
Zero Trust cybersecurity for credit unions must go beyond network control.
Zero Trust Data Access (ZTDA), protects sensitive member data at the file level through least-privilege access, identity verification, and continuous activity logging. This approach helps credit unions comply with FFIEC guidelines, reduce breach risk, and modernize cybersecurity without costly infrastructure changes..
Zero Trust Cybersecurity for Credit Unions
Estimated reading time: 6 minutes
Table of Contents
-
-
- Introduction: Navigating Credit Union Cybersecurity Challenges
- What is a Credit Union?
- What is the Difference Between a Credit Union and a Bank?
- What are the Main Credit Union Cyber Security Concerns?
- What is Zero Trust Data (ZTDA) Access Based Cybersecurity?
- Why Credit Union Cybersecurity Needs Zero Trust Data Access Technology
- Use Cases
- Conclusion: Building Member Trust Through Advanced Zero Trust Cybersecurity Measures
-
Introduction: Navigating Credit Union Cybersecurity Challenges
What is a Credit Union?
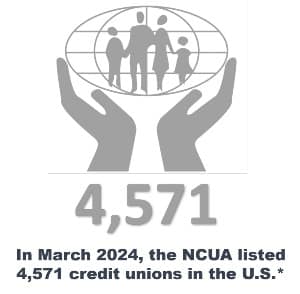
A credit union is a member-owned, nonprofit financial institution that offers banking services like savings accounts, loans, and credit, typically at lower rates and fees than traditional banks. Top credit unions include the Navy Federal Credit Union with 10.5 million members and $170.8 billion in assets and the State Employees Credit Union with 2.7 million members and $54.6 billion in assets.
What is the Difference Between a Credit Union and a Bank?
The top two differences between a credit union and a bank are:
-
Ownership Structure:
- Credit unions are nonprofit organizations owned by their members, while banks are for-profit institutions owned by shareholders.
-
Profit Distribution:
- Credit unions typically return profits to their members through lower fees, better interest rates, and dividends, whereas banks aim to maximize profits for shareholders.
What are the Main Credit Union Cybersecurity Concerns?
-
Data Breaches and Identity Theft:
- Credit unions handle sensitive member data, such as personal and financial information, making them prime targets for data breaches and identity theft through hacking or phishing attacks.
-
Ransomware and Malware Attacks:
- Cybercriminals may use ransomware or malware to disrupt operations or encrypt sensitive data, demanding a ransom to restore access, which can lead to financial losses and reputational damage.
-
Insider Threats:
- Employees or contractors with access to sensitive data or systems may intentionally or unintentionally cause data leaks or system vulnerabilities.
-
Unauthorized or Accidental Sharing of Confidential Information:
- Credit unions are at risk of unauthorized or accidental sharing of unstructured data. This often occurs through improper handling or sharing of sensitive information via email, exposing member data to unintended recipients.
-
Third-Party Vendor Risk:
- Credit unions often rely on third-party service providers, and weaknesses in the security of these vendors can expose the credit union to breaches or cyberattacks.
-
Phishing and Social Engineering:
- Cybercriminals use phishing emails or social engineering tactics to trick employees or members into divulging sensitive information, compromising accounts, or granting unauthorized access.
-
Regulatory Compliance:
- Credit unions must comply with stringent financial and data protection regulations (e.g., GLBA, PCI DSS), and failure to maintain compliance can lead to legal penalties and security vulnerabilities.
-
Distributed Denial-of-Service (DDoS) Attacks:
- These attacks aim to overwhelm a credit union’s network, causing service outages, which can disrupt member access to accounts and services.
What is Zero Trust Data (ZTDA) Access Based Cybersecurity?
