
Illumio Core is extended with Zero Trust Data Access expanding Illumio’s micro-segmentation and policy enforcement to include data activity for a more comprehensive security solution that adds defense against external infiltration and data extraction to Illumio’s expertise at containing threats on the internal network before they can spread.
Top Reasons to Add Zero Trust Data Access to Illumio Core
Estimated reading time: 7 minutes
Table of Contents
-
-
- Introduction: Elevating Data Protection Using Integration of Illumio Core and Zero Trust Data Access
- Illumio Core: Containing Threats on the Internal Network Before They Can Spread
- Illumio Core Plus Zero Trust Data Access Defends Against External Infiltration and Data Extraction
- Additional Reasons to Add Zero Trust Data Access to Illumio Core
- Additional Use Cases when Zero Trust Data Access is Added to Illumio Core
- Summary: Strengthening Cybersecurity Defenses Through Integration
-
Introduction: Elevating Data Protection Using Integration of Illumio Core and Zero Trust Data Access
 In today’s interconnected digital landscape, integrating cybersecurity solutions plays a pivotal role in strengthening organizational defenses against evolving cyber threats. When Illumio Core is integrated with Zero Trust Data Access capability as implemented by FileFlex Enterprise, a more comprehensive security solution addresses both the prevention and mitigation aspects of cyber threats. Through this integration, organizations can achieve heightened security measures, streamlined workflows, and enhanced data governance, greatly improving their defense against sophisticated cyber-attacks, data breaches and ransomware.
In today’s interconnected digital landscape, integrating cybersecurity solutions plays a pivotal role in strengthening organizational defenses against evolving cyber threats. When Illumio Core is integrated with Zero Trust Data Access capability as implemented by FileFlex Enterprise, a more comprehensive security solution addresses both the prevention and mitigation aspects of cyber threats. Through this integration, organizations can achieve heightened security measures, streamlined workflows, and enhanced data governance, greatly improving their defense against sophisticated cyber-attacks, data breaches and ransomware.
Illumio Core: Containing Threats on the Internal Network Before They Can Spread
Illumio is a cybersecurity company that offers a platform for securing enterprise networks and applications. Their product, called the Illumio Core, provides real-time visibility and control over network traffic, allowing businesses to identify and contain threats before they can spread. The platform uses zero trust-based micro-segmentation to create security policies based on the identity of individual workloads, regardless of their location or the infrastructure they are running on. This approach enables businesses to protect critical data and applications across a variety of environments, including on-premises data centers, cloud environments, and hybrid environments. Additionally, Illumio offers integrations with a range of security and IT tools to streamline workflows and enhance security posture.
Illumio Core is primarily focused on securing enterprise networks and applications through micro-segmentation, real-time visibility, and policy enforcement. This approach allows organizations to protect critical data and applications from lateral movement and zero-day threats.
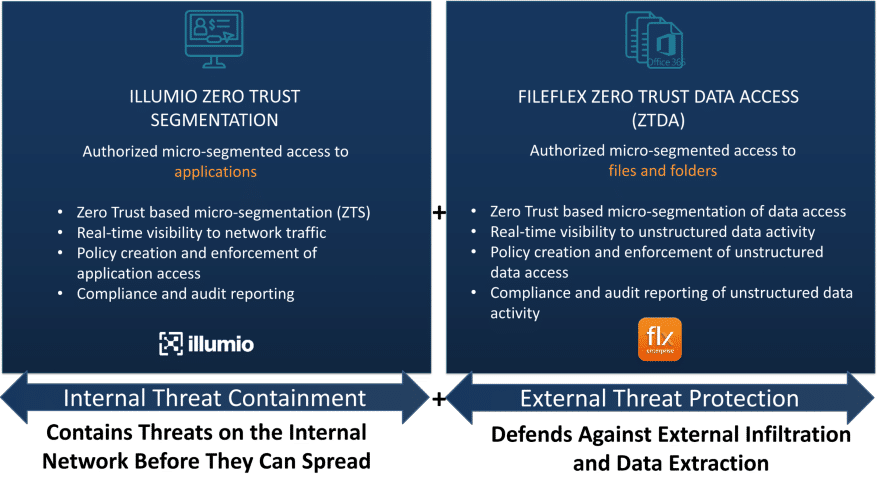
Extending the Illumio Zero Trust Ecosystem to Include Data
Illumio Core Plus Zero Trust Data Access Defends Against External Infiltration and Data Extraction
While Illumio Core and Zero Trust Data Access address different aspects of enterprise security, together they complement each other to provide a more comprehensive security solution. For example, Illumio Core can provide micro-segmentation and policy enforcement to secure the network and applications, while Zero Trust Data Access as implemented by FileFlex Enterprise guards against external threats by expanding that zero trust security to include data and data access.
