
Microsoft 365 E5 security for remote and external users takes a significant step forward by integrating Zero Trust Data Access (ZTDA) capabilities to enhance protection, streamline data management, and meet evolving cybersecurity challenges.
21 Reasons to Supplement Microsoft 365 E5 Security with Zero Trust Data Access
Estimated reading time: 5 minutes
Table of Contents
What is Microsoft 365 E5?
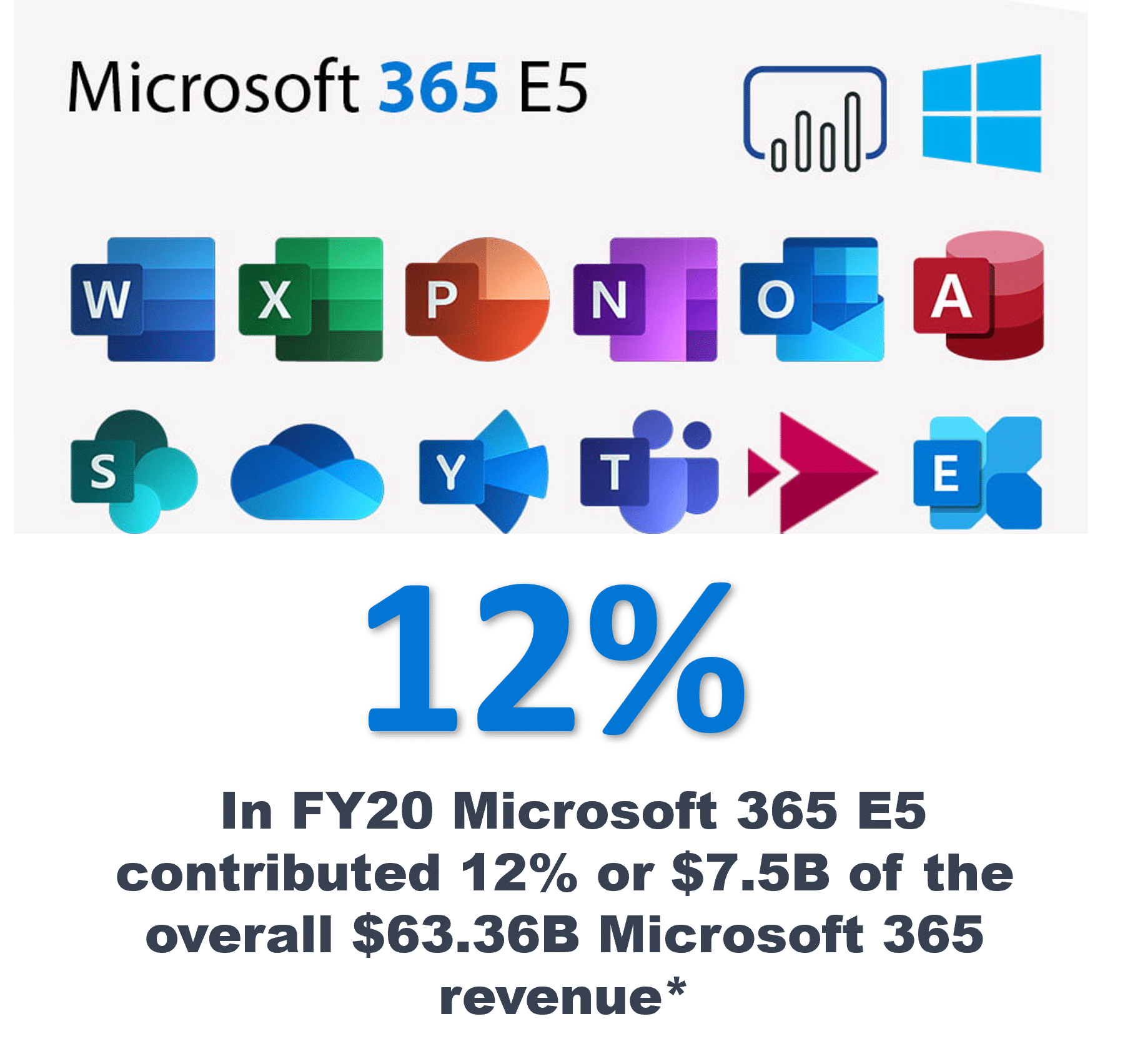
Microsoft 365 E5 security for remote and external users is greatly enhanced when Zero Trust Data Access (ZTDA) functionality and security are tied in and used to add value to this Microsoft ecosystem.
