
Distributed administration of remote unstructured data access of a complex supply chain can significantly aid security and productivity.
Distributed Administration of Remote Unstructured Data Access for the Complex Supply Chain
Estimated reading time: 4 minutes
Centralized Control, Decentralized Enforcement
The location of unstructured data in today’s organizations can be incredibly complex. Its unstructured data can not only be anywhere on the organization’s multi-domain, hybrid-IT infrastructure of on-premises, cloud-hosted, Infrastructure-as-a-Service and SharePoint repositories, it is often shared in cooperation with subsidiaries, suppliers, vendors, partners, regulators, government agencies, contractors and related third-parties.
According to a study of 1000 CISOs and other risk and security professionals by the Ponemon Institute, 59% of organizations surveyed have been affected by cyberattacks through third parties. The organizations surveyed share confidential and sensitive information with 583 companies on average showing the growing complexity and use of third parties and partners. According to them, they were compromised because of a lack of centralized control, lack of resources and complexity of third-party relationships.
Centralized control over unstructured data but with decentralized enforcement and administration can greatly increase the security of remote access to unstructured data.
Recognizing the need to address the security holes in their supply chain, the US Department of Defense is moving all of its suppliers to obtain Cybersecurity Maturity Model Certification (CMMC) and the US Federal Government is using the National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171). These are comprehensive requirements on defense and federal suppliers to better defend the vast attack surface of their supply chains.
To stay ahead of this, the strong data governance and distributed administration capabilities of FileFlex Enterprise can be used to manage remote file access, collaboration and sharing with your third-party ecosystem. Let’s take a look at a few scenarios.
Distributed Enforcement – The Organization with Multiple Subsidiaries and/or Locations
Legacy Systems via Merger
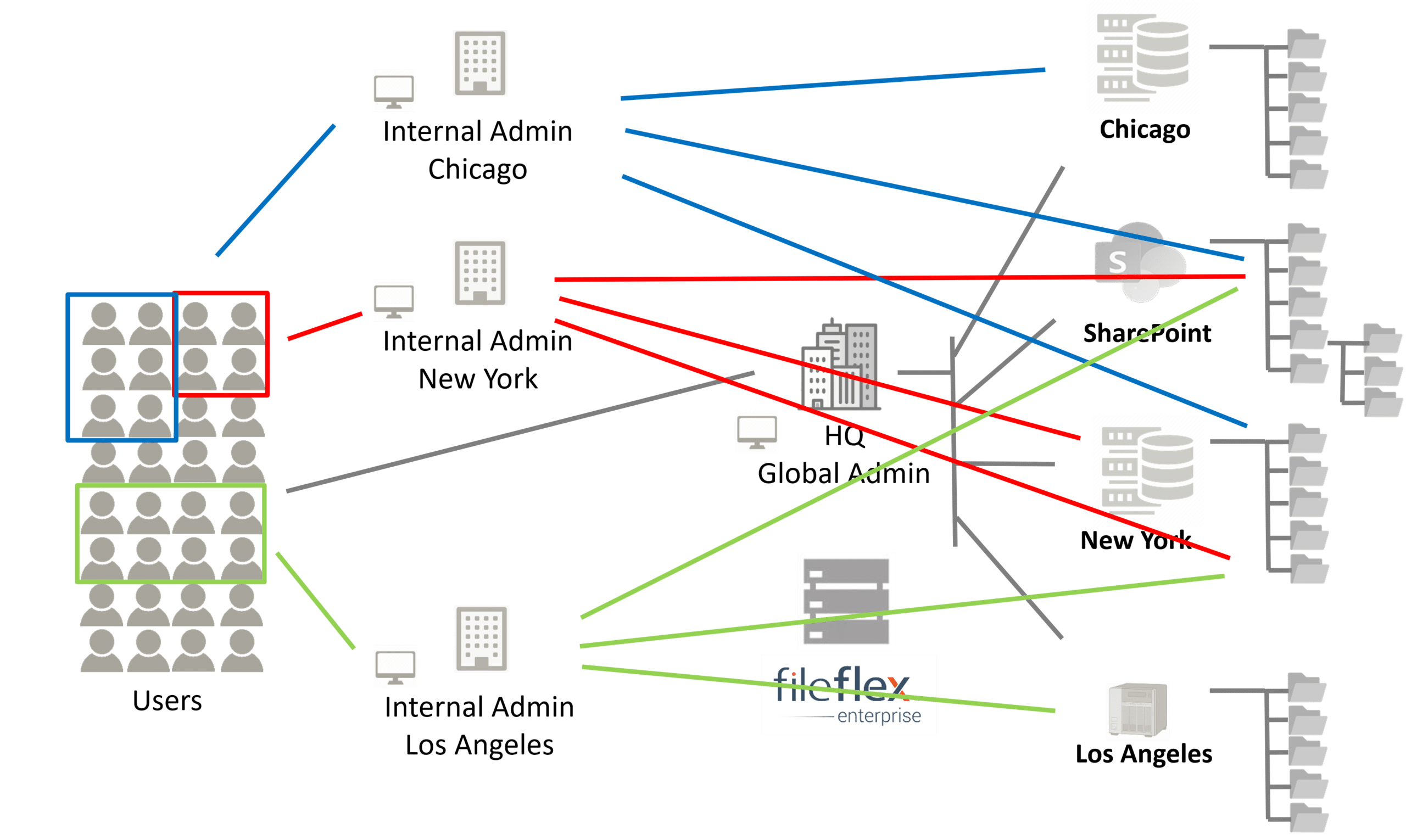
Distributed Enforcement – Integration of Legacy Systems Obtained from Mergers and Acquisitions
In one example, a transportation company has merged with several other companies through acquisition. These merged organizations are not only located in different cities, they have different IT infrastructures, some with outdated legacy hardware and software. However, now they need to share lots of independently generated unstructured data like forms, work orders, tracking, etc.
