
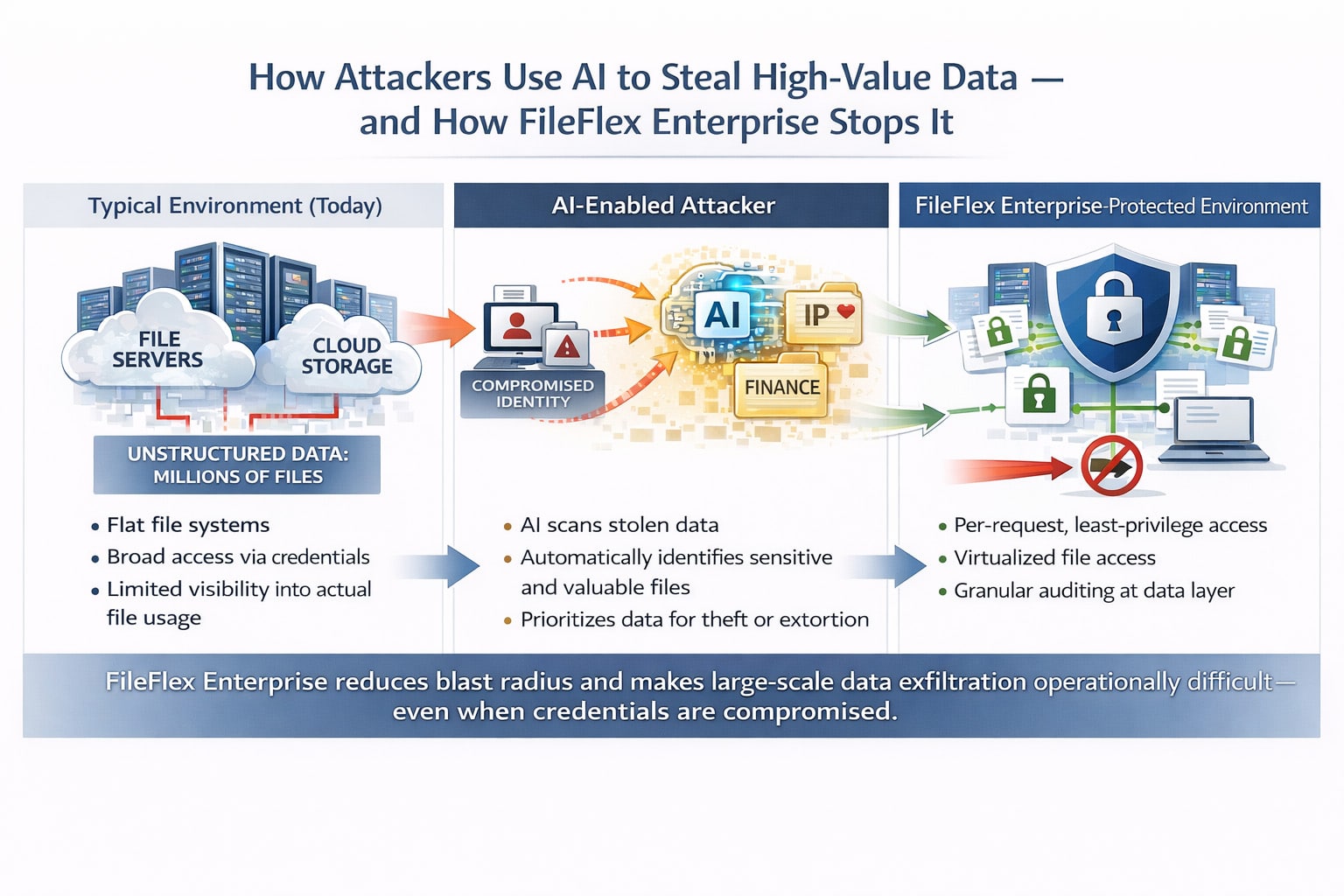
AI-driven cybercrime is rapidly increasing the risk of high-value data theft, and this post explains how FileFlex Enterprise mitigates that risk by enforcing least-privilege access, virtualized file controls, and granular auditing to disrupt large-scale exfiltration.
AI-Driven Cybercrime at Zettabyte Scale: Why Data Exfiltration Defines Modern Breaches
Estimated reading time: 2.5 minutes
Table of Contents
Q&A with Ed Dubrovsky, Board Advisor, Qnext
Cybercrime has quietly become one of the largest unmanaged economic risks facing organizations today. As attacks scale, data footprints explode, and artificial intelligence reshapes both offense and defense, traditional security models are struggling to keep up. To better understand what has changed—and what must change next—we spoke with Ed Dubrovsky, a veteran cybersecurity leader and Board Advisor at Qnext, about the realities of modern cybercrime and why data exfiltration has become the defining challenge of the AI era.
