
Unstructured data management presents modern organizations with many complex challenges, as its exponential growth across on-premises, cloud-based and SharePoint locations strains IT management’s ability to ensure security, compliance, and operational efficiency. Implementing a Zero Trust Data Access approach offers a strategic solution to navigate this complex landscape by enforcing secure, controlled access, sharing and governance regardless of disparate and chaotic unstructured data and storage locales.
Top 11 Ways Zero Trust Data Access Aids Unstructured Data Management
Estimated reading time: 6 minutes
Table of Contents
The Proliferation of Unstructured Data
Modern organizations struggle with the complexities of their storage infrastructure, which houses an overwhelming volume of data. According to IDC’s projections, the global data volume is anticipated to reach a staggering 175 zettabytes by 2025, with a significant 80% of this data being unstructured. This unstructured data, represented by files and folders, is spread across a multitude of locations such as on-premises servers, server-attached devices, network-attached resources, and individual PC storages. Further, this now extends into cloud-hosted solutions provided by Microsoft, Amazon, and Google. It can also be stored in self-hosted or Microsoft-hosted implementations of SharePoint. It is compounded by the fact that these data repositories are distributed across multiple domains and geographical locations on a global scale.
What are the Challenges of Unstructured Data Proliferation?
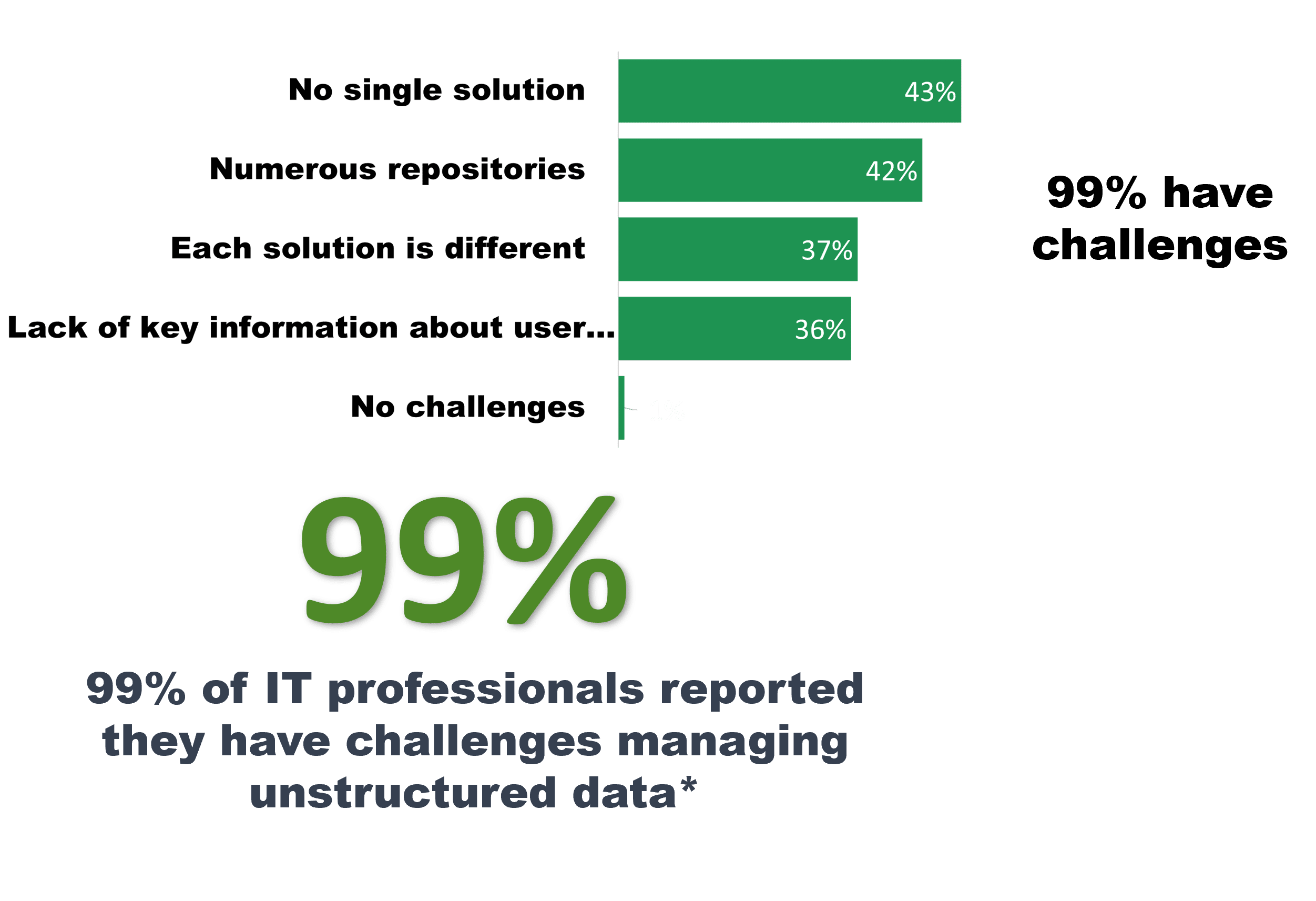 Given this difficult scenario, it’s hardly surprising that an overwhelming 99% of IT security experts encounter challenges in effectively governing and managing unstructured data. The sheer enormity and variation of unstructured data sources present complex problems across security, productivity, and data governance.