FileFlex adds the following to Illumio Core:
- Illumio’s zero trust-based micro-segmentation is expanded to include data access
- Illumio’s real-time visibility to network traffic is expanded to include data activity
- Illumio’s policy creation and enforcement is expanded to include data activity
- Illumio’s compliance and audit reporting is expanded to include data activity
Expanding Illumio’s micro-segmentation and policy enforcement to include data activity now offers a broader security solution that addresses both prevention and mitigation aspects of cyber threats. While Illumio Core excels in limiting the extent of damages and exposure as a result of a breach, integration of data activities via Zero Trust Data Access can also help prevent breaches by eliminating common infiltration points utilized by malware and bad actors and detecting ransomware attacks in process during the data extraction phase, before servers are encrypted and ransom demanded – assuming the organization’s environment is properly secured. By combining these solutions, Illumio users achieve greatly improved overall protection and risk mitigation: Illumio Core helps defend internal systems post-breach, while the Zero Trust Data Access architecture of FileFlex Enterprise helps defend against external infiltration, and data extraction. Thus, integration brings a more robust defense against cyber threats.
Additional Reasons to Add Zero Trust Data Access to Illumio Core
Beyond the compelling security benefits, the integration is also a practical complement to Illumio in addressing the problems of unstructured data as follows:
-
Expands Data Governance:
- Zero Trust Data Access adds unstructured data access controls and policies based on user roles and permissions to Illumio Core. IT managers can define and enforce data access policies consistently across various data sources, promoting effective data governance.
-
Delivers Ease and Unification of Access and Sharing:
- By providing a unified access and sharing control solution federated across on-premises, cloud-hosted and SharePoint storage in Windows, Zero Trust Data Access as implemented by FileFlex simplifies and adds the unification of access and sharing management across diverse data repositories to Illumio Core. IT managers can centrally manage access and sharing permissions, reducing the administrative burden and improving operational efficiency.
-
Improves Data Visibility and Control:
- Zero Trust Data Access as implemented by FileFlex produces a detailed activity log over all access and sharing activities of unstructured data. This augments Illumio Core by providing visibility into data access and sharing patterns, allowing IT managers to monitor user behavior and detect unusual activities. This helps identify potential security threats and ensures that data is accessed only by authorized individuals.
-
Reduces Complexity:
- Zero Trust Data Access combined with Illumio Core streamlines access management by providing a unified approach to authentication, authorization, and access control. IT managers can simplify their access management strategies, reducing complexity in managing diverse access methods.
-
Provides Auditing and Compliance:
- The FileFlex Zero Trust Data Access platform includes an activity log that can be used with Illumio Core and the organization’s SIEM for auditing and reporting capabilities to help IT managers track data access and maintain compliance with regulations. This addresses the challenge of monitoring and auditing access across different data repositories.
-
Enables Secure Collaboration:
- Zero Trust Data Access adds secure data sharing and collaboration to Illumio Core by implementing access controls based on user roles and needs. This facilitates teamwork while ensuring data security.
-
Reduces Infrastructure Load:
- Zero Trust Data Access can scale to accommodate the growing volume of unstructured data and diverse storage locations. It can be used with Illumio Core to enable IT managers to implement a consistent access control framework that adapts to changing data requirements. Since Zero Trust Data Access allows sharing from a centralized location it reduces the need to make copies for sharing and decreases the requirement to scale infrastructure, storage, and bandwidth.
-
Simplifies Vendor Management:
- Zero Trust Data Access can be used for access and sharing across various storage platforms and used with Illumio Core to provide a consistent access and sharing security approach regardless of the data storage solution. This synergy simplifies vendor management complexities and allows for the reduction of sharing and VPN platforms.
-
Improves User Experience:
- While prioritizing security, by federating storage and integrating into Windows, Zero Trust Data Access as implemented by FileFlex provides a seamless and user-friendly experience that is part of their already established workflows, ensuring that legitimate users can access data efficiently.
