THE CHALLENGE:
Unstructured Data is the Major Security Problem for Ransomware
With your unstructured data stored over thousands of devices in multiple domains and numerous methods of access, it has become a problem from a security, productivity and data governance perspective.
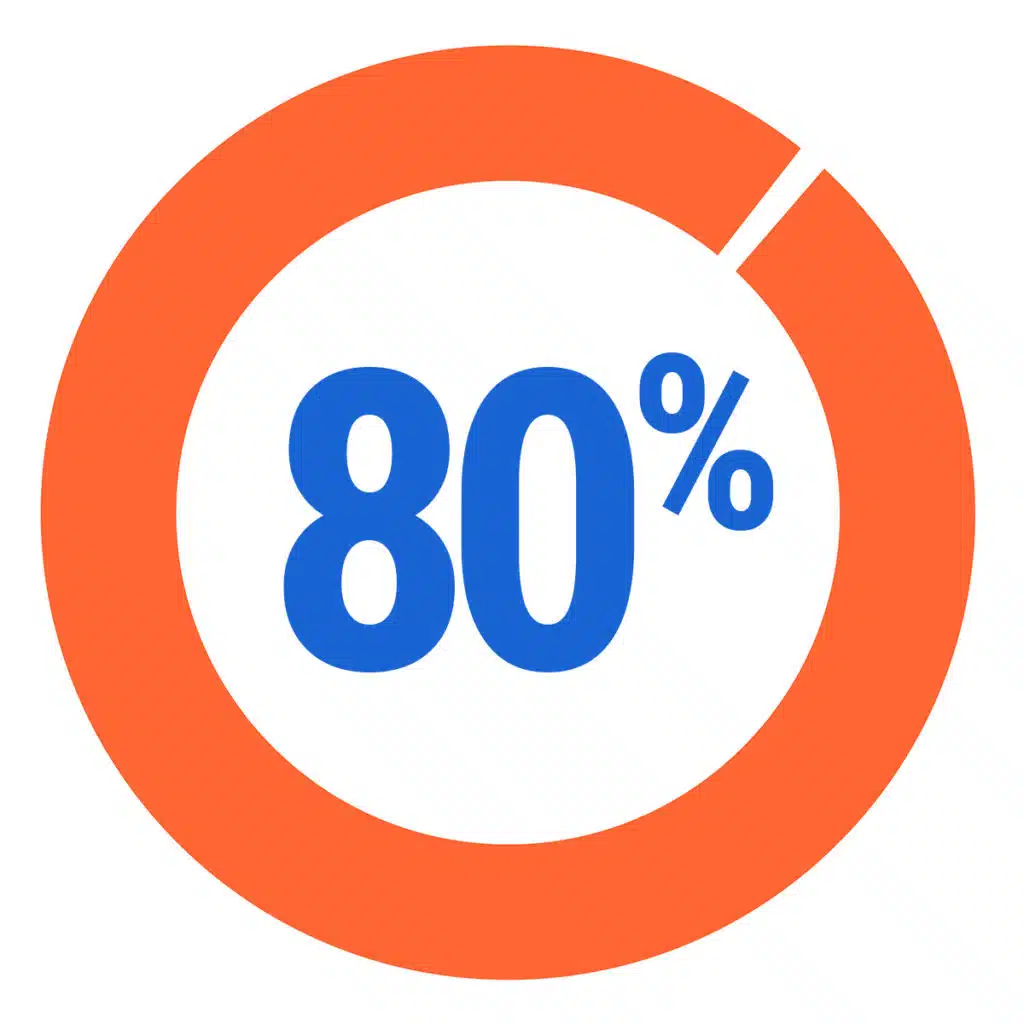
“Upward of 80% of enterprise data today is unstructured.”
– Gartner
The Expanding Chaos of Unstructured Data
FileFlex Enterprise federates access to disparate unstructured data repositories in Windows.
The storage infrastructure of modern organizations today is incredibly complex. IDC estimates that by 2025 there will be 175 zettabytes of data globally, with 80% of that data being unstructured. Files and folders – your company data – are located over thousands of locations — on-premises devices like servers, server-attached, network-attached and PC storage.
They can be cloud solutions hosted by Microsoft, Amazon or Google or they can be stored on self-hosted or Microsoft-hosted implementations of SharePoint. And, more often than not, these are stored over multiple domains and global locations.
As a result of this complexity, 99% of IT security specialists have issues governing and managing unstructured data. The massive and disparate amount of unstructured data is a problem from a security, productivity and data governance perspective.
With your unstructured data stored over thousands of devices in multiple domains and numerous methods of access, it has become a problem from a security, productivity and data governance perspective.
How FileFlex Transforms Enterprise Data Security
Unstructured data is located throughout a complex hybrid-IT infrastructure
- On-premises
- Public and private clouds
- Multiple domains
- Multiple devices
- Multiple locations
The unmanaged growth of unstructured data, disparate information silos and multiple methods of access has led to increased organization-wide exposure to ransomware

“Ransomware …ultimately requires access to files and file repositories if it is to be effective. As such, ransomware is a data access issue.”

