Ransomware attacks in 2023 pose a pervasive and costly threat to organizations, but adopting Zero Trust Data Access (ZTDA) through FileFlex Enterprise offers granular access controls, minimizes lateral movement, and helps the detection of data extraction through robust activity monitoring, to reduce the risk of ransomware and aid data protection and uninterrupted business operations.
How to Reduce Ransomware Risk Using Zero Trust Data Access (ZTDA)
Estimated reading time: 2.5 minutes
Introduction: How Zero Trust Data Access Can Thwart a Ransomware Attack
Using the Zero Trust Data Access (ZTDA) of FileFlex Enterprise as a security measure to secure and control both remote and on-premises access to files and folders offers several benefits to mitigate the risk of ransomware, for superior data protection and uninterrupted business operations.
It is important to note here that to enjoy the following benefits of zero trust data access control, other methods of accessing and sharing of cloud storage and network level on-premises access of organizational storage must be restricted to not allow the zero trust security to be bypassed.
What is the Anatomy of a Ransomware Attack:
Ransomware attacks typically unfold in three distinct stages, each playing a crucial role in the attackers’ objectives:
1. Phase 1: Infiltration and Lateral Movement:
- Ransomware attacks often start with infiltration, commonly through phishing emails or malicious downloads. Once inside the network, attackers aim to gain elevated privileges by planting keylogger software to capture network passwords and credentials. This initial access allows them to move laterally across the organization, seeking out valuable devices and critical information.
2. Phase 2: Information Extraction:
- In the second stage, cybercriminals are in your environment and extract sensitive data from compromised systems. This extraction is vital to a successful ransomware attack, as it provides leverage for extortion. In order to help intruders from being immediately detected, the extraction takes place slowly over a long period of time. Attackers threaten to release the stolen information unless a ransom is paid. Without the extracted data, organizations could potentially restore their systems from backups and mitigate the impact of the attack.
3. Phase 3: Encryption and Extortion:
- In the final stage, ransomware encrypts system access, rendering critical files and systems inaccessible. The attackers then demand a ransom payment in exchange for the decryption key. This phase aims to exploit the urgency and potential irreversibility of the encrypted state, compelling organizations to comply with the ransom demands.
How Organizations Can Reduce Ransomware Risk with ZTDA:

1. Uses Zero Trust Based Access Controls:
- ZTDA establishes granular access controls that limit user access to only the necessary data and systems. By implementing ZTDA, organizations significantly reduce the attack surface, making it harder for cybercriminals to infiltrate networks and move laterally across systems.
2. Minimizes Lateral Movement:
- ZTDA enforces strict micro-segmentation, limiting the lateral movement of attackers within the network. By compartmentalizing data access and implementing zero trust based controls, ZTDA prevents the rapid spread of ransomware and restricts attackers’ ability to reach critical systems.
3. Detects Data Extraction via Activity Monitoring:
- ZTDA solutions, such as FileFlex, offer robust activity tracking capabilities. These systems monitor data activity, including both remote and internal network-based file access and movement, detecting the potential extraction of files and folders from your environment during a ransomware attack. By exporting activity logs to a Security Information and Event Management (SIEM) system, organizations gain visibility into anomalous behavior, allowing organizations to detect and investigate the unusual activity, identify the compromised user/credentials, stop the exfiltration of data early and prevent the ransomware attack.
Watch a detailed explanation
In the podinar produced by Canada Podcasts, Ed Dubrovsky CISSP OSCP PMP MBA MSc, COO and managing partner of Cypher and SCS/Cyber Security Program board member for York University explains the anatomy of a ransomware attack and how before attackers lock your systems they steal your information. Ed has extensive experience in managing over 4700 security incidents including ransomware, business email compromise, malicious insiders, extortion, executive protection, threat intelligence, and prevention/mitigation of risk associated with cyber-attacks.
Ed Dubrovsky – Anatomy of a Ransomware Attack – Before Attackers Lock Your Systems They Steal Your Information
Conclusion:
Ransomware attacks continue to pose significant threats to organizations worldwide. By adopting Zero Trust Data Access (ZTDA) as implemented by FileFlex Enterprise, organizations can strengthen their defenses against ransomware attacks at various stages. FileFlex’s access controls, restrictions on lateral movement, and robust activity monitoring enable organizations to detect and prevent ransomware attacks during the critical extraction phase. By implementing ZTDA, organizations help safeguard their valuable data assets, maintain business continuity, and combat the evolving landscape of ransomware threats.
To learn more, check out our other blogs Network Security: The Power of Zero Trust Data Access to Control On-Premises Access to Files and Folders, How Zero Trust Data Access Can Facilitate Secure and Controlled On-Premises Network Access of Files and Folders, Why Your Zero Trust Security Model Must Include Zero Trust Data Access, and How to Reduce the Risk of Ransomware with the Zero Trust Platform of FileFlex Enterprise.
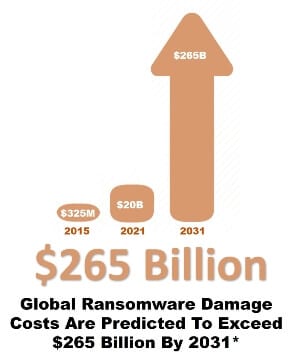
** Cybereason
Learn More About FileFlex Sign Up for a Free Trial