
Zero Trust Network Access (ZTNA) combined with Zero Trust Data Access (ZTDA) enhances security at both the network and data levels, significantly reducing the risk of data breaches like the one at Tesla.
Why Zero Trust Network Access Combined with Zero Trust Data Access Could Have Prevented the Tesla Breach
Estimated reading time: 3 minutes
Table of Contents
Introduction

Combining Zero Trust Network Access (ZTNA) with FileFlex Enterprise Zero Trust Data Access (ZTDA), these organizations could have established a robust defense system, ensuring that only authorized personnel could access sensitive data through secure, verified channels. Even though the following principles apply to all potential data breaches, let’s look at the recent breach at Tesla in particular and see how this zero-trust combination could have prevented the breach.
What Happened at Tesla
Tesla experienced a data breach that impacted the personal information of over 75,000 employees and 23,000 internal documents that was attributed to two former employees who misappropriated the information and leaked it to the German newspaper Handelsblatt. *
Why a Combined Zero Trust Network Access (ZTNA) and Zero Trust Data Access (ZTDA) FileFlex Enterprise Solution Could Have Prevented the Breach
Combining the Zero Trust Data Access (ZTDA) technology of FileFlex Enterprise with a Zero Trust Network Access (ZTNA) platform could have provided a robust defense against the Tesla data breach. The Zero Trust Network Access platform would be used to isolate the sensitive data repositories and allow authorized personnel access only through the Zero Trust Data Access ability of FileFlex Enterprise.
Here’s a detailed approach to how these tools could be used to prevent a data breach similar to the one at Tesla:
Key Components of the Solution
-
Zero Trust Network Access (ZTNA) Platforms:
- Identity and Access Management (IAM): Enforces strict user authentication and authorization.
- Device Posture Assessment: Ensures that only compliant and secure devices can access the network.
- Granular Access Control: Allows for detailed access policies based on user roles, device status, and contextual factors.
- Continuous Monitoring and Logging: Provides real-time monitoring and detailed logging of access attempts.
-
FileFlex Enterprise Zero Trust Data Access:
- Data-Centric Security: Implements Zero Trust principles at the data level, verifying every access request.
- Encryption and Secure Access: Ensures all data access and transfers are encrypted.
- Detailed Auditing and Reporting: Monitors and logs all data access activities to detect malicious movement and later forensic analysis.
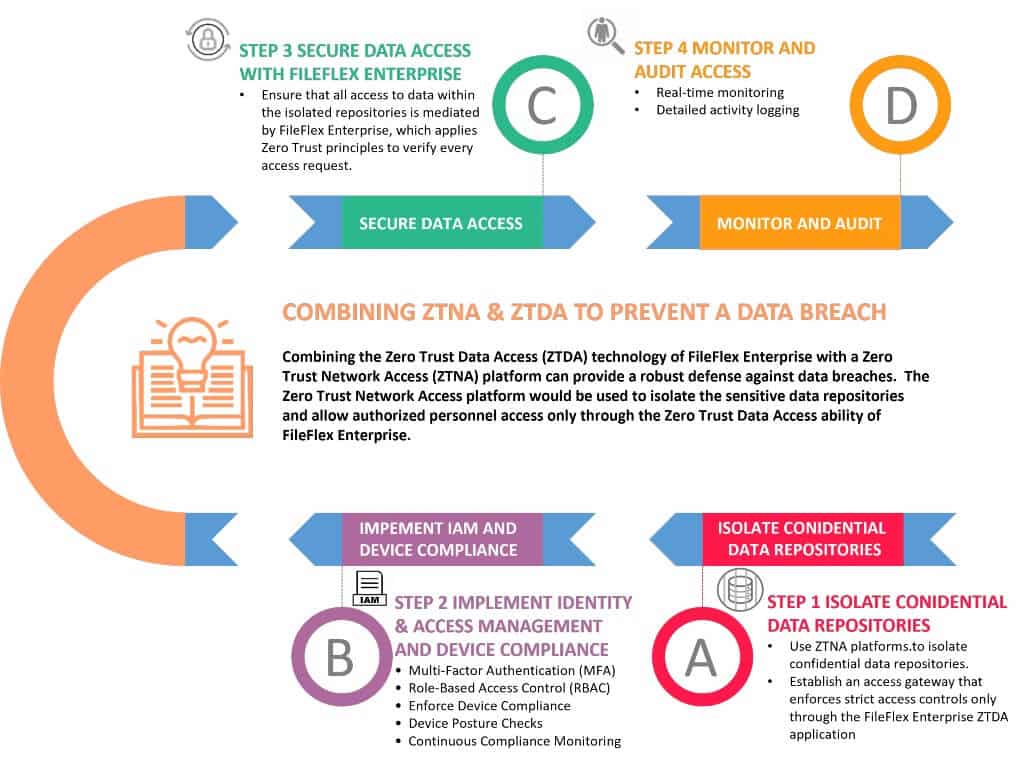
Combining ZTNA with ZTDA to Prevent Data Breach
Implementation Steps
-
Isolate Confidential Repositories:
- Network Segmentation: Use ZTNA platforms to segment the network and isolate repositories containing confidential information. This prevents unauthorized lateral movement within the network.