With the zero trust architecture of FileFlex Enterprise, they can now securely view all the relevant storage repositories of each location in Windows under a single-pane-of-glass where they can be accessed and collaborated as if they were on a local drive regardless of the difficulties related to their legacy technologies. Further, the IT administrators of each location can independently assign storage repositories and permissions to their own employees as needed without intervention from head office centralized IT. The head office, however, retains overall control and governance of all unstructured data and has a complete activity log over every activity of every user in every location. The organization now has centralized control over its unstructured data but with decentralized administration. Data sitting behind the firewalls of multiple networks, on servers, volumes, appliances, workstations, etc., as well as any cloud-owned repositories can be securely accessed through a deployed FileFlex Enterprise Server.
The Conglomerate
Distributed Enforcement for the Complex Conglomerate
In a second example, a large multinational mass media and entertainment conglomerate owns several movie, sound, animation and special-effects studios that operate independently but often need to cooperate. Their digital media libraries are enormous with huge individual files.
The zero trust data access architecture of FileFlex Enterprise allows the independent studios to securely share digital media libraries, all accessible to permitted users within Windows. The IT departments of each studio have administration over their users and what libraries they can access, they also have administration over what libraries can be accessed by the other studios and they can control the permission level of that access on a repository-by-repository or folder-by-folder basis. They also know who has accessed, downloaded, uploaded, shared or changed any file.
FileFlex Enterprise provides secure zero trust data access services to facilitate the many needs of conglomerates today where the multi-tenancy of a FileFlex Enterprise Server can be used to facilitate secure B2B data access. The only entity within the entire system that sees every activity from every tenant, company and individual user, is the system-level administrator (owner of the server). User forensics server-wide are visible and accessible to the system-level administrator and the user activities within each individual tenant may be also monitored by their respective tenant-level administrator.
The Organization with Outside Partners, Vendors and Complex Supply Chain
Distributed Enforcement for The Manufacturer
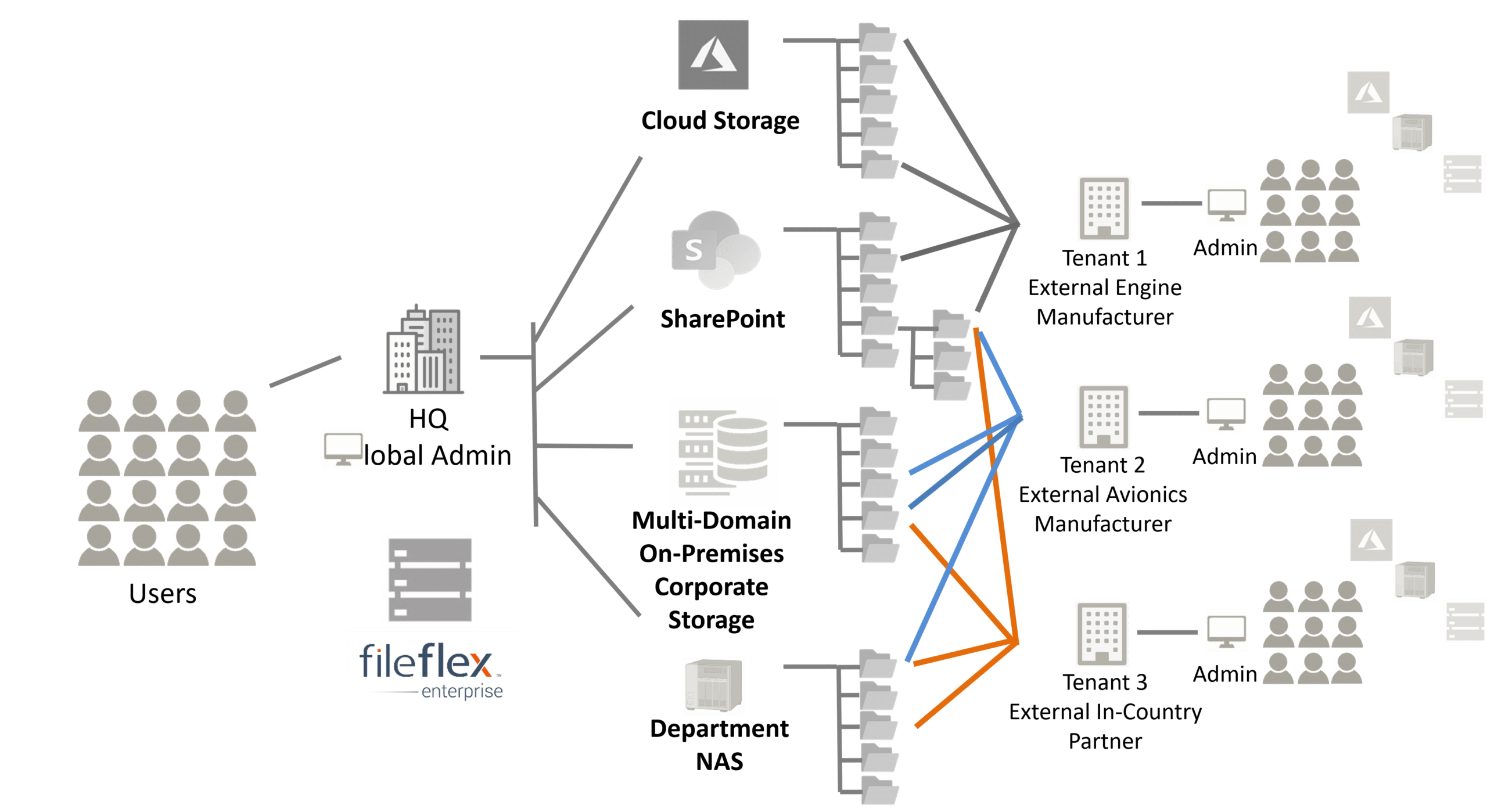
In this last example, a large aircraft manufacturer relies heavily on third-party vendors and has a diverse and complicated supply chain. They have several partners that make engines, electronics, and aviation components where the aircraft manufacturer is responsible for the overall engineering/design and final assembly. To spur domestic economies, international sales often involve local government subsidies and regulations that dictate the substantial use of in-country partners for sub-assembly and engineering work.
