This brief blog provides an overview of the salient features of Qnext’s FileFlex Enterprise, a commercially available platform that implements ZTDA for enterprise customers.
The FileFlex Enterprise Commercial Platform for Zero Trust Data Access
By Dr. Edward Amoroso, TAG Cyber
Estimated reading time: 3 minutes
Founded in 2016, IT security company Qnext offers the FileFlex Enterprise platform, which supports data access and sharing for enterprise. This commercial, zero trust-based solution is designed specifically to make business processes more effective and secure by supporting sharing and unified access across on-premise, hybrid and cloud infrastructure.
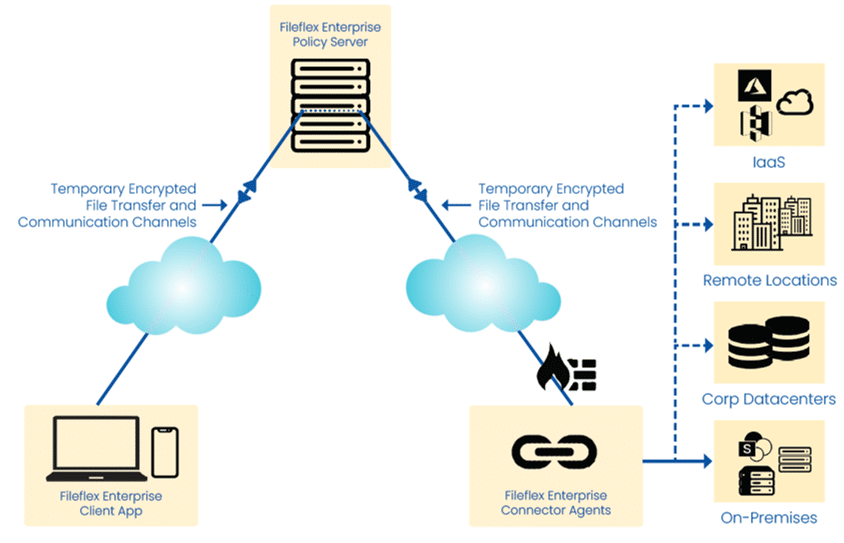
FileFlex Enterprise Architecture
The FileFlex Enterprise solution is designed as an overlay service, built on top of existing data, application and service infrastructure. Thus, the platform’s security, control and functionality operate independently of the details of the underlying network, resulting in portability across environments. FileFlex Enterprise also includes encrypted access to data, thereby enabling secure sharing with the ability to manage permissions at a highly granular level.
One unique aspect of the FileFlex Enterprise platform is its policy-decision point for unstructured data access. This is an important feature for enterprise teams hoping to control both structured and unstructured data, as it is not commonly found in most zero trust network access (ZTNA) and application access (ZTAA) platforms. FileFlex fills this gap for both threat avoidance and compliance reporting.
Zero Trust Support
As suggested above, a primary design goal for FileFlex Enterprise is its focus on zero trust. This reflects the obvious changes in hybrid architectures that allow data to be accessible, shared and used across heterogeneous network environments. This patented platform includes the following specific features that enable zero trust:
- Confidentiality Requirement – Sensitive information is protected from access by unauthorized users and groups.
- Infrastructure Separation – Data is made available to authorized users without having to give them access to infrastructure.
- File Sharing and Transfer – Required tools and capabilities are included to enable sharing and transfer of files and data between users.
- VPN Replacement – Access to data is no longer dependent on the provision of a virtual private network (VPN).
The goal of the FileFlex Enterprise platform is to eliminate unauthorized access to data and services coupled with making access control enforcement as granular as possible. This allows security administrators to match their data access policies up with the objectives of their individual business units.
Resource Access Approach
FileFlex Enterprise also offers support for remote access to resources that might be located on cloud-hosted, on-premise and SharePoint storage and puts them under a single pane of glass. A key aspect of its virtual data security overlay is that users have access to network resources without being on the network infrastructure; this separation helps keep unauthorized users away from network resources.
Access is provided in real-time via the FileFlex Enterprise connector agent, with the security being invisible to the user. This stands in contrast to other solutions that either replicate information to another server to which they have access using enterprise file synchronization and sharing (EFSS) or give direct access to the infrastructure via a VPN or remote desktop software. FileFlex Enterprise abstracts the infrastructure from the data, thereby protecting the organization’s infrastructure from direct and unauthorized access.
File Synchronization
FileFlex Enterprise’s file sync and share (FSS) and EFSS cloud-sharing solutions all provide the ability to share files. The main difference, however, is that cloud-sharing solutions do not have the capability to access the organization’s infrastructure remotely, meaning that organizations need cloud solutions for file sharing and VPNs for remote access.
In addition, FileFlex Enterprise allows for the sharing of any file in the entire hybrid-IT multidomain infrastructure, while cloud solutions can only share files that are duplicated to their servers. That is because cloud solutions are based on a centralized cloud architecture, while FileFlex Enterprise is an overlay built on a zero trust architecture.
Cloud solutions create fragmented separate silos, compromise privacy and require sharing and duplication, thereby increasing the threat surface. They also lack the ability to access and share self-hosted and MS-hosted implementations of SharePoint.
Understanding Zero Trust Data Access
This article is the fourth in a series of 5 from TAG Cyber on Understanding Zero Trust Data Access.
In Article 1, TAG Cyber CEO Dr. Edward Amoroso examines “How To Securely Share Data?”. In the second article, TAG Cyber’s Chris Wilder looked at the risks to unstructured data. In Article 3, TAG Cyber’s Ed Amoroso expands on this theme to outline zero trust access methods and how zero trust data access might work at the file and folder level for customers. Article 5 from TAG Cyber’s Dr. Ed Amoroso proposes an action plan for enterprises in this area.