
Restricting direct access to storage infrastructure through Zero Trust Data Access (ZTDA) enhances security, reduces risks like insider threats and ransomware, ensures compliance, and improves operational efficiency by enforcing identity-based controls, abstracting data access, and leveraging advanced monitoring.
Top 10 Benefits of Restricting Direct Access to the Storage Infrastructure
Estimated reading time: 12 minutes
Table of Contents
-
-
- Introduction: Rethinking Security – Why Direct Access Is a Risk You Can’t Afford
- Security Risks Inherent to Employee Access to Infrastructure
- Security Risks Inherent to Malicious Entity Access to Infrastructure
- How the Zero Trust Data Access Model Minimizes Direct Access to Data
- Top Benefits of Using Zero Trust Data Access to Prevent Direct Access to the Storage Infrastructure
- Conclusion: Safeguarding the Future with ZTDA
-
Introduction: Rethinking Security – Why Direct Access Is a Risk You Can’t Afford

Zero Trust Data Access (ZTDA) represents a paradigm shift in cybersecurity. By eliminating direct access to infrastructure and enforcing strict, identity-based controls, ZTDA minimizes risk while enabling secure and efficient operations. This article explores the compelling advantages of ZTDA, detailing how it transforms security, enhances compliance, and streamlines access management. From reducing attack surfaces to ensuring future-proof defenses, ZTDA provides a robust framework for safeguarding today’s dynamic IT environments.

Security Risks Inherent to Employee Access to Infrastructure
Security risks are introduced when employees or contractors have access to an organization’s storage infrastructure. These risks can stem from intentional malicious activities, inadvertent mistakes, or vulnerabilities in the systems being accessed. Below are some key risks to consider:
-
Insider Threats
-
- Malicious Intent: Employees or contractors could intentionally misuse their access to steal data, sabotage systems, or leak sensitive information.
- Unintentional Breaches: Accidental actions, such as sharing credentials, misconfiguring systems, or falling for phishing attacks, can lead to data breaches or system vulnerabilities.
-
Data Leakage
-
- Access to sensitive data (e.g., intellectual property, customer data, or financial records) increases the risk of it being copied, shared, or stolen, whether deliberately or inadvertently.
-
Credential Theft
-
- Weak passwords, password reuse, or insufficient multi-factor authentication (MFA) can lead to stolen credentials, granting unauthorized access to critical systems.
-
Third-Party Risks
-
- Contractors often work remotely or on temporary contracts, making it harder to enforce the same security policies and practices as full-time employees.
- If contractors reuse credentials or access systems from insecure networks, it could introduce vulnerabilities.
-
Unauthorized Access
-
- Lack of proper access controls can result in employees or contractors gaining access to data they don’t need for their role, leading to overexposure of sensitive information.
-
Privilege Escalation
-
- Mismanagement of access rights could allow users to escalate their privileges, gaining unauthorized control over critical systems.
-
Endpoint Security
-
- Devices used by employees or contractors might be unpatched, unsecured, or infected with malware, posing a risk when connecting to the organization’s storage network.
-
Lack of Visibility
-
- Poor monitoring or logging can prevent organizations from detecting and responding to unauthorized activities in a timely manner.
-
Compliance Violations
-
- Mishandling sensitive data or granting excessive access can lead to violations of regulations such as GDPR and HIPAA resulting in fines and reputational damage.
-
Shadow IT
-
- Employees or contractors might use unauthorized applications or services to perform their work, potentially introducing unvetted and unsecured software into the organization’s ecosystem.
Security Risks Inherent to Malicious Entity Access to Infrastructure
If a malicious entity gains access to an organization’s storage infrastructure, the potential security risks are severe and wide-ranging. These risks can result in significant financial loss, reputational damage, legal liabilities, and operational disruption. Below are the key risks associated with such an incident:
- Data Breach and Theft
-
- Sensitive Information: Attackers can exfiltrate confidential data such as customer records, trade secrets, intellectual property, or financial information.
- Identity Theft: Personal data of employees or customers may be stolen and used for fraudulent activities.