Given this difficult scenario, it’s hardly surprising that an overwhelming 99% of IT security experts encounter challenges in effectively governing and managing unstructured data. The sheer enormity and variation of unstructured data sources present complex problems across security, productivity, and data governance.
With unstructured data spanning thousands of devices across many domains and utilizing numerous access methods, it has now materialized into a critical challenge that demands attention from the perspectives of security fortification, operational efficiency, and maintaining healthy data governance protocols.
IT Problems Over Unstructured Data Management
The proliferation of unstructured data poses several significant problems for IT management. These problems include:
Complex Storage Infrastructure:
-
-
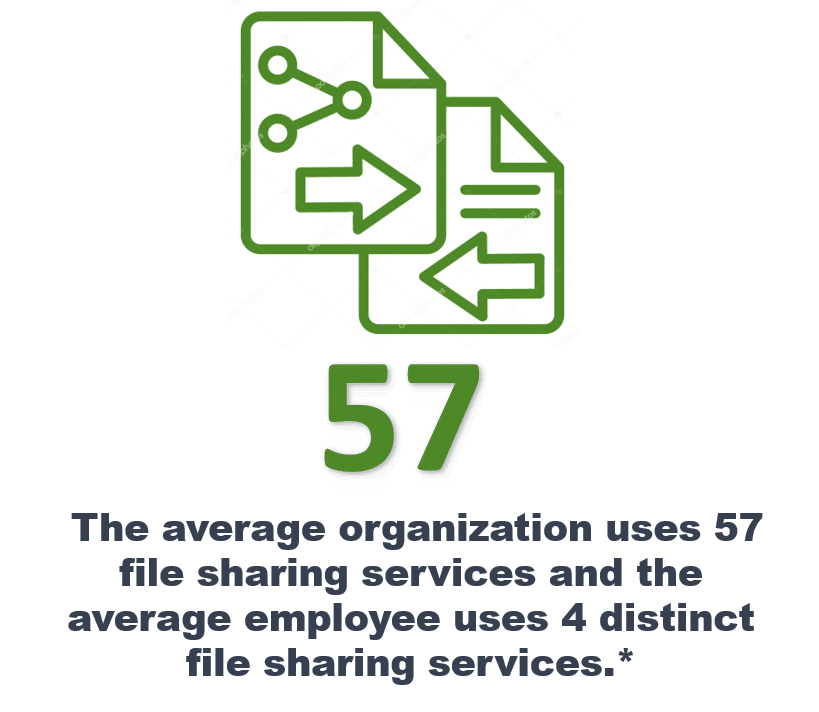
-
Complex Workforce Access:
-
-
- Not only is unstructured data scattered across the organization, but it also needs to be accessed and shared by employees, contractors, gig-workers, partners and external parties by PCs, tablets, phones and multiple operating systems using multiple services and applications.
-
Data Security Risks:
-
-
- Unstructured data’s diverse distribution increases the surface area for potential security breaches. IT managers must implement robust security measures to safeguard data across numerous locations and access points, addressing concerns such as unauthorized access, data leakage, and compliance violations.
-
Inefficient Data Governance:
-
-
- The decentralized nature of unstructured data complicates data governance efforts. IT managers struggle to maintain consistent data quality, enforce access controls, and ensure compliance with regulations across disparate storage locations and platforms.
-
Operational Inefficiencies:
-
-
- The fragmented nature of unstructured data storage leads to operational inefficiencies. IT managers face difficulties in locating, organizing, and retrieving relevant data. This hampers productivity and increases the time and effort required to manage data effectively.
-
Resource Allocation Challenges:
-
-
- Managing unstructured data demands significant IT resources, including storage space, processing power, and network bandwidth. IT managers must allocate resources judiciously to ensure optimal performance across various data sources and access methods.
-
Integration and Migration Difficulties:
-
-
- Integrating new technologies or migrating data becomes intricate due to the heterogeneous nature of unstructured data storage. IT managers must navigate compatibility issues and data transformation challenges when moving or upgrading systems.
-
Compliance and Regulatory Concerns:
-
-
- Different data repositories may be subject to varying compliance requirements and regulations. IT managers must ensure that data across all locations adhere to relevant standards, necessitating thorough monitoring and reporting mechanisms.
-
Monitoring and Auditing Challenges:
-
-
- Monitoring and auditing unstructured data distributed across multiple sources poses difficulties. IT managers need comprehensive monitoring tools to track data access, changes, and usage patterns across the diverse decentralized landscape.
-
Data Access and Collaboration Barriers:
-
-
- Inconsistent access methods and fragmented data repositories hinder collaboration among teams. IT managers need to implement solutions that facilitate secure data sharing and collaboration while ensuring proper access controls.
