
FileFlex Zero Trust Data Access brings governance, security and order to the chaos of unstructured data
FileFlex is a Windows overlay service that provides IT-controlled access and sharing of unstructured data across your organization and adheres to the best practices access control principles as outlined in NIST SP-800-171v2 via a zero trust architecture as follows:
FileFlex Enterprise Brings Plug and Play Zero Trust Data Access to Enterprise Data on a Per Transaction Basis

Using our data access policy server, FileFlex Enterprise continually authenticates, verifies and grants or denies access to information on a per transaction basis via an exchange of anonymous secure tokens.

New encryption keys are generated for every session and tokens are available only per session. The use of tokens protects user and device credentials since they are not stored on the FileFlex Enterprise server or with the service provider (MSP).

Direct access to resources is not permitted. All access is via the connector agent which acts as a proxy for the user.
Access and Sharing of Files and Folders According to Dynamic, Granular Policy
- IT admins use the FileFlex Enterprise Management Console to set access and sharing policies that are determined on a user-by-user or group-by-group basis with storage location, folder, or even granular, file-level access.
- Administrators can make selected devices, folders, or files 'view-only' meaning downloading shared content is prohibited, or they can allow access only and prohibit sharing altogether.
Users can also set their sharing options so that downloading of shared content is not permitted. - Unauthorized copying of shared files can be prohibited by both users and administrators to maintain control over the privacy of files shared.
- See Top 6 Reasons You Need Zero Trust File Sharing Management and Top 8 Reasons for Zero Trust Storage Management.
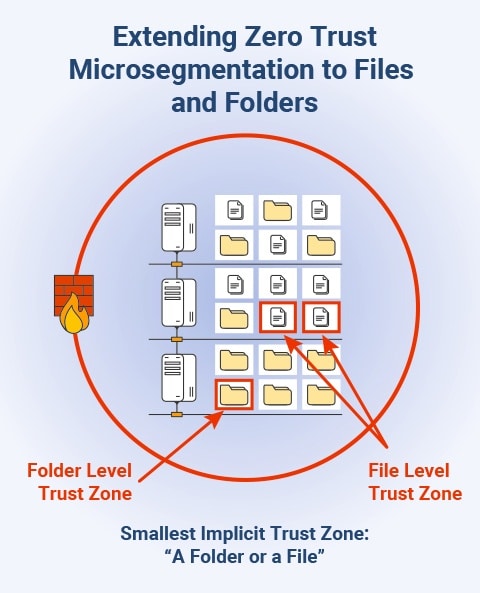
Granular File and Folder Level Microsegmentation
- FileFlex Enterprise provides micro-segmented file and folder level access to prevent lateral movement.
- See Top 5 Reasons Why Zero Trust Micro Segmentation is Important.
No Access to the Infrastructure
- Neither the share recipient nor the FileFlex Enterprise server can access the storage infrastructure. The connector agent fulfills the request, encrypts it, and sends it back to the user thereby abstracting the user from the infrastructure.
- Access to resources is granted only with the least privileges needed to complete the task.
- Read The Top 7 Benefits of Network File Access Control Using Zero Trust Data Access.


All Resource Authentication and Authorization is Dynamic and Strictly Enforced Before Access is Allowed
- FileFlex Enterprise authenticates and verifies all users for all sessions and transactions.
- Prohibits sharing to unauthenticated users. Sharing is done and consumed in the app using patented technology to authenticate users and does not permit open links that can be forwarded or shared on social media providing organizations control over shared files.
- Restricts administrator access where even administrators cannot use FileFlex Enterprise to access any restricted information beyond what their permission levels permit. Also, all administrator activities are logged.
- See Why Zero Trust Data Access User Management is Crucial for IT.
- And Top 8 Reasons for Zero Trust Storage Management.
FileFlex Enterprise Considers All Data Sources and Computing Devices as Resources
- For organizations pursuing a zero trust infrastructure deployment, FileFlex Enterprise isolates and protects remote access to the crown jewel of any organization – its data. Remote data access is the missing piece of zero trust solutions today.
- Protects company information when accessed both from company-owned devices and even when accessed via today's bring your own device (BYOD) use of smartphones, tablets, and computers privately owned by users.
- See Top 11 Ways Zero Trust Data Access Helps Address the Problems Created by the Proliferation of Unstructured Data.