-
Financial Loss
-
- Fraud: Attackers could manipulate financial systems to steal money directly or reroute transactions.
- Ransomware Attacks: Critical data or systems may be encrypted, with attackers demanding a ransom for their release.
-
Operational Disruption
-
- Denial-of-Service (DoS): Malicious entities can disable critical services, causing downtime and disrupting business operations.
- System Sabotage: Attackers might delete or corrupt data, damage hardware, or introduce bugs into software systems.
-
Spread of Malware
-
- Internal Propagation: Malware introduced into the infrastructure could spread across networks, infecting devices and systems.
- Supply Chain Attacks: Attackers may use the organization’s infrastructure to target partners, customers, or vendors.
-
Unauthorized Access and Escalation
-
- Privilege Escalation: Once inside, attackers may exploit vulnerabilities to gain administrative control over systems.
- Persistent Access: Attackers might create backdoors or install rootkits to maintain long-term access.
-
Reputational Damage
-
- Customer Trust: Public exposure of a breach can erode trust and result in customer churn.
- Negative Publicity: Media coverage of the breach can harm the organization’s brand and credibility.
-
Compliance Violations
-
- Regulatory Fines: Breaches of laws like GDPR, CCPA, or HIPAA could lead to hefty fines.
- Litigation: Impacted parties may file lawsuits, resulting in legal costs and settlements.
-
Espionage and Competitive Disadvantage
-
- Corporate Espionage: Attackers might steal sensitive R&D data or strategies, benefiting competitors or foreign entities.
- Market Manipulation: Financial information or trade secrets could be leaked to manipulate markets or devalue the organization.
-
Loss of Intellectual Property
-
- Proprietary designs, source code, or patents could be stolen, undermining the organization’s competitive edge.
-
Exploitation of Infrastructure
-
- Botnets: The compromised infrastructure could be used to launch attacks on other organizations.
- Phishing Campaigns: Attackers may use the organization’s email systems to launch phishing attacks on others, leveraging trust.
-
Insider Threats Amplified
-
- Credential Abuse: Malicious entities might exploit stolen credentials to impersonate legitimate employees.
- Manipulation: Attackers could coerce or blackmail employees into furthering their objectives.