Increased Vulnerability to Ransomware
FileFlex Enterprise reduces the risk of ransomware through security controls and a zero trust architecture.
According to IDC, 37% of organizations have been hit with ransomware, and ransomware complaints to the FBI are up 62%. Ransomware is at epidemic levels today with many organizations being attacked. 80% of enterprise data is unstructured and, according to Gartner, the primary vector for ransomware is the rise of unstructured data as ransomware is primarily a data access issue.
The cost of ransomware is not just in payments to the hackers, but in investigation, recovery, fines and credit remediation.

“As ransomware continues to wreak havoc on organizations, security and risk management leaders must take a data-centric view of this data-focused threat.”

Rogue Information Silos and Access Solutions
FileFlex Enterprise is a single solution that provides federated access to disparate silos of unstructured data.
Unstructured data is stored across thousands of repositories – from on-premises PCs, NAS, and servers to cloud-hosted storage on Amazon, Microsoft and Google, to SharePoint storage. The result is that there are thousands of silos of information and multiple methods of access. Organizations lack a single solution that provides federated access to these disparate silos.

Ungoverned Data Access Problems
FileFlex Enterprise provides IT with a management console and real-time activity log to govern and track remote access to unstructured data.
With thousands of users accessing thousands of data silos, IT managers lack key information as to who, what and when unstructured data is being accessed. It is difficult to know where confidential information is stored, or control access to it.
Increased Headaches of Remote Work and Use of Contractors
FileFlex Enterprise allows IT to provide controlled least-privileged access to contractors and gig workers.
Not only do we have a tremendous proliferation of unstructured data and an epidemic of ransomware, but we have also seen a massive restructuring of the workforce compounding the security, productivity and governance problems IT decision-makers face. We have shifted from a workforce of employees working from organization-owned facilities to a distributed workforce that includes contractors and gig workers that are often remote. They can be on corporate-owned PCs or their personal devices which can include their laptops, tablets and phones. These remote workers, contractors and gig workers also need controlled access to appropriate content on the organization’s complex hybrid-IT infrastructure without necessarily giving them VPN access.
This paradigm shift has been accelerated and magnified with the recent Covid-19 pandemic and the massive increase in work-from-home. This has thrown a new level of remote data access at hybrid IT infrastructures.

The Workforce Works From Anywhere, On Any Device
- On-premises or remote
- Corporate or personal computers
- Mobile devices
Current Remote Access and Sharing Solutions are Insufficient
Multiple remote access and sharing solutions are the norm in enterprises today compounding issues in governance, security, productivity and costs.
VPNs: In a business environment, the VPN connects remote users and satellite offices to the organization’s network. The problem with the VPN is that it lacks the security of a Zero Trust architecture and lacks granular role-based policy control, the ability to micro-segment , least-privilege access, detailed activity logs or alerts and lacks the ability to share files. Finally, since VPNs are widely used, they are a honeypot for hackers and need constant updates and maintenance.
Enterprise File Sync and Share (EFSS): In order to share files organizations have complimented VPNs with Enterprise File Sync and Share solutions. The problem with EFSS solutions are that they are based on a centralized cloud architecture where files are generally synced, copied or duplicated to a third party creating a fragmented separate silo of information. They also lack the security of a Zero Trust architecture and do not provide access to the company infrastructure or SharePoint.
Zero Trust Network Access, Zero Trust Application Access: To address the security shortcomings of the VPN, organizations are now adopting Zero Trust Network Access (ZTNA) and Zero Trust Application Access (ZTAA) solutions. Although they provide identity management, micro-segmentation, least-privilege access and control to a network segment or application, they also allow access to every file and folder on that segment or accessible by that application. They also do not provide file sharing or collaboration capability.


Enter FileFlex Enterprise
FileFlex Enterprise provides the remote file access functionality of a VPN but with a zero trust architecture. It provides the file-sharing capability of Enterprise File Sync and Share,
but from all the storage of the organization’s infrastructure, not just the files synced to the EFSS servers. And it is a great complement to Zero Trust Network Access and Zero Trust Application Access solutions as it provides IT- controlled access micro-segmented to the file and folder level and is not limited to a network segment or application, but applies to the entire infrastructure of on-premises, cloud-hosted and SharePoint storage.

INDEPENDENT REPORT:
Understanding Zero Trust Data Access Using Fileflex
Edited By Dr. Edward Amoroso, CEO & Senior Analyst, Tag Cyber
This Report explains how zero trust data access (ZTDA) can be implemented across an enterprise. Zero trust data access (ZTDA) provides an effective means for externally sharing unstructured data in a secure manner. And external users with work from-anywhere connections to enterprise applications, without the need for VPN support. This publication outlines the basics of the emerging ZTDA model, involving the creation of a secure, remote-access infrastructure.