Q: How bad is global cybercrime today?
Global cybercrime has become one of the largest unmanaged economic risks on the planet. When you account for business disruption, data destruction, intellectual property theft, fraud, ransom payments, reputational damage, and litigation arising from class-action lawsuits, annual costs are now measured in the trillions of dollars. Multiple industry forecasts project that cybercrime will cost organizations more than $10 trillion annually by 2030, with no indication that the curve is flattening.
Attack volume, automation, and attacker sophistication continue to rise. At the same time, the near-universal adoption of AI across every sector has introduced an entirely new attack surface—one the industry has not yet fully understood or secured. This compounds the challenge of protecting what has become the lifeblood of the information age: data.
Q: What does it actually mean to “solve” a cyber-attack today?
In today’s environment, a “solved” cyber-attack is not just about restoring systems. It means containing the intruder, preventing further data exfiltration, preserving evidence for legal and regulatory obligations, and proving to customers, partners, and insurers that effective controls were in place.
AI dramatically raises the stakes. It allows threat actors—including criminal syndicates and nation-states—to ingest massive datasets, learn from them, and rapidly identify an organization’s true crown jewels. Finding the needle in a haystack is no longer difficult when AI effectively evaporates the haystack.
Q: What can organizations do to protect themselves?
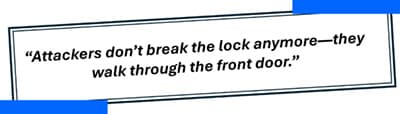
Most organizations continue to spend heavily on perimeter defenses—firewalls, endpoint tools, and point solutions—while the fundamental way data is accessed, stored, audited, and governed evolves far more slowly. Attackers increasingly bypass traditional defenses by abusing legitimate credentials, remote access tools, and cloud collaboration platforms. They don’t break the lock; they walk through the front door.
A useful analogy is your own home. Someone breaks in without visibly damaging the door or lock, yet you’re forced to replace both because trust has been broken. In cybersecurity, that loss of trust translates into millions of dollars in recovery costs, even when systems appear intact.
What has dominated cybersecurity for the past two decades—higher walls and deeper moats—no longer works on its own in a world of agentic AI, remote work, cloud services, and distributed data. This is the gap FileFlex is designed to address. It assumes intruders may get inside, but it disrupts the attack kill chain by changing how unstructured data is accessed, controlled, and audited.
Today, files are still largely stored in groups and directories with operating-system permissions that are difficult to manage at scale, often supplemented by add-on tools that act as bandages rather than fundamentally rethinking data governance. FileFlex takes a different approach by tightly controlling and virtualizing access to unstructured data, dramatically limiting lateral movement and large-scale theft—even when credentials are compromised.
Threat actors increasingly rely on specialized tools that exfiltrate data based on the access granted to stolen credentials. Those tools break down in a FileFlex-enabled environment. Importantly, FileFlex is designed to deploy on top of existing infrastructure, integrating with current systems rather than forcing a disruptive rip-and-replace, while fundamentally changing behavior and compliance at the data layer.
Q: Why is data exfiltration such a big issue now?

At the same time, the global data footprint has exploded. Data stored in the cloud alone is projected to exceed 100 zettabytes, roughly half of all data worldwide, with total global storage expected to surpass 200 zettabytes. A single zettabyte represents roughly a billion terabytes.
Cybercrime has effectively shifted from targeting terabyte-scale environments to operating at zettabyte scale, enabled by faster networks, more capable tooling, and the weaponization of artificial intelligence for reconnaissance, automation, and exploitation.
This is precisely where FileFlex comes into play. By changing how organizations treat and control unstructured data—documents and files spread across endpoints, file servers, and clouds—it makes large-scale exfiltration operationally difficult and economically unattractive. By reducing the blast radius of a compromise, FileFlex has the potential to materially shift the economics of cybercrime back in favor of defenders.
For further reading, see The Zero Trust Data Gap, From VPN Risk to Zero Trust Security: A Smarter Approach to Remote Access and How to Make Your Hybrid-IT and Infrastructure-as-a-Service Environment Easier for Your Users.
Learn More About FileFlex Sign Up for a Free Trial