How the Zero Trust Data Access Model Minimizes Direct Access to Data
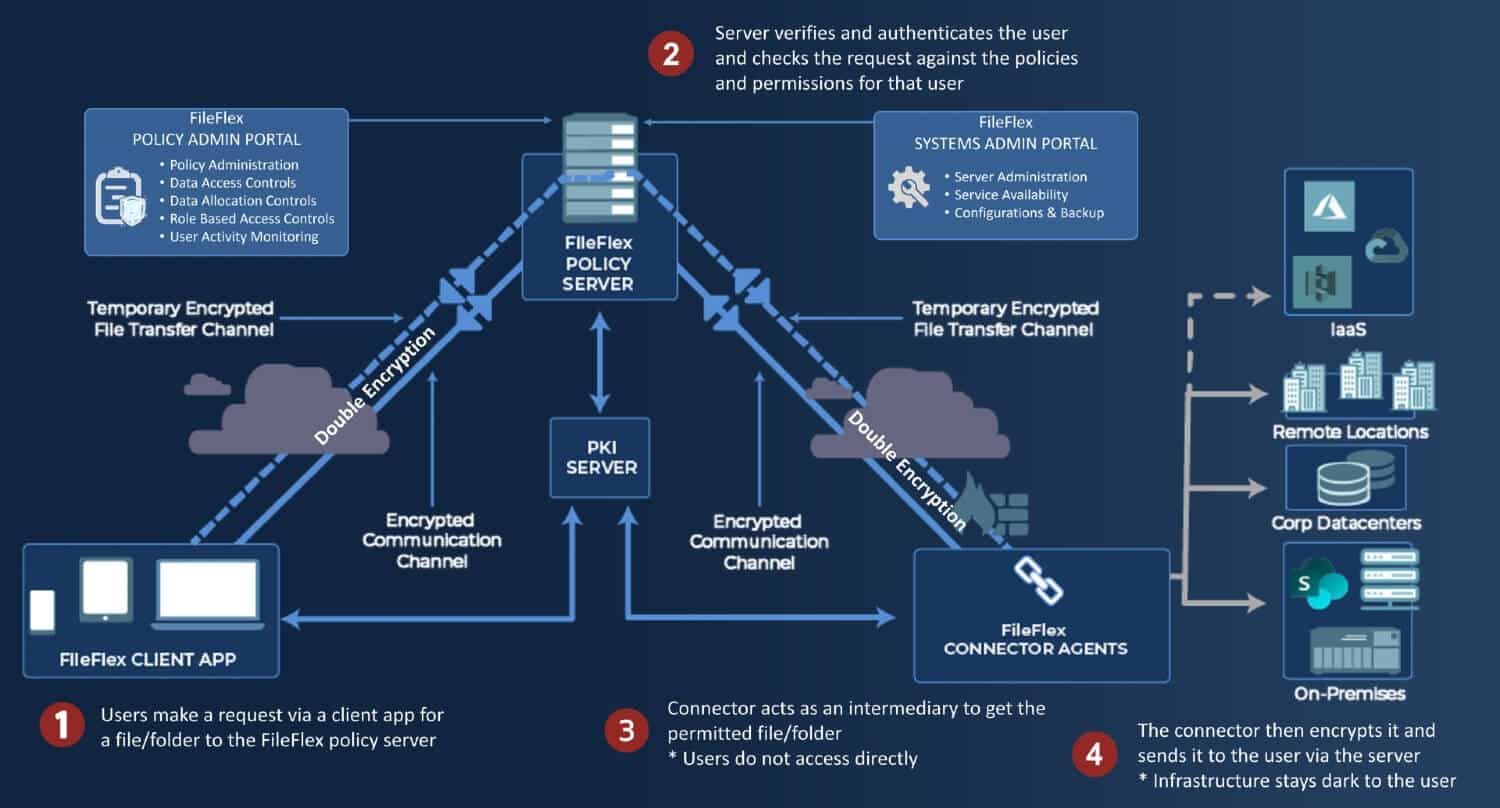
As illustrated in Diagram 1 above, a Zero Trust Data Access (ZTDA) architecture (as implemented by FileFlex Enterprise) prevents direct access to infrastructure and data resources by enforcing strict, granular controls and mediating all access through secure gateways and policies. It shifts the focus from perimeter-based security to identity and data-centric security. Here’s how ZTDA achieves this:
-
No Direct Infrastructure Exposure
-
- Secure Proxy or Broker Model
- ZTDA uses a client-to-policy server to connector agent to data storage architecture. This acts as a broker or gateway, to manage all access requests. Users and devices interact with the zero-trust server/broker architecture, which enforces access policies and retrieves data on their behalf.
- The storage infrastructure remains hidden and cannot be directly accessed by end users.
- The broker communicates with the storage infrastructure via authenticated and encrypted channels.
- ZTDA uses a client-to-policy server to connector agent to data storage architecture. This acts as a broker or gateway, to manage all access requests. Users and devices interact with the zero-trust server/broker architecture, which enforces access policies and retrieves data on their behalf.
- Micro-Segmentation
- Infrastructure is divided into isolated segments, limiting visibility and access even for authenticated users. This segmentation ensures that even if one resource is compromised, others remain protected.
- Software Defined Perimeter (SDP) Dark Cloud Approach
- The ZTDA employs a Software-Defined Perimeter (SDP) attitude that enforces a “dark cloud” approach, which is a key principle in the Zero Trust model. This approach ensures that the storage infrastructure is hidden and inaccessible to any entity that has not been authenticated and explicitly authorized. Here’s a deeper explanation of how it works:
- Invisible Infrastructure
- Resources protected by ZTDA are not discoverable by unauthorized users. Unlike traditional network architectures, where infrastructure components (e.g., IP addresses, ports, or server names) are visible to anyone on the network, ZTDA ensures these components are “cloaked” or hidden. Unauthorized users cannot even determine whether a resource exists, let alone interact with it.
