Zero Trust Data Access ensures secure CUI collaboration under CMMC
CMMC mandates granular protection of Controlled Unclassified Information. ZTDA adds continuous authentication, file-level permissions, and audit trails on top of compliant infrastructure—helping organizations safely share and collaborate without vulnerabilities.
Zero Trust Data Access for CMMC Compliance
Estimated reading time: 9 minutes
Table of Contents
-
- What is CMMC?
- What are the CMMC Requirements for User Access, Sharing and Collaboration?
- Using Zero Trust Data Access for CMMC Compliance
- Why a Zero Trust Architecture Matters for CMMC Compliance
- How Zero Trust Data Access Contributes to CMMC Compliance
- How Zero Trust Data Access Goes Beyond Mere CMMC Compliance
- Use Cases for Zero Trust Data Access in the CMMC-Compliant Financial Institution
- The Role of Zero Trust Data Access CMMC Compliance and the Safeguarding CUI Unstructured Data
What is CMMC?
CMMC stands for Cybersecurity Maturity Model Certification. It is an assessment framework and certification program developed by the U.S. Department of Defense (DoD) to enhance the cybersecurity posture of the Defense Industrial Base (DIB). The CMMC program is designed to ensure that DIB contractors protect sensitive unclassified information, including Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), that is shared with them by the Department.
The CMMC 2.0 program, which is the latest iteration, streamlines cybersecurity requirements into three levels of certification, aligning each level with well-known and widely accepted NIST cybersecurity standards. The key features of the CMMC 2.0 program include:
- A tiered model that requires companies to implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information.
- An assessment requirement that allows the Department to verify the implementation of clear cybersecurity standards.
- Implementation through contracts, meaning that certain DoD contractors handling sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
The CMMC model is part of the DoD’s efforts to safeguard national security information against frequent and complex cyberattacks.
What are the CMMC Requirements for User Access, File Sharing and Collaboration of Unstructured Data?
The CMMC (Cybersecurity Maturity Model Certification) requirements for user access, file sharing, and collaboration of unstructured data are designed to protect Controlled Unclassified Information (CUI) within the Defense Industrial Base (DIB). These requirements are part of a broader set of cybersecurity practices that contractors must implement to achieve CMMC certification. Here are some key practices related to user access and data collaboration:
-
Limit System Access:
-
-
- Only authorized users, processes, or devices should have access to information systems, especially those containing CUI.
-
-
Control Transaction Types:
-
-
- Authorized users should be limited to the types of transactions and functions they are permitted to execute.
-
-
Verify External Connections:
-
-
- Connections to and use of external information systems must be verified and controlled to prevent unauthorized access.
-
-
Wireless Device Authorization:
-
-
- Devices connecting wirelessly, including mobile devices, must be authorized and use encrypted connections.
-
-
Limit External Data Storage and Processing:
These practices are part of the Access Control domain, one of the 17 domains categorized in the CMMC framework. The framework outlines specific practices and processes that contractors need to follow to protect CUI and achieve the required level of certification. Companies need to understand these requirements and how they apply to their specific assets and data management strategies.
Using Zero Trust Data Access for CMMC Compliance for Unstructured Data
Zero Trust Data Access (ZTDA) emerges as a valuable tool for defense contractors striving for CMMC compliance, particularly in handling CUI unstructured data (documents and files) within intra or inter-company communications. (It is not a solution for structured data.)
In the exchange of CUI documents, ZTDA aligns with common industry practices to ensure a tailored security strategy for unstructured data and effectively addresses the unique security requirements of CMMC, thereby enhancing overall compliance efforts while mitigating potential risks.
Implementing a Zero Trust Data Access can significantly aid in meeting compliance requirements outlined in the Cybersecurity Maturity Model Certification (CMMC) by enhancing the security and resilience of contractor’s IT systems and operations. Zero Trust is a cybersecurity model centered on the principle of not automatically trusting any user or device inside or outside a network. Users must be verified, and specific access requests must be authorized before granting access.
For more information on the Access Control Requirements of CMMC and how Zero Trust can be used to meet those requirements see How to Use Zero Trust to Meet CMMC Access Control Practices for Remote Data Access.
Why a Zero Trust Architecture Matters for CMMC Compliance
Implementing a Zero Trust Architecture (ZTA) is crucial for meeting CMMC compliance standards. This architectural framework aligns closely with the principles outlined in NIST SP-800-171v2, specifically emphasizing zero trust access control. (See How to Meet NIST Guidelines for Zero Trust for Remote Data Access.)