Zero Trust Data Access (ZTDA) is a security framework designed to grant access to files and folders only to authenticated and authorized users in a zero-trust environment. Its core principle is to restrict access to data on a need-to-know basis, ensuring that every access request is rigorously authenticated and evaluated against a defined set of rules. ZTDA assumes every access attempt could be malicious, thus preventing unauthorized access and reducing the risk of data breaches. For a more detailed description see What is Zero Trust Data Access (ZTDA)?
Why Credit Unions Need Zero Trust Data Access Cybersecurity
-
-
-
-
-
Enhances Member Trust and Protection:
- Credit unions actively strengthen the security of their members’ sensitive data by enforcing strict access controls, verifying every user and device, and blocking unauthorized access. This commitment directly boosts members’ confidence in the institution’s ability to safeguard their financial information.
-
Protects Reputation:
- By proactively preventing security incidents, credit unions protect their reputations, ensuring that members and the broader community continue to view them as secure and trustworthy. Zero trust helps them avoid breaches that could damage their image and disrupt member relationships.
-
Reduces Operational Costs:
- Credit unions can consolidate file sharing, FTP, MFT and VDR services and reduce the financial risks associated with data breaches, such as legal fees and fines, by preventing unauthorized access and minimizing the damage of any potential breaches. This allows them to maintain low fees and better rates for their members.
-
Improves Compliance:
- Credit unions must meet strict regulatory requirements, such as those under the Gramm-Leach-Bliley Act (GLBA) and PCI DSS, by implementing zero trust technology. They actively demonstrate compliance by ensuring that only verified, authorized users can access sensitive data.
-
Enables Secure Digital Innovation:
- Credit unions support secure access to modern digital services, such as online banking and mobile apps, by using zero trust to monitor and control every interaction. This approach allows them to innovate while keeping member data secure.
-
Enhances Security:
- Zero trust actively verifies every user, device, and network, refusing to trust anything by default—even if it’s within the network perimeter. This method significantly reduces the risk of insider threats and external attacks by ensuring that only authorized users and devices access sensitive member data and financial systems.
-
Improves Protection Against Evolving Threats:
- As cyber threats become more sophisticated, credit unions rely on zero trust to provide adaptive defenses. This technology enables them to detect and respond to advanced threats—such as ransomware, phishing, and insider attacks—more effectively, ensuring robust protection for member data.
-
Minimizes Damage from Breaches:
- In the event of a security breach, zero trust restricts attackers’ movements within the network by segmenting access and requiring re-authentication for every action. This strategy limits the potential impact of a breach by isolating compromised areas and preventing lateral movement within the system.
-
Secures Remote Access:
- With the rise of remote work, zero trust ensures secure remote access to sensitive data and systems. By doing so, it reduces the risk of unauthorized access from compromised devices or insecure networks, safeguarding member information regardless of where employees are working.
-
Reduces the Risk of Data Breaches:
- By continuously monitoring user activity and employing strict access controls, zero trust significantly reduces the risk of data breaches. This proactive approach helps identify unusual behavior early, allowing credit unions to respond swiftly and mitigate potential threats before they escalate.
-
Mitigates the Accidental or Unintentional Sharing of Unstructured Data:
- Zero Trust Data Access ensures that sensitive unstructured data can only be accessed and shared by authorized individuals. This reduces the risk of accidental or unintentional sharing of confidential information, a common issue in email communications and other forms of data transfer.
-
Mitigates Ransomware Threats:
- Zero trust architecture helps credit unions defend against ransomware attacks by limiting access to critical data and applications. By enforcing strict permissions and segmenting the network, even if an attacker gains initial access, they cannot easily spread throughout the network, thus containing the threat.
-
-
-
-
| Feature/Concern | Traditional CU Security | With Zero Trust Data Access (ZTDA) |
| Member data access control | Role-based, broad permissions | Granular, real-time per user/file |
| Compliance readiness | Manual audits | Automated tracking + user-level logs |
| Insider threat containment | Reactive | Preemptive control + visibility |
| Deployment model | Complex, often disruptive | Overlays existing infrastructure |
| Breach impact | Lateral spread possible | Contained to smallest access unit |
Use Cases
In addition to the security, regulatory, member trust and reputational benefits for Credit Unions that implement Zero Trust Data Access, Credit Unions enjoy the following use cases.