- Access Based on Identity, Not Location
- Traditional perimeter-based security models rely on network location (e.g., being inside the corporate firewall) to grant access. ZTDA flips this model by granting access based on verified identity and policy. Only authenticated users can discover and interact with specific resources.
- Authentication Before Connection (ABAC)
- Unlike traditional models, where a user can sometimes connect to a storage repository before authentication, ZTDA requires users to authenticate first. If authentication fails, the connection attempt is dropped, and the user cannot proceed or gain any visibility into the network.
- Dynamic Resource Discovery
- Once a user or device is authenticated, they are dynamically provisioned access to only the resources they are authorized to use. All other resources remain hidden, even if they are on the same network.
- Invisible Infrastructure
- The ZTDA employs a Software-Defined Perimeter (SDP) attitude that enforces a “dark cloud” approach, which is a key principle in the Zero Trust model. This approach ensures that the storage infrastructure is hidden and inaccessible to any entity that has not been authenticated and explicitly authorized. Here’s a deeper explanation of how it works:
- Secure Proxy or Broker Model
-
Identity-Centric Access Control
-
- Authentication Before Access
- When enabled, every access request is authenticated via multi-factor authentication (MFA), ensuring only verified identities can interact with the broker. Even employees or contractors must authenticate each session. Stolen credentials alone are insufficient, as MFA is also required.
- Least Privilege Enforcement
- Users are granted access only to the specific data they need for their role and nothing more, minimizing unnecessary exposure to sensitive infrastructure.
- Authentication Before Access
-
Data Access Abstracted From the User
-
- Granular Access Policies
- ZTDA enforces fine-grained policies to define exactly what users can do with data (e.g., view, edit, share) without exposing the physical storage or infrastructure. Policies are applied at the file or folder level, restricting users’ ability to move or manipulate data outside their scope.
- Data Virtualization
- Users access a virtualized view of the data through the broker, meaning they interact with data without direct access to the underlying storage system.
- This prevents users or malicious entities from directly interacting with file systems and data repositories.
- No Persistent Connections
- Sessions are tightly controlled and terminated immediately after the task is complete, reducing the risk of hijacked or lingering connections.
- Granular Access Policies
-
Encryption and Secure Communication
-
- End-to-End Encryption
- Data is encrypted in transit, ensuring that even if intercepted, it remains inaccessible. Encryption keys are managed by a PKI server, separately from data, adding an additional layer of protection.
- Access Through Secure Channels
- All communication with infrastructure is routed through encrypted tunnels.
- End-to-End Encryption
-
Monitoring and Enforcement
-
- Comprehensive Activity Tracking
- Every action—who accessed what, and when —is logged. This visibility ensures accountability and facilitates forensic investigations.
- Behavioral Analytics
- The activity log can be exported to a SIEM where user behavior is continuously analyzed for anomalies, such as accessing unusual data or making unexpected changes. If suspicious activity is detected, access can be revoked.
- Threat Response
- If a malicious entity or compromised user is detected, ZTDA/SIEM systems can alert IT to revoke access and isolate sessions.
- Comprehensive Activity Tracking
-
Preventing Data Resource Exposure
-
- Data Access Without Copying or Syncing
- ZTDA solutions often allow users to work with data in situ (e.g., viewing, analyzing) without downloading or copying it. This prevents data from leaving the secure environment.
- Data Access Without Copying or Syncing
Top Benefits of Using Zero Trust Data Access to Prevent Direct Access to the Storage Infrastructure
Preventing direct access to the storage infrastructure through Zero Trust Data Access (ZTDA) as implemented by FileFlex Enterprise offers significant security, operational, and compliance benefits. Here’s why an organization would want to implement this approach:
-
Minimized Attack Surface
-
- The traditional model provides direct access to the storage infrastructure and exposes services, ports, and protocols, creating potential entry points for attackers. However, ZTDA hides the storage infrastructure from users and attackers. Malicious entities cannot identify or exploit vulnerabilities in servers, databases, or networks without direct access.
-
- This drastically reduces the likelihood of successful cyberattacks and prevents attackers from using reconnaissance tools to map the organization’s network or systems.
