.
-
Mitigates Insider Threats:
- Zero Trust effectively reduces the risk of insider threats through verification of all users and devices, irrespective of their roles or positions within the organization. This approach mitigates the potential for unauthorized or malicious activities by insiders, effectively thwarting any attempts at unauthorized access by employees or contractors. Access control is based on user roles, curbing lateral movement and fortifying the security of the infrastructure.
-
Augments Data Privacy and Compliance:
-
- The principles of Zero Trust effortlessly conform to data protection and compliance standards, including but not limited to HIPAA, GDPR, CIRCI, CMMC, ISO 27001, ENISA, and various regulatory frameworks. Through the implementation of zero trust access controls, organizations can enhance the security of sensitive customer data, ensuring a more forceful adherence to regulatory compliance.
-
Reduces the Attack Surface:
- Zero Trust optimizes security by segmenting and isolating storage resources and by eliminating the need to duplicate data to secondary locations. This strategy effectively diminishes the attack surface, making it significantly more challenging for potential attackers to move laterally within the network, thereby curbing the proliferation of threats.
-
Adapts Well to Remote Work and Contractor Integration:
- In our modern work landscape, characterized by remote work and widespread mobile device usage, Zero Trust enables content collaboration from anywhere. Moreover, it provides contractors and gig-workers with controlled shared access, and thanks to its use of micro-segmentation and least privilege principles, it effectively mitigates risks associated with contractor, gig-worker, partner, supplier or other external party data access.
-
Provides Granular Micro-Segmentation:
- A Zero Trust Data Access architecture provides IT the ability to segment storage into smaller, isolated zones and limit access to those zones only to users who need to access that data. This principle of least-privilege access also limits the lateral movement of malicious actors within the system to contain and isolate potential security breaches.
-
Delivers Improved Data Visibility, Control and Incident Response Capabilities:
- Since all activities must be authorized and controlled by a zero-trust policy server, all actions are known and recorded in a log that can be accessed directly or exported to a SIEM. Exporting to a SIEM enables management to observe user behavior, spot irregularities, and recognize potential security threats. They can then potentially isolate and remediate an attack in process.
-
Offers Seamless Integration, Extraordinary User Experience and Familiar Workflow:
- Zero Trust Data Access as implemented by FileFlex seamlessly integrates with Windows File Explorer and popular Windows applications like Microsoft 365, Adobe, and AutoCAD. This integration enhances the user experience, streamlines data access, and eliminates the need for additional content collaboration, virtual data rooms or file-sharing platforms. Users continue with the apps and workflows that they are already familiar with.
-
Extends Better Protection to Emerging Threats:
- The adaptive nature of zero trust makes the collaboration platform more resilient to evolving cyber threats. It can quickly adapt to new attack vectors and vulnerabilities.
-
Supplies Management an IT-Controlled Chain-of-Command and Superior Data Governance:
- The administration panel supplies management with detailed controls over permission levels, even down to the file level on either a group or individual basis to provide IT-controlled chain-of-command and governance over sensitive data. Since all data transfers are handled by a Zero Trust policy server, management has a detailed activity log that can be used to monitor user behavior, detect unusual behavior, and identify potential security threats.
-
Provides for the Creation of Collaborative Virtual Data Rooms:
- Virtual data rooms are an important tool for content collaboration. A zero-trust architecture allows users to create as many rooms with as many participants in those rooms as needed. Participants can include clients/partners/suppliers or external parties and each user can be established with their own permission levels at no additional cost. (view-only, downloading prohibited, no editing, etc.) Data rooms can also be set up by IT. Further, virtual data rooms can be located from any storage location such as SharePoint, on-premises (NAS, server NAS, etc), or cloud-hosted storage so that sensitive data does not need to be stored on third-party servers. Data room activity is logged for analytics, monitoring, and alerts. For more information see Top 13 Reasons to Adopt Zero Trust Secure Virtual Data Rooms.
-
Federates Hybrid and Multi-Cloud Environments:
- A Zero Trust architecture enables secure content collaboration from on-premises (NAS, SAN, server, PC), cloud-hosted or SharePoint storage repositories and federates these in Windows Explorer and by extension any Windows app (Office, Adobe, AutoCAD, etc.).
-
Is a More Cost-Effective Model:
- Zero Trust Data Access as implemented by FileFlex, allows organizations to reduce or even eliminate duplication to expensive cloud storage, cloud content collaboration, virtual data room, VPN and FTP/MFT platforms. Organizations pay via a fixed user-based low monthly subscription fee, making it a more economical solution.
-
Enables Reliable and Trustworthy Partner Collaboration:
- Teams that include partners, suppliers, clients, or other third parties can collaborate with access controlled only to necessary resources, managed by IT, to minimize and contain third-party risk to the organization.
Conclusion: The Advantages of Empowering Secure Content Collaboration via a Zero Trust Architecture
In conclusion, adopting an enterprise content collaboration platform built on a zero-trust architecture is imperative for organizations aiming to elevate security, streamline workflows, and adapt to the evolving demands of the modern workplace. This transformative approach not only helps protect against emerging cyber threats but also provides a cost-effective, adaptable, and user-friendly solution, paving the way for a more secure and efficient era of content collaboration.
In the following webinar, Tom Ward, VP of Marketing for Qnext explains zero trust-based collaboration.
Watch ‘Zero Trust Data Collaboration for Remote Workers’
To understand more about how a Zero Trust Data Access platform can help your organization see Top 13 Reasons to Adopt Zero Trust Secure Virtual Data Rooms and Top 13 Reasons to Use a Zero Trust Secure File-Sharing Platform for Business.
* Zippia
Learn More About FileFlex Sign Up for a Free Trial