
A complete Zero Trust Security framework requires both Zero Trust Network Access (ZTNA) to control user and device access to networks and apps, and Zero Trust Data Access (ZTDA) to protect sensitive data at the file level. Together, they form a unified strategy to reduce risk and prevent breaches.
How to Build a Complete Zero Trust Security Framework
Estimated reading time: 2 minutes
Table of Contents
-
-
-
-
- Introduction: The Need for a Complete Zero Trust Security Framework
- What Is a Complete Zero Trust Security Framework?
- Why ZTNA Alone Isn’t Enough for a Complete Zero Trust Security Framework
- How ZTDA Completes the Zero Trust Security Framework
- Benefits of a Complete Zero Trust Security Framework
- The Business Impact of a Combined ZTNA and ZTDA Zero Trust Strategy
- Conclusion: A Complete Zero Trust Security Framework
-
-
-
Introduction: The Need for a Complete Zero Trust Security Framework
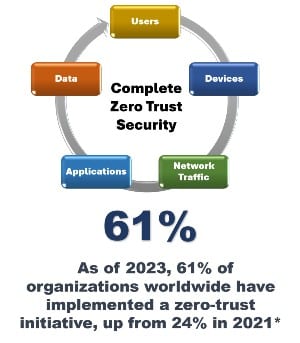
What Is a Complete Zero Trust Security Framework?
A complete Zero Trust Security framework eliminates implicit trust by enforcing continuous verification and least-privilege access at every level—network, application, and data. It requires both ZTNA to secure access and ZTDA to protect sensitive data at the file level.
Why ZTNA Alone Isn’t Enough for a Complete Zero Trust Security Framework
Zero Trust Network Access (ZTNA) replaces traditional network security models, such as VPNs, with an identity-centric approach that enforces least-privilege access. Instead of granting broad network access, ZTNA verifies users, devices, and contexts before allowing access to specific applications or services. It reduces the attack surface, preventing lateral movement by malicious actors.
However, ZTNA primarily focuses on securing access to applications and systems, not on how data is accessed, shared, or protected once inside. This is where Zero Trust Data Access (ZTDA) becomes essential.
How ZTDA Completes the Zero Trust Security Framework
While ZTNA ensures that only authorized users can access applications, it does not govern how those users interact with sensitive data. ZTDA enforces strict data-level security policies, ensuring that only the right users, devices, and processes can access or share specific files—regardless of network location.
ZTDA provides:
- Granular file-level access control beyond application permissions
- Prevention of data exfiltration by unauthorized users or compromised accounts
- Visibility into file interactions for compliance and security monitoring
- Policy enforcement for regulatory requirements such as GDPR, CCPA, and HIPAA
Benefits of a Complete Zero Trust Security Framework
By integrating ZTDA with ZTNA, organizations can establish a complete Zero Trust security framework that covers both network access and data protection. Here’s how they work together:
| Aspect | ZTNA (Zero Trust Network Access) | ZTDA (Zero Trust Data Access) | Complete Zero Trust Security Framework of ZTNA + ZTDA |
| Primary Focus | Secure network access to applications & systems | Secure access to files & data | Extends Zero Trust to data, not just networks |
| Trust Model | Verifies users before granting network/application access | Verifies users & devices before allowing file access | Ensures least privilege extends to data |
| Access Control | Grants access based on identity & device posture | Grants file access based on identity and policies | Prevents overprivileged access to sensitive data |
| Visibility | Tracks user activity at the network/application level | Provides insights into file interactions, sharing & collaboration | Completes the security picture with data-level monitoring |
| Risk Reduction | Reduces attack surface by preventing lateral movement | Prevents unauthorized data access & exfiltration | Stops attackers from accessing sensitive files even if network access is compromised |
| Deployment | Implemented via identity-aware proxies, software-defined perimeters | Enforced via policy-based access to file storage | Works alongside ZTNA to provide end-to-end security |
| Use Case Examples | Secure remote access, VPN replacement, cloud & SaaS security | Secure file sharing, collaboration, VDR, MTF, FTP, compliance, insider threat protection | Ensures Zero Trust applies to data, not just apps |
The Business Impact of a Combined ZTNA and ZTDA Zero Trust Strategy
By combining ZTNA and ZTDA, organizations can significantly reduce risk and enhance security posture. This integrated approach ensures that even if network defenses are breached, sensitive data remains protected through granular access controls and monitoring. Benefits include:
-
- Enhanced Insider Threat Protection: Prevents unauthorized data movement by malicious insiders or compromised credentials.
- Compliance Simplification: Ensures continuous enforcement of data security policies for regulatory standards.
- Improved Incident Response: Enables visibility into data interactions to detect and mitigate breaches faster.
- Reduced Attack Surface: Limits exposure of sensitive data, even within authorized applications.

Conclusion: A Complete Zero Trust Security Framework
ZTNA is a crucial step in securing enterprise networks, but it does not go far enough on its own. ZTDA is the missing link that ensures Zero Trust Security principles extend all the way down to the data itself. By deploying both solutions together, organizations can eliminate implicit trust at every level, from network access to data governance, and achieve a truly resilient security architecture.
As cyber threats continue to evolve, businesses that embrace both ZTNA and ZTDA will be better positioned to safeguard their most valuable asset—their data.
For further reading see How to Enforce Zero Trust Access Control to Mitigate Data Breach and Ransomware, Top Reasons to Add Zero Trust Data Access to Illumio Core, and Why Zero Trust Network Access Combined with Zero Trust Data Access Could Have Prevented the Tesla Breach.
Sign Up for a Free TrialFrequently Asked Questions
What makes a Zero Trust Security framework complete?
A complete Zero Trust Security framework includes both Zero Trust Network Access (ZTNA) to control access to networks and applications, and Zero Trust Data Access (ZTDA) to protect data at the file level. Together, they eliminate implicit trust across the entire environment.
What is the difference between ZTNA and ZTDA?
ZTNA secures network and application access by verifying users and devices before granting permission, while ZTDA focuses on securing sensitive data with file-level access control and continuous verification. Both are essential to achieving a complete Zero Trust strategy.
Why is ZTDA necessary if I already have ZTNA?
ZTNA only protects access to networks and apps, not how users interact with sensitive files once inside. ZTDA adds critical protection by enforcing file-level controls, preventing data exfiltration, and ensuring compliance—even after access is granted.
How do ZTNA and ZTDA work together?
ZTNA verifies identity and context before granting access to network devices/segments and applications, while ZTDA governs how users interact with data within those segments/devices and apps. When combined, they offer a complete Zero Trust Security framework that defends against both external and internal threats.