The zero trust based platform of FileFlex Enterprise allows their many vendors and in-country international partners access to any part of the library of complex engineering diagrams and manufacturing specifications. They can collaborate on the drawings and overall project. The aircraft manufacturer itself controls what resources each third-party vendor can access, collaborate and share. Alternatively, each third-party partner controls the resources that the aircraft manufacturer can access and collaborate on. There is no separate system or app that has to be used or learned for this access and collaboration, it is achieved from within Windows with no change in workflow making it an easy plug-and-play solution that can be easily rolled out to thousands of users in dozens of locations each using their localized Windows language and each administered by their own IT departments, but with the aircraft manufacturer maintaining governance over the unstructured data of each project.
The strong data governance and distributed administration capabilities of FileFlex Enterprise is used to manage remote file access, collaboration and sharing in a third-party ecosystem without using a VPN. Many external partners can be added and managed in this way. All external tenants are abstracted from one another, containerized and unaware of each other’s presence completely. Users and administrators within each tenant are blind to all other users and administrators from all other tenants to enable confidential, controlled & secure movement of inter-organizational data.
Conclusion
The zero trust architecture and distributed administration capability of FileFlex Enterprise allows organizations with complex supply chains centralized control with distributed administration for an unprecedented level of governance over their unstructured data. Meanwhile, the zero trust architecture allows for a higher level of security over the remote access, collaboration and sharing of that data extended to the entire supply chain reducing the risk inherent to using a complex supply chain. Finally, the integration of FileFlex Enterprise into the Windows operating system makes access to that unstructured data simple and easy – as though it was located on the local drive – with no change in workflow, no duplication and no syncing allowing the easy and rapid adoption by thousands of users and multiple languages and complete real-time audit on every interaction with alarm capabilities.
For more information on how FileFlex Enterprise aids compliance see: NIST SP-800-17v2 Access Control Practices for Remote Data Access, How to FileFlex Enterprise Helps DoD Contractors Meet CMMC Best Practices for Access Control, and overall security of the zero trust technology.