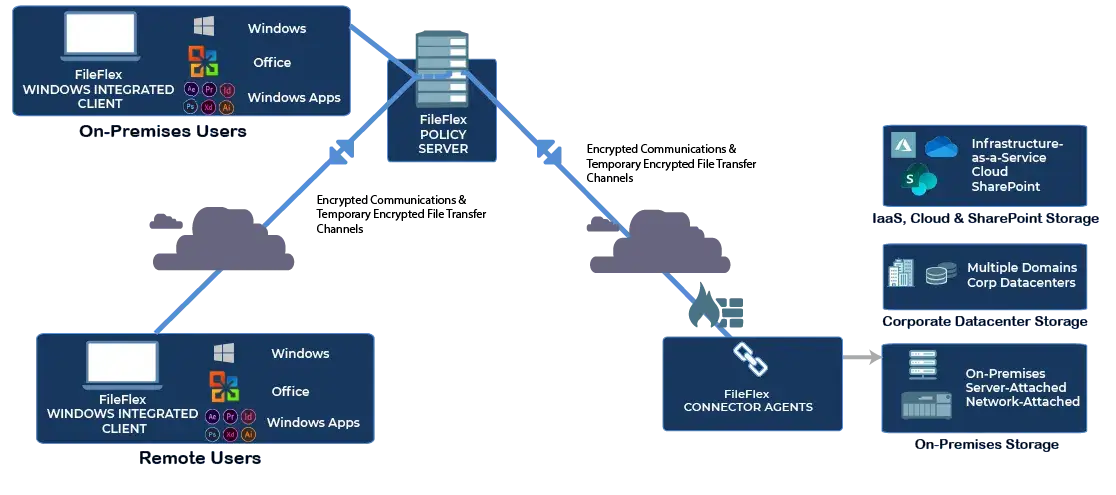
Within this framework, a central server plays a critical role in verifying user identities and permissions. Instead of allowing direct shared access to the original resource location, the server facilitates the delivery of requested files to users. This approach is visualized in Diagram 1, illustrating a simplified zero-trust architecture.
Simplified Zero Trust Architecture for CMMC Compliance
This method enables seamless access, sharing, collaboration, and management of files and folders across various repositories—be it cloud-based, FTP, SharePoint, or on-premises storage. Notably, there’s no need for the zero trust policy server to be managed by a third party, and sensitive information remains secure without requiring uploads to an external server.
Management retains detailed control over access and restrictions, aligning with the principle of Least Privilege and the established IT hierarchy. Additionally, by centralizing all actions through the zero-trust server, comprehensive records of activities are maintained, aiding forensic investigations and for output to the SIEM to detect ransomware attacks in progress (see How to Reduce Ransomware Risk Using Zero Trust Data Access).
Implementing zero trust principles via a ZTA is the key to achieving CMMC compliance regarding secure access, sharing, and collaboration of CUI.
How Zero Trust Data Access Contributes to CMMC Compliance
Here’s how Zero Trust Data Access as implemented by FileFlex Enterprise can contribute to CMMC requirements over access, sharing and collaboration of CUI files and folders:
-
Limits System Access:
Only authorized users, processes, or devices should have access to information systems, especially those containing CUI.
Zero Trust Data Access as implemented by FileFlex Enterprise can be used to only allow authorized users and devices access to information systems containing CUI.
-
Controls Transaction Types:
Authorized users should be limited to the types of transactions and functions they are permitted to execute.
Zero Trust Data Access as implemented by FileFlex addresses the requirement to control transaction types by limiting the data transaction type or actions permitted for authorized users, such as read-only, download/copy access, delete, modify, share, and edit. IT can also set entire storage repositories to view-only, sharing prohibited, editing prohibited, and uploading prohibited.
-
Verifies External Connections:
Connections to and use of external information systems must be verified and controlled to prevent unauthorized access.
FileFlex addresses this requirement by only allowing connections from authorized FileFlex servers. All external connections are performed on secure and controlled communication channels to and from the secured FileFlex server. All other communication channels are denied.
-
Provides Wireless Device Authorization:
Devices connecting wirelessly, including mobile devices, must be authorized and use encrypted connections.
FileFlex addresses the requirement for wireless device authorization via its device control feature. This feature allows IT to formally authorize or remove any device from the secure device list. Communication is rejected from any devices not on the secure device list. All communication and authentications are performed on fully encrypted channels.