-
Scalability and Performance Concerns:
-
-
- As unstructured data continues to grow, scalability and performance become concerns. IT managers must plan for scaling the infrastructure, ensuring that storage, processing, and networking resources can handle increasing data volumes effectively.
-
Vendor Management Complexity:
- Dealing with various vendors for different storage solutions introduces vendor management complexities. IT managers need to manage relationships, contracts, and multiple support processes.
Increased Risk of Ransomware:
-
-
- According to Gartner, ransomware is primarily a data access issue as the primary vector for ransomware is unstructured data. The cost of ransomware is not just in payments to the hackers but in investigation, recovery, fines, and credit remediation.
-
In essence, the proliferation of unstructured data presents a multifaceted challenge for IT management, requiring thoughtful strategies, technology solutions, and meticulous planning to overcome the problems associated with this decentralized and diverse data landscape.
Top 11 Ways Zero Trust Data Access Aids Unstructured Data Management
Zero Trust Data Access, as implemented by FileFlex Enterprise is a security framework and approach that can help address many of the problems associated with the proliferation of unstructured data. It focuses on ensuring secure and controlled access and sharing of unstructured data regardless of its location, and it aligns well with the challenges faced by IT management in managing and securing diverse decentralized data repositories. Here’s how FileFlex’s Zero Trust Data Access solution can help mitigate the problems of managing unstructured data:
1. Enhances Security:
-
-
- Zero Trust Data Access requires verifying the identity of users and devices before granting access to data. This helps prevent unauthorized access and reduces the risk of data breaches, addressing the security risks associated with dispersed data.
-
2. Expands Data Governance:
-
-
- Zero Trust Data Access enforces granular access controls and policies based on user roles and permissions. IT managers can define and enforce data access policies consistently across various data sources, promoting effective data governance.
-
3. Delivers Ease and Unification of Access and Sharing:
-
-
- By providing a unified access and sharing control solution federated across on-premises, cloud-hosted and SharePoint storage in Windows, Zero Trust Data Access as implemented by FileFlex simplifies and unifies access and sharing management across diverse data repositories. IT managers can centrally manage access and sharing permissions, reducing the administrative burden and improving operational efficiency.
-
4. Improves Data Visibility and Control:
-
-
- Zero Trust Data Access as implemented by FileFlex produces a detailed activity log over all access and sharing activities of unstructured data. When imported into the SIEM this offers visibility into data access and sharing patterns, allowing IT managers to monitor user behavior and detect unusual activities. This helps identify potential security threats and ensures that data is accessed only by authorized individuals.
-
5. Reduces Complexity:
-
-
- Zero Trust streamlines access management by providing a unified approach to authentication, authorization, and access control. IT managers can simplify their access management strategies, reducing complexity in managing diverse access methods.
-
6. Provides Auditing and Compliance:
-
-
- The FileFlex Zero Trust Data Access platform includes an activity log that can be used with the organization’s SIEM for auditing and reporting capabilities to help IT managers track data access and maintain compliance with regulations. This addresses the challenge of monitoring and auditing access across different data repositories.
-
7. Enables Secure Collaboration:
-
-
- Zero Trust Data Access enables secure data sharing and collaboration by implementing access controls based on user roles and needs. This facilitates teamwork while ensuring data security.
-
8. Reduces Infrastructure Load:
-
-
- Zero Trust Data Access can scale to accommodate the growing volume of unstructured data and diverse storage locations. IT managers can implement a consistent access control framework that adapts to changing data requirements. Since it allows sharing from a centralized location it reduces the need to make copies for sharing and decreases the requirement to scale infrastructure, storage and bandwidth.
-
9. Simplifies Vendor Management:
-
-
- Zero Trust Data Access can be used for access and sharing across various storage platforms, providing a consistent access and sharing security approach regardless of the data storage solution. This simplifies vendor management complexities and allows for the reduction of sharing and VPN platforms.
-
10. Improves User Experience:
-
-
- While prioritizing security, by federating storage and integrating into Windows, Zero Trust Data Access as implemented by FileFlex provides a seamless and user-friendly experience that is part of their already established workflows, ensuring that legitimate users can access data efficiently.
-
11. Reduces Risk of Ransomware:
-
-
- Zero Trust Data Access (ZTDA) as implemented by FileFlex Enterprise, provides a powerful defense against ransomware attacks, focusing on mitigating risks at multiple stages of the attack lifecycle. It achieves this via its zero trust-based access controls, minimizing lateral movement, and detecting data extraction and activity monitoring. (See The Power of Zero Trust Data Access (ZTDA) in Reducing Ransomware Risk)
-
Summary – Essential Unstructured Data Management via a Zero Trust Approach
In summary, adopting a Zero Trust Data Access approach as implemented by FileFlex Enterprise can help IT address the challenges of unstructured data. By prioritizing security, visibility, and consistent access control, organizations can mitigate risks, enhance operational efficiency, and maintain robust data governance across their diverse data landscape turning the chaos of unstructured data into an opportunity for enhanced efficiency and protection. For more information about Zero Trust Data Access see What is Zero Trust Data Access (ZTDA)?
Learn More About FileFlex Sign Up for a Free Trial