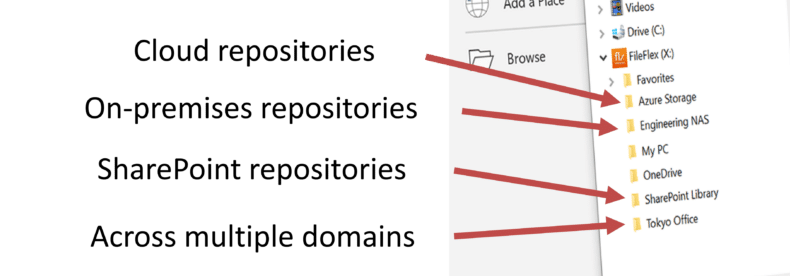
Zero trust security model is a security approach that assumes that every user, whether inside or outside of the organization’s perimeter, is a potential threat. To fully implement a zero trust security model, it is essential to include zero trust data access where only authorized individuals have access to data, and only for the specific purposes for which they are authorized.
Why Your Zero Trust Security Model Must Include Zero Trust Data Access (ZTDA)
Estimated reading time: 3.5 minutes
 In today’s digital world, data is a critical asset, and it needs to be protected against unauthorized access, theft, and other malicious activities. Therefore, when implementing a zero-trust security model, a zero-trust data access approach is a crucial step toward securing sensitive information and maintaining the confidentiality, integrity, and availability of that data.
In today’s digital world, data is a critical asset, and it needs to be protected against unauthorized access, theft, and other malicious activities. Therefore, when implementing a zero-trust security model, a zero-trust data access approach is a crucial step toward securing sensitive information and maintaining the confidentiality, integrity, and availability of that data.
Organizations have started their journey to implementation of a zero trust security model with Zero Trust Network Access (ZTNA) products, but ZTNA addresses only part of organizational needs. Organizations implementing zero trust security also need Zero Trust Data Access (ZTDA).
Both Zero Trust Data Access (ZTDA) and Zero Trust Network Access (ZTNA) are two important concepts in the zero trust security model, which assumes that no user should be automatically trusted and that all requests to access resources must be authenticated and authorized according to policies for each user.
What is Zero Trust Network Access?
Traditionally, network security has been built around the idea of creating a perimeter around a trusted network and allowing users and devices inside that perimeter to access network resources freely. However, this approach has proven to be ineffective against modern security threats, such as advanced persistent threats, malware, and phishing attacks.
ZTNA addresses these challenges by focusing on securing the access of users to network resources, using technologies such as multi-factor authentication, identity and access management (IAM), encryption, and micro-segmentation. It provides granular access control policies that limit access to specific applications and resources, reducing the attack surface and making it harder for attackers to gain access to sensitive data.
Organizations adopt Zero Trust Network Access for its improved security, better compliance, reduced complexity, improved user experience and hedge against obsolesce to stay ahead of evolving security threats.
The Difference Between Zero Trust Network Access and Zero Trust Data Access
Instead of the ZTNA focus on secure access to applications and network resources, ZTDA, focuses on the secure access and sharing of unstructured data within an organization. It assumes that data should not be freely accessed or shared, and uses verification and authentication of users to protect that unstructured data. ZTDA aims to provide granular access control policies that limit access to specific data resources, reduce the risk of data exposure and leakage, and protect sensitive data from unauthorized access and exfiltration. It also provides activity tracking and integration into SIEM platforms to detect malicious behavior and aid in forensic investigation.
Both concepts are important for a comprehensive zero-trust security approach and can work together to provide a more secure and resilient security posture for organizations.
Why Organizations Implementing a Zero Trust Security Model Need to Include Zero Trust Data Access (ZTDA)
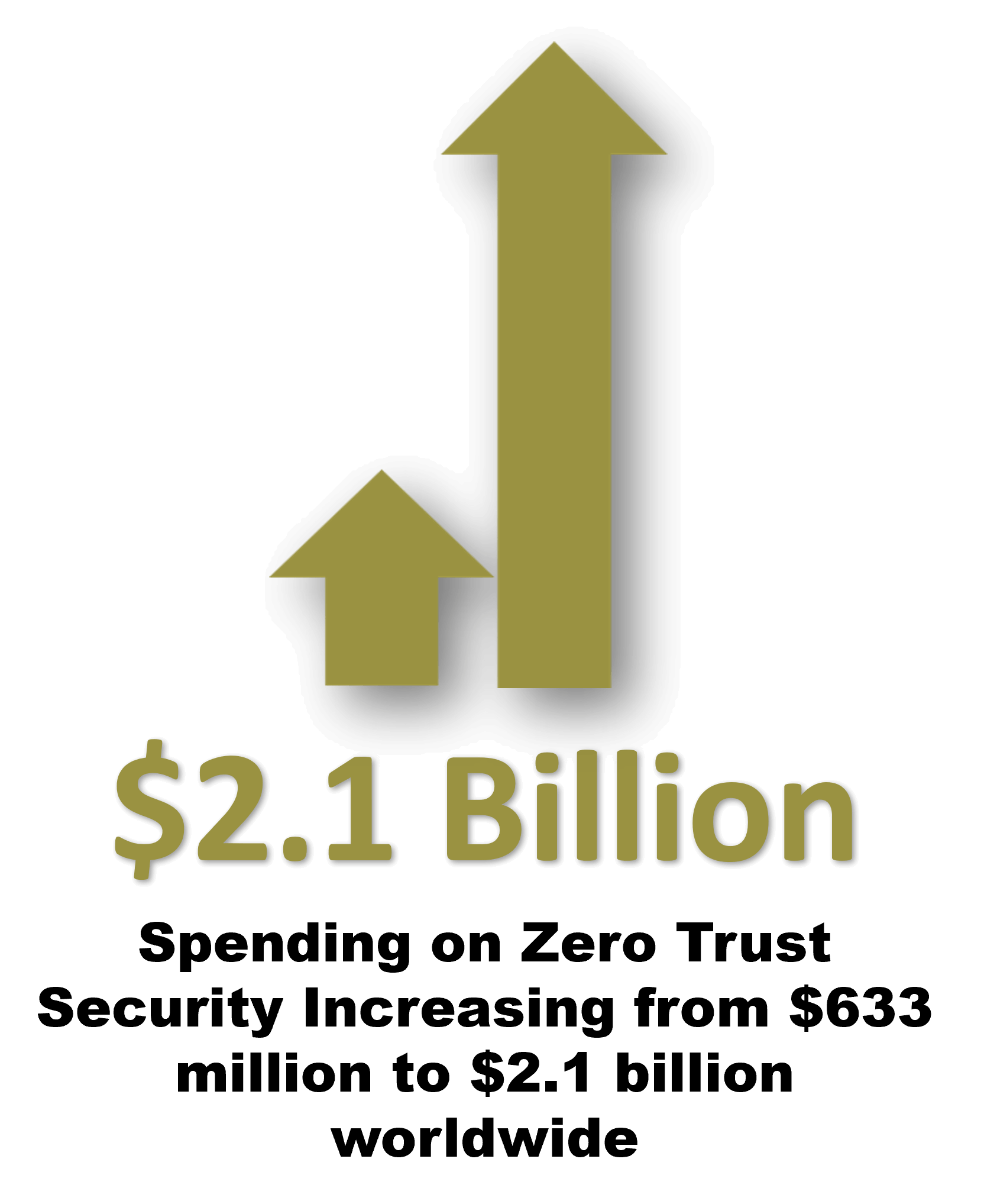 Zero Trust Data Access (ZTDA) is part of a zero trust security model that compliments ZTNA by providing the following key functionality organizations need that ZTNA lacks.