Adding Zero Trust data access capabilities to Microsoft 365 E5 security can be beneficial for organizations seeking to enhance their security posture for remote and external users and address evolving cybersecurity challenges.
What is Zero Trust Data Access?
Zero Trust Data Access (ZTDA) as implemented by FileFlex Enterprise, is a technology that provides secure access to files and folders for authorized users through a zero-trust architecture. This architecture uses a server that verifies users and specific permissions for that user then via a connector agent sends the requested files to that user much like the way a bank teller is used in a bank. The fundamental principle of Zero Trust Data Access is that access to data should be granted only on a need-to-know basis, and every access request should be authenticated and authorized against policy before granting access. Under the Zero Trust Data Access model, every data access request is verified against a set of rules that dictate what data can be accessed, and by whom.
A zero trust data access architecture is designed to:
-
-
- Protect access to a network segment, application, or data without providing access to the organization’s network infrastructure
- Provide IT the tools they need to control that access
- Protect the transfer of information and communications
- Allow for only authorized access and,
- Protect user credentials.
-
Zero trust data access establishes encrypted connections between remote employees’ devices and a centralized corporate network over the Network or the Internet, however, the connection is made through a zero trust architecture that does not allow direct access to resources. It also provides access to cloud-hosted repositories, FTP repositories, SharePoint repositories, and on-premises storage over multiple domains. Employees can connect to their corporate resources from anywhere with internet access, however, their access can be controlled and restricted by management according to Least Privilege Principles and IT chain of command. It also provides file-sharing capability and because all actions are controlled by a zero trust server, all actions are recorded for forensic investigation and for output to the SIEM to detect ransomware attacks in process.
21 Reasons to Supplement Microsoft 365 E5 Security for Remote and External Users with Zero Trust Data Access
Here are 21 reasons why an organization might want to incorporate Zero Trust principles as implemented by FileFlex Enterprise into their Microsoft 365 E5 security environment for remote and external users:
-
-
-
Brings Increased Cutting-Edge Security:
- Zero Trust Data Access is a security model that assumes that threats may already be inside the network. By implementing Zero Trust data access with Microsoft 365 E5 security, organizations can bolster their security and reduce the risk of data breaches and unauthorized access, even from trusted devices or users.
-
Reduces the Risk of Ransomware:
- By limiting access to sensitive data, monitoring user activity, and restricting lateral movement, ZTDA can help prevent ransomware attacks and minimize their impact on data integrity.
-
Superior Regulatory Compliance:
- ZTDA facilitates compliance with data privacy regulations like HIPAA, GDPR, CIRCI, CMMC, ISO 27001, and ENISA, ensuring that only authorized users can access sensitive data.
-
Exceptional Insider Threat Mitigation:
- ZTDA effectively reduces insider threats, such as unauthorized access by employees or contractors, by strictly controlling access based on user roles and responsibilities, preventing lateral movement and keeping infrastructure dark to users.
-
Simplified Management:
- ZTDA simplifies security management with a unified approach applicable to all users, reducing complexity in managing diverse access methods
-
Enhanced User Experience:
- While prioritizing security, ZTDA integrates seamlessly into Windows and Microsoft 365 E5 established workflows, providing a user-friendly experience and improving access to data.
-
Excellent Data Governance:
- ZTDA enforces granular access controls and policies consistently across various data sources, promoting effective data governance.
-
Unique Federated Storage Management:
- ZTDA streamlines access and sharing management across diverse on-premises, cloud-hosted and SharePoint data repositories across multiple domains, allowing central access control, reducing administrative burdens, and enhancing operational efficiency.