-
Limits External Data Storage and Processing:
External connections, storage, and processing of CUI must be limited to ensure security.
FileFlex addresses the CMMC requirement to limit external data storage by limiting external storage/copy/download of data through policy definitions and by enabling remote access, sharing and collaboration of on-premises data storage to limit external data storage and use of cloud providers as necessary.
How Zero Trust Data Access Goes Beyond Mere CMMC Compliance
Here’s how Zero Trust Data Access as implemented by FileFlex Enterprise goes beyond simply meeting CMMC requirements over access, sharing and collaboration of CUI files and folders:
Provides Granular Access Control:
-
- Zero Trust Data Access emphasizes the principle of least privilege, ensuring that users only have access to the specific resources they need for their roles. This approach helps members of the Defense Industrial Base (DIB) manage user access and limit system access as required by CMMC, reducing the risk of unauthorized access to sensitive data or critical systems.
Delivers Continuous Authentication and Authorization:
-
- Zero Trust Data Access continuously verifies and authenticates users and devices before granting access to resources. All users attempting to access CUI documents must be authenticated and their identities verified before granting any level of access. This ensures that only authorized personnel can view or modify sensitive information.
Brings Least Privilege Access:
-
- Following the principle of least privilege, users should only be granted access to the specific CUI documents and files required to perform their job functions. This minimizes the risk of unauthorized access or accidental exposure of sensitive data.
Supplies Encryption and Data Protection:
-
- Zero Trust Data Access incorporates encryption, double encryption (encrypted data in an encrypted micro-channel), and other data-centric security measures. By encrypting data-in-motion and ensuring that access controls are applied consistently across all data interactions, DIB organizations can better protect information and align with CMMC’s objectives for data security and resilience.
Creates Microsegmentation:
-
- Zero Trust Data Access (ZTDA) focuses on securing access to individual files and folders as the smallest implicit trust zone. By isolating different network access to the file and folder level, organizations can restrict the lateral movement of threats to reduce the threat surface and help prevent them from spreading across the entire network. This strategy helps contain potential breaches and limits the impact of cyber incidents. (See Why You Need Zero Trust Data Access Micro-Segmentation.)
Secures Collaboration and Sharing:
-
- Implementing secure collaboration tools and platforms that support encrypted communication channels and access controls can facilitate safe sharing and collaboration on CUI documents among authorized users while preventing unauthorized access from external or malicious sources.
Delivers Activity Monitoring:
-
- Since all actions must be authenticated and authorized by the zero trust policy server, ZTDA provides detailed activity logs for data access and sharing, enabling IT managers to monitor user behavior, detect anomalies, and identify potential security threats. This enables prompt incident response and adherence to CMMC requirements for incident reporting and response.
By adopting Zero Trust Data Access principles for handling CUI unstructured data, DIB contractors can enhance their overall cybersecurity posture, mitigate risks associated with data breaches or unauthorized access, and demonstrate compliance with the stringent requirements of the CMMC framework.
| CUI Security Requirement (CMMC) | Traditional File Sharing | With ZTDA (FileFlex) |
| Access control | Broad permissions | Least privilege per file/folder |
| Identity verification | Single login | Continuous, contextual verification |
| Change & access logging | Basic system logs | Real-time file-level audit trails |
| Secure collaboration | Cloud-based, data duplication | In-place access w/ policy enforcement |
| CUI data movement | Copies moved around | CUI stays in compliant infrastructure |
Use Cases for Zero Trust Data Access in the CMMC-Compliant Defense Industrial Base (DIB) Organization
Implementing a Zero Trust Data Access as implemented by FileFlex Enterprise aligns with the core principles of cybersecurity, access control, and risk management that are central to CMMC compliance. Adopting this approach can significantly enhance the operational resilience and security posture of DIB entities, ultimately helping them meet CMMC’s requirements for the access and sharing of CUI unstructured data. Some practical use cases for the implementation of Zero Trust Data Access as implemented by FileFlex Enterprise are as follows:
CMMC Compliant VPN Alternative
-
- ZTDA can be used as a CMMC-compliant VPN alternative that delivers cutting-edge security, simplified access management, IT-controlled chain of command, file sharing/collaboration functionality, and with Windows integration, enhanced user experience. See 19 Advantages of the Zero Trust Data Access VPN Alternative.