Zero Trust Data Access (ZTDA) is part of a zero trust security model that compliments ZTNA by providing the following key functionality organizations need that ZTNA lacks.
- Secure controlled access to files and folders for authorized users
- Secure controlled file sharing to authorized recipients
- Secure controlled collaboration, virtual data rooms, pdf form fill, and e-signature
- Federation of on-premises, cloud-hosted and SharePoint into Windows and Windows apps
- Activity tracking and integration into SIEM platforms to detect malicious behavior and aid in forensic investigation.
In the Zero Trust Security Model ZTNA and ZTDA Together Replace the VPN
In the zero trust security model, Zero Trust Network Access (ZTNA) together with Zero Trust Data Access have the potential to displace virtual private networks (VPNs) for most users for several reasons:
-
Reduced attack surface:
Unlike VPNs, which provide broad access to the entire network, ZTNA +ZTDA provides granular access control policies and micro-segmentation that limit access to unstructured data, specific applications and resources. This reduces the attack surface and makes it harder for attackers to gain access to sensitive data.
VPNs can be complex and difficult to use, which can lead to frustration and decreased productivity for users. ZTNA provides a simpler and more streamlined approach to network access, with seamless authentication and access to specific applications and resources. ZTDA as implemented by FileFlex Enterprise, is integrated into Windows with no need for a separate app or change in user behavior.
-
Improved security:
VPNs rely on trust in the network perimeter, which can be easily breached by attackers. ZTNA and ZTDA, on the other hand, assume that the organization has already been breached and use verification and authentication of users and devices to protect files, folders and network resources.
-
Greater flexibility:
ZTNA and ZTDA can be implemented in a variety of environments, including cloud-based and hybrid on-premises environments. This provides greater flexibility for organizations that need to support a variety of files, folders, applications and users across different locations and devices.
-
Better compliance:
ZTNA and ZTDA provide granular access control policies and activity tracking of file access and network activity, which can help organizations meet regulatory requirements for data security and access control.
Overall, ZTNA and ZTDA provide a more secure, user-friendly, and flexible approach to unstructured data access and network access, which has the potential to displace VPNs for many users in many network environments.
How FileFlex Enterprise ZTDA Compliments the Zero Trust Security Model
In conclusion, ZTNA and ZTDA – as implemented by FileFlex Enterprise – are two different approaches in a zero-trust security model that address different aspects of secure access to data and applications.
While ZTNA provides secure access to applications and network segments, FileFlex Enterprise provides secure federated access to unstructured data. ZTNA can complement FileFlex Enterprise by providing secure access to the applications that users need to access files and data. Conversely, FileFlex Enterprise can complement ZTNA by providing secure access and sharing of files and data that are stored in applications that are accessed through ZTNA.
Overall, in implementing a zero-trust security model ZTNA and FileFlex Enterprise work together to provide a comprehensive solution for secure, remote access to applications, files, and data.
To learn more, check out our other blogs – What is Zero Trust Data Access (ZTDA)?, Critical Infrastructure Management Over Remote Access and Sharing Using Zero Trust Architecture, Critical Infrastructure Regulatory Compliance via Zero Trust Architectures, Protecting Critical Infrastructure Using Zero Trust Data Access Architecture and How to Protect Your Data with Zero Trust Data Access (ZTDA).
Infographics Source: VentureBeat 2023
Learn More About FileFlex Sign Up for a Free Trial