-
Improved Data Visibility and Control:
- ZTDA provides detailed activity logs for data access and sharing, enabling IT managers to monitor user behavior, detect anomalies, and identify potential security threats.
-
Reduced Complexity:
- ZTDA simplifies access management by unifying authentication, authorization, and access control, reducing complexity in managing access.
-
Improved Secure Collaboration:
- ZTDA enables secure data sharing and collaboration with access controls aligned to user roles and needs, promoting teamwork while ensuring data security.
-
Reduced Infrastructure Load and Scalability:
- ZTDA can scale to handle growing data volumes and storage locations, reducing infrastructure requirements and the need for data duplication.
-
Distinctive Granular Contractor Access:
- Organizations can grant contractors access to specific resources without granting direct site access based on micro-segmentation and least privilege principles, reducing the risk associated with providing data access to external parties.
-
Extends Centralized Control with Decentralized Administration:
- ZTDA allows decentralized administration for subsidiaries and partners while maintaining centralized IT control and visibility.
-
Remarkable Granular File and Folder Micro-Segmentation for Enhanced Data Protection:
- ZTDA offers micro-segmentation down to the file and folder level, enhancing network security, compliance, and incident response.
-
Does Not Allow Direct Access to Infrastructure:
- Users and recipients cannot directly access the storage infrastructure, enhancing security by abstracting users from the infrastructure.
-
Adds Secure File Sharing:
- ZTDA includes secure file-sharing capabilities from within Windows, eliminating the need for additional file-sharing platforms and enhancing security by aligning file-sharing activities with Zero Trust principles.
-
Brings an IT-Controlled Chain of Command:
- The management console provides granular control over permission levels down to the file level, protecting sensitive data.
-
Is a Low-Cost Model:
- ZTDA operates on a cost-effective subscription model.
-
Provides Access to Multiple SharePoint Accounts from One FileFlex Account:
-
- The power of a ZTDA architecture means that multiple SharePoint or OneDrive accounts from potentially multiple departments, subsidiaries or even organizations can be federated into one FileFlex account in Windows and Microsoft 365. For example, org1.sharepoint.com, org2.sharepoint.com and org2.sharepoint.com could all be accessed from one FileFlex account in Windows.
-
-
-
Containerized Guest Profiles Maintained Outside of Active Directory/Azure AD:
- External parties such as customers, suppliers and partners can be given limited access to specific files or folders under an IT-controlled chain of command via containerized guest profiles without having to add them to the company Active Directory.
-
Superior to VPN for Remote and External Users:
- Most companies use some form of a VPN to enable on-prem access for E5 network access for remote users as well as for external users. ZTDA can eliminate this need and alleviate the burden on maintaining and managing these additional network connections that are not as secure. For more details see “Why Replacing FTP with ZTDA is a No-Brainer”.
-
-
Summary – Elevating Microsoft 365 E5 Security with Zero Trust Data Access Capabilities
The article emphasizes the advantages of integrating Zero Trust Data Access (ZTDA) capabilities, specifically as implemented by FileFlex Enterprise, into Microsoft 365 E5 security, particularly for remote and external users. By embracing ZTDA principles, organizations can elevate their security posture, reduce the risk of data breaches, enhance regulatory compliance, mitigate insider threats, simplify management, and streamline access controls, among other benefits, ultimately fortifying their data protection and access management efforts within the Microsoft ecosystem.
In addition to security benefits, the following webinar talks about how zero trust data access extends Microsoft 365 functionality into a hybrid storage infrastructure.
For more reading about using zero trust data access in a Microsoft ecosystem see Accelerating Digital Transformation Leveraging Zero Trust Data Access (ZTDA) in a Microsoft Ecosystem, Key Benefits of Extending Microsoft 365 with FileFlex Enterprise, and Extending Microsoft 365 Functionality into a Hybrid-IT Infrastructure.
Learn More About FileFlex Sign Up for a Free Trial