Superior Zero Trust File Sharing:
-
-
-
- Credit unions use zero-trust file sharing to ensure that sensitive files are securely shared with authorized users only, continuously verifying identities and permissions throughout the process. See Top 13 Reasons for Secure Zero Trust File Sharing.
-
-
Advanced Zero Trust VPN Alternative:
-
-
-
- Replacing traditional VPNs, Zero Trust Data Access enables secure remote access for credit union employees by validating every access request, reducing the risks associated with compromised devices and networks. See 19 Advantages of the Zero Trust Data Access VPN Alternative.
-
-
Enhanced Zero Trust FTP Alternative:
-
-
-
- Credit unions utilize Zero Trust Data Access as an alternative to traditional FTP. By restricting access and verifying users at every stage, Zero Trust Data Access provides more secure and controlled file transfers. See 24 Reasons to Use Zero Trust Data Access as an FTP Alternative.
-
-
Secure Zero Trust MFT Alternative:
-
-
-
- Implementing zero trust managed file transfer (MFT) ensures secure, automated file transfers with constant monitoring and validation of users, protecting member data from unauthorized access. See Why Organizations Need Zero Trust Data Access as a Managed File Transfer (MFT) Alternative.
-
-
Robust Zero Trust Collaboration:
-
-
-
- Credit unions adopt zero-trust collaboration tools to ensure that only authenticated and authorized users can participate in shared workspaces, keeping member data and communications secure. See Discover the Top 15 Reasons to Adopt Zero Trust Collaboration.
-
-
Protected Zero Trust Virtual Data Rooms:
-
-
-
- Credit unions can leverage zero trust virtual data rooms to create a secure digital space for each individual member. In these member-specific data rooms, confidential documents can be uploaded, reviewed, and signed electronically using platforms like DocuSign. The documents are securely stored for future reference, ensuring that sensitive member information remains protected. This approach offers a more secure alternative to emailing unstructured data, reducing the risk of accidental sharing or unauthorized access, and allowing credit unions to maintain stringent control over sensitive files. See Top 13 Reasons to Adopt Zero Trust Secure Virtual Data Rooms.
-
-
These Zero Trust Data Access use cases provide robust security for credit unions, reducing risks associated with traditional access methods while ensuring compliance with regulatory standards.
Conclusion: Building Member Trust Through Advanced Zero Trust Cybersecurity Measures
In conclusion, by adopting Zero Trust Data Access technology, credit unions can significantly enhance their data protection measures and ensure regulatory compliance, ultimately creating a safer operating environment and strengthening member trust. For a related article see Zero Trust for FFIEC Compliance: Why ZTDA Is the Missing Link, Zero Trust for GLBA Compliance: File-Level Data Protection, DORA Compliance for File Sharing, Access and Collaboration Using Zero Trust Data Access
Learn More About FileFlex Sign Up for a Free TrialFrequently Asked Questions
Why are credit unions adopting Zero Trust?
Credit unions are adopting Zero Trust to protect member data from evolving cyber threats. It offers granular controls and breach containment that traditional perimeter defenses cannot match.
How does ZTDA support credit union cybersecurity?
ZTDA secures sensitive files by enforcing continuous authentication, granular permissions, and real-time monitoring. It ensures only authorized users access data—reducing breach impact.
Does ZTDA help meet FFIEC or GLBA guidelines?
Yes. ZTDA enables access logging, user-level policy enforcement, and data protection—directly supporting FFIEC and GLBA compliance for credit unions.
Can FileFlex integrate into existing CU systems?
Yes. FileFlex overlays existing infrastructure to apply Zero Trust Data Access without replacing core systems—supporting hybrid and on-prem environments.