-
Reduces Risk of Data Breach and Ransomware:
- Zero Trust Data Access (ZTDA) combined with Illumio Core, provides a powerful defense against data breach and ransomware attacks, focusing on mitigating risks at multiple stages of the attack lifecycle. It achieves this via its zero trust-based access controls, minimizing lateral movement, and detecting data extraction and activity monitoring.
Additional Use Cases when Zero Trust Data Access is Added to Illumio Core
Beyond these benefits, the integration adds several new use cases beyond enhanced security and expanded IT-controlled chain of command. These include:
Zero Trust VPN Alternative That Includes Unstructured Data Access
The addition of Zero Trust Data Access as implemented by FileFlex Enterprise to Illumio Core provides a zero-trust alternative to the VPN that seamlessly connects users to applications plus all the unstructured data stored on on-premises devices, cloud-hosted platforms, FTP, and SharePoint over the Internet. Access to these unstructured data repositories is federated as a drive in the Windows operating system making it accessible to File Explorer and any Windows app. For more details see Zero Trust Data Access as a VPN Alternative.
Zero Trust Secure File Sharing, FTP and MFT Replacement
Adding Zero Trust Data Access to Illumio Core enables secure file sharing across multiple storage platforms, grants precise permissions control, supports large file sharing, enforces in-app user authentication, tracks sharing activities with email notifications, applies watermarks and redactions, and allows seamless sharing directly from Windows. See Top 13 Reasons to Use Zero Trust Data Access for Secure File-Sharing, 24 Reasons to Use Zero Trust Data Access as an FTP Alternative, and Why Organizations Need Zero Trust Data Access as a Managed File Transfer Alternative.
Zero Trust-Based Content Collaboration
Illumio Core combined with Zero Trust Data access provides a collaboration platform that facilitates remote editing and file replacement directly from original storage locations, supporting various applications like Office 365, Google Docs, AutoCAD, and Adobe Creative Suite, and offering an intuitive workflow, version control, file locking, activity tracking, with no size restrictions for editing files. See Top 15 Reasons for Content Collaboration Using Zero Trust Data Access.
Zero Trust Virtual Data Rooms
Illumio Core plus Zero Trust Data Access as implemented by FileFlex allows end users to create unlimited Virtual Data Rooms located anywhere on on-premises, cloud-hosted, IaaS, or SharePoint storage, with unlimited participants, diverse permission levels, comprehensive activity tracking, and no restrictions on file sizes or storage capacity. See Top 13 Reasons to Adopt Zero Trust Secure Virtual Data Rooms.
Zero Trust SharePoint Add-in
Illumio Core with Zero Trust Data Access enhances self-hosted implementations of SharePoint by enabling secure file sharing and collaboration within Windows, without file size limitations, providing access to multiple accounts, enabling team collaboration with external parties without SharePoint licenses, facilitating Virtual Data Room creation within SharePoint while integrating SharePoint to the rest of the corporate storage infrastructure. See 19 Reasons Why Zero Trust Data Access is an Essential SharePoint Add-in.
Zero Trust Hybrid Storage File Management and Machine-to-Machine Transfer
Illumio Core when extended with Zero Trust Data Access provides end-users extensive file management across diverse storage types with remote operations, activity logging, customizable settings, no file size restrictions, and it enables machine-to-machine transfer capabilities for administrators handling large storage migrations.
Zero Trust Storage Federation with Windows Integration
For end-users, data access is now integrated into Windows at the driver level, federating hybrid storage locations as a local drive to enable sharing, collaboration, file management, and direct access from Windows File Explorer or any Windows program.
Summary: Strengthening Cybersecurity Defenses Through Integration
In today’s dynamic digital environment, integrating cybersecurity solutions is essential for strengthening organizational defenses against evolving cyber threats. By combining Illumio Core with the Zero Trust Data Access capability provided by FileFlex Enterprise, organizations can achieve a more comprehensive security solution that addresses both the prevention and mitigation aspects of cyber threats. This integration enhances security measures and data governance ultimately empowering organizations to effectively safeguard against sophisticated cyber attacks and maintain a more robust security posture in this ever-changing threat landscape.
* Forbes
Learn More About FileFlex Sign Up for a Free Trial