Secures All Communications Regardless of Network Location
- FileFlex Enterprise protects information when accessed over the Internet using a gated AES encrypted hybrid point-to-point system regardless of whether it is located on-premises or on cloud-based assets that are not located on the enterprise-owned network.
- No files are stored on the FileFlex Enterprise server, reducing the organization's threat surface.
- Encryption keys can either be generated in the included PKI server or they can be generated in the secure SGX enclaves of an Intel processor. This protects data transmission even on a system compromised by malware.
- Optional double encryption ensures that the transmitted data is encrypted from sender to receiver (P2P) addressing threats such as man-in-the-middle; snooping and intercept.
- Read Using Zero Trust Architecture (ZTA) to Protect Remote Data Access.
Detailed Activity Logging
- Monitors data access and sharing across all storage locations and logs all user and administrator activities – even for in-app activities via public clouds – for audit and regulatory compliance issues.
- The activity log can be imported to the most popular risk management and SIEM systems using common import protocols.
- See Top 8 Reasons Your Organization Needs Zero Trust Activity Tracking.
Employ Best Practices Compliance Across Your Enterprise

GDPR Compliance
FileFlex Enterprise provides secure file access, sharing and collaboration which supports and augments an organization's GDPR compliance endeavors… More

HIPAA Compliance
FileFlex Enterprise is the ideal file
sharing and collaboration tool for HIPAA Covered Entities and HIPAA Business Associates… More

NIST Compliance
FileFlex Enterprise supports the published best “Access Control” practices for data access outlined in NIST SP-800-171v2… More

CMMC Compliance
FileFlex Enterprise supports the published best “Access Control” practices for data access outlined in the Department of Defense's Cybersecurity Maturity Model Certification… More

FFIEC Compliance
FFIEC guidelines require financial institutions to implement robust cybersecurity frameworks such as Zero Trust Data Access More

Aids FedRAMP
FedRAMP Compliance is enhanced with Zero Trust Data Access for secure remote access and sharing of unstructured data stored in FedRAMP-authorized data centers. More

GLBA Compliance
GLBA compliance is strengthened through Zero Trust Data Access, which enhances data security, minimizes insider threats, and ensures the auditing of sensitive information in financial institutions. More

DORA Compliance
DORA compliance for file sharing, access and collaboration necessitates the implementation of Zero Trust Data Access (ZTDA). More

Local Privacy Regulations
ZTDA aids local privacy regulation compliance in protecting personal data. More

Critical Infrastructure Regulatory Compliance
Critical infrastructure regulatory compliance in regard to protecting access to unstructured data can be greatly enhanced through the use of zero-trust architectures. More

CCPA/CPRA
California Privacy and Cybersecurity Standards necessitate the implementation of Zero Trust Data Access (ZTDA. More
And That's Not All… FileFlex Enterprise Software Gives you ZTDA and all the Security Features You Expect.
Active Directory and LDAP Integration
- Supports integration with Lightweight Directory Access Protocol (LDAP) and Active Directory (AD) and Azure AD.
- When a new user is added, they can automatically only access storage as allowed by Active Directory and device permissions.
- When a user is deleted from AD, they instantly lose access to any storage through FileFlex Enterprise, and all their file sharing is turned off reducing risks associated with timing delays or human error caused by having to manage the deletion as two separate actions in two separate systems.
Support for Single Sign-On (SSO) (SAML)
- Supports SSO and SAML (Security Assertion Markup Language) open standard as well as the following custom versions from the following providers: OneLogin; Google; Microsoft Azure; HelloID; MiniOrange; Okta, TraitWare, Ping Federate and ForgeRock.
User Authentication of Shared Files
- Sharing to unauthenticated users is prohibited. Sharing is done and consumed in the app using patented technology to authenticate users and does not permit open links that can be forwarded or shared on social media providing organizations control over shared files.
Device Authentication
- Device authentication ensures that only authorized devices can use FileFlex Enterprise.
When used with login credentials can be used as an unobtrusive type of two-factor authentication. - Helps protect against phishing as credentials are only accepted when sent in conjunction with the device fingerprint.
Support for Multi-Factor Authentication and U2F Devices
- Strong two-factor authentication and easy-to-use U2F device support using public key crypto that protects against phishing, session hijacking, man-in-the-middle, and malware attacks.
Protection of Credentials
- To protect user and device credentials, FileFlex Enterprise uses an exchange of anonymous secure tokens for every request.
- FileFlex generates new encryption keys every session and tokens are available only per session. The use of tokens protects user and device credentials since they are not
stored on the FileFlex Enterprise server, the service provider, or with Qnext.
Restricted Administrator Access
- Even administrators cannot use FileFlex Enterprise to access any restricted information beyond what their own permission levels permit. Administrator activities are logged.
Secure, View-Only Option – Downloading Prohibited
- Administrators can make selected files, folders, or devices 'view-only' with downloading of shared content prohibited or they can allow access only and prohibit sharing altogether.
- Users can also set their sharing options so that downloading of shared content is not permitted.
- Unauthorized copying of shared files can be prohibited to maintain control over the privacy of files shared.






