- Access Gateway: Ensure that access to these isolated repositories is only possible through the ZTNA gateway, which enforces strict access controls only through the FileFlex Enterprise ZTDA application.
-
Implement Identity and Access Management:
- Multi-Factor Authentication (MFA): Require MFA for all users attempting to access the isolated repositories, adding an extra layer of security.
- Role-Based Access Control (RBAC): Define roles and permissions to ensure that only authorized personnel can access sensitive data.
-
Enforce Device Compliance:
- Device Posture Checks: Use ZTNA platforms to verify that devices meet security standards before granting access. Non-compliant devices are denied access.
- Continuous Compliance Monitoring: Continuously monitor device status and revoke access if a device falls out of compliance.
-
Secure Data Access with FileFlex Enterprise:
- Zero Trust Data Access: Ensure that all access to data within the isolated repositories is mediated by FileFlex Enterprise, which applies Zero Trust principles to verify every access request.
- Encryption and Secure Data Handling: Encrypt all data access and transfers to protect sensitive information from unauthorized access and breaches.
-
Monitor and Audit Access:
- Real-Time Monitoring: Use ZTNA platforms and FileFlex Enterprise to monitor access attempts in real-time, allowing for immediate detection and response to suspicious activities.
- Detailed Logging: Maintain detailed logs of all access attempts and data transactions for forensic analysis and compliance reporting.
Hypothetical Application to Prevent the Tesla Data Breach
-
Pre-Breach Attempt:
- Identity Verification: ZTNA platforms would have enforced strict identity verification using MFA and role-based access controls, ensuring only authorized users could attempt access.
- Device Compliance: Device posture checks would ensure that only secure and compliant devices could access the network and sensitive repositories.
-
During the Breach Attempt:
- Access Control: ZTNA platforms would have detected and blocked unauthorized access attempts based on identity, device posture, and contextual factors.
- Data Access Verification: FileFlex Enterprise would have verified every data access request, blocking any unauthorized attempts to access or transfer confidential data.
- Real-Time Monitoring: Use the data activity tracking FileFlex Enterprise to monitor access actions in real-time, allowing for immediate detection and response to suspicious activities.
-
Post-Breach Attempt:
- Forensic Analysis: Detailed logs and monitoring from both ZTNA platforms and FileFlex Enterprise would provide comprehensive insights into how the breach was attempted, what measures were bypassed, and what data was targeted.
- Incident Response: Real-time alerts and monitoring would enable a swift incident response, minimizing the potential damage and securing the affected systems.
Conclusion
Combining ZTNA platforms with FileFlex Enterprise Zero Trust Data Access provides a multi-layered defense strategy that can effectively isolate repositories with confidential information and ensure that access is only granted to verified and authorized personnel. This comprehensive approach enhances security at both the network and data levels, significantly reducing the risk of data breaches like the one at Tesla.
Learn More About FileFlex Sign Up for a Free Trial