CMMC Compliant Secure CUI File Sharing
-
- ZTDA provides CMMC-compliant CUI file-sharing that delivers data protection, and efficient sharing of federated storage, simplifies the user experience, enhances data privacy and compliance, and provides exemplary data governance and an IT-controlled chain of command with no duplication or syncing. See Zero Trust Data Access for Secure File-Sharing.
CMMC Compliant FTP Alternative
-
- ZTDA is a CMMC-compliant FTP alternative that offers cutting-edge security, ransomware prevention, regulatory compliance, simplified management, enhanced user experience, and more. Read Zero Trust Data Access as an FTP Alternative.
CMMC Compliant MFT Alternative
-
- ZTDA is a contemporary alternative that addresses the security vulnerabilities of MFT. It offers granular file and folder micro-segmentation, has unique federated storage management, encompasses distinctive granular contractor access and brings an IT-controlled chain of command. For more see, Zero Trust Data Access as a Managed File Transfer Alternative.
CMMC Compliant Zero Trust Content Collaboration
-
- ZTDA can be used as a CMMC-compliant zero trust content collaboration platform that safeguards CUI data through micro-segmentation and stringent access to elevate security, streamline workflows, reduce the risk of ransomware and more, providing a cost-effective, adaptable, and user-friendly solution. See Content Collaboration Using Zero Trust Data Access.
CMMC Compliant Virtual Data Rooms
-
- Delivers CMMC-compliant Zero Trust Virtual Data Rooms that offer superior data security, robust protection against ransomware, superior governance and chain-of-command and comprehensive insider threat prevention, while also ensuring compliance, reducing the attack surface, and providing a cost-effective, future-proof approach. Read Top 13 Reasons to Adopt Zero Trust Secure Virtual Data Rooms.
CMMC Compliant Enhancement for Microsoft 365
-
- Integrating into Microsoft 365 E5, particularly for remote and external users, elevates security posture, reduces the risk of data breaches, enhances regulatory compliance, and mitigates insider threats, ultimately fortifying data protection and access management within the Microsoft ecosystem. See 21 Reasons to Supplement Microsoft 365 E5 Security with Zero Trust Data Access.
CMMC Compliant SharePoint Add-in
-
- As a SharePoint add-in, it delivers robust security, flexible data access, and compliance capabilities, making it indispensable for modern organizations prioritizing data protection and efficient collaboration, particularly for remote and external users. See 19 Reasons Why Zero Trust Data Access is an Essential SharePoint Add-in.
Reduces Your Costs
-
- Zero Trust Data Access technology as implemented by FileFlex reduces your VPN, FTP, MFT, file sharing, content collaboration, virtual data room and cloud storage setup, maintenance and use to dramatically reduce your costs. See How Zero Trust Data Access Cuts Costs in Organizational Operations.
Conclusion: The Role of Zero Trust Data Access CMMC Compliance and the Safeguarding CUI Unstructured Data
In conclusion, Zero Trust Data Access (ZTDA) presents a pivotal solution for defense contractors seeking Cybersecurity Maturity Model Certification (CMMC) compliance, particularly in safeguarding Controlled Unclassified Information (CUI) unstructured data. By aligning with industry practices and bolstering security measures, ZTDA not only enhances overall compliance efforts but also mitigates potential risks, thereby fortifying the cybersecurity posture of the Defense Industrial Base.
For more information on protecting critical infrastructure with Zero Trust Data Access see Critical Infrastructure Regulatory Compliance via Zero Trust Architectures, The Top 8 Protections of Critical Infrastructure Using Zero Trust Data Access Architecture, and Critical Infrastructure Management Over Remote Access and Sharing Using Zero Trust Architecture.
* US Congressional Research Service
Learn More About FileFlex Sign Up for a Free TrialFrequently Asked Questions
What is CMMC and why does it matter for CUI?
CMMC (Cybersecurity Maturity Model Certification) provides a unified standard for securing Controlled Unclassified Information (CUI) in defense supply chains. It requires controls around access, sharing, and logging of sensitive data.
How does ZTDA support CMMC requirements?
ZTDA enforces continuous identity verification, least‑privilege access, real‑time audit logging, and secure file sharing—addressing key CMMC practices for handling CUI.
Can FileFlex be used for CUI collaboration under CMMC?
Yes. FileFlex allows secure sharing and real‑time collaboration without moving CUI from compliant infrastructure, applying file-level policies and detailed tracking to satisfy CMMC controls.
Is ZTDA required for CMMC certification?
ZTDA is not strictly required by CMMC, but it significantly strengthens compliance posture by adding file-level governance and monitoring that exceed baseline requirements.