-
Mitigation of Insider Threats
-
- While the traditional model allows insiders or compromised employees to access more systems than necessary, potentially leading to data leaks or sabotage, Zero Trust Data Access implements the least privilege principle and prevents users from directly interacting with the storage infrastructure. All access is mediated and logged, limiting the damage insiders can cause.
-
- This reduces the risk of intentional or accidental misuse of systems and prevents lateral movement within the network by malicious insiders or compromised accounts.
-
Enhanced Security for Remote Work
-
- Traditional VPNs often provide broad access to the internal network, exposing infrastructure to remote employees or contractors. ZTDA on the other hand, allows secure access to specific data without exposing the entire infrastructure.
-
- This protects critical systems from unauthorized access, even in distributed or hybrid work environments and secures third-party and contractor access without the need for extensive trust or overprovisioning.
-
Stronger Data Protection
-
- Using the traditional model, users may have unrestricted access to data, enabling them to move, download, or share sensitive files. ZTDA enforces in-place data access, ensuring users can view or process data without downloading or directly accessing the underlying storage.
-
- This prevents data exfiltration by limiting what users can do with data and enhances compliance with regulations like GDPR, HIPAA, or CCPA by restricting how sensitive information is accessed and handled.
-
Improved Scalability and Flexibility
-
- Using the traditional model adding new users or resources often involves complex network configurations, increasing management overhead. Zero Trust Data Access uses dynamic policies and a brokered access model, allowing resources and users to be added or removed easily without impacting overall infrastructure security.
-
- This reduces administrative burden for IT teams and simplifies resource management in dynamic environments like cloud or hybrid infrastructures.
-
Enhanced Compliance and Auditing
-
- Direct access can make tracking and auditing activities across infrastructure challenging when using the traditional model. Zero Trust Data Access logs every access action across a hybrid storage infrastructure, providing detailed records of who accessed what and when
-
- This meets compliance requirements for audit trails and data protection and simplifies forensic investigations by providing a clear and complete access history.
-
Reduced Risk from Malware and Ransomware
-
- Using the traditional model, malware or ransomware that infects a device may use direct access to spread laterally across systems or encrypt critical infrastructure. ZTDA mediates all access through secure brokers and prevents direct connections, to limit the spread of malicious code.
-
- This helps contain infections, protecting sensitive systems and data and reduces downtime and costs associated with recovery from ransomware attacks.
-
Better User Experience
-
- With the traditional model users often experience performance issues due to overly restrictive or poorly configured security measures. ZTDA provides seamless, brokered access to only the necessary resources without unnecessary network or system exposure.
-
- This improves performance by streamlining access and increases productivity by enabling secure, role-based access to resources without friction.
-
Future-Proof Security Posture
-
- Legacy systems and static defenses struggle to keep up with evolving threats under the traditional model. By exporting the activity log to a SIEM, ZTDA adapts to threats by using continuous monitoring, behavior analysis, and real-time policy enforcement.
-
- This prepares organizations for modern security challenges like zero-day attacks and advanced persistent threats (APTs) and supports integration with emerging technologies like AI-based threat detection or cloud-native architectures.
-
Simplified Cloud and Multi-Cloud Security
-
- Traditionally managing security across multiple cloud providers or hybrid environments can expose infrastructure inconsistencies. ZTDA abstracts data access, providing a unified security model regardless of where the infrastructure resides.
-
- This reduces complexity in securing cloud environments and facilitates seamless adoption of cloud-native and hybrid solutions.
Conclusion: Safeguarding the Future with ZTDA
As organizations navigate an increasingly perilous cybersecurity landscape, Zero Trust Data Access (ZTDA) as implemented by FileFlex Enterprise offers a transformative solution that goes beyond traditional security models. By minimizing direct access to the storage infrastructure, enforcing granular policies, and leveraging advanced monitoring, ZTDA dramatically reduces risk while maintaining operational efficiency. From mitigating insider threats to future-proofing against emerging challenges, ZTDA empowers organizations to protect their most critical assets without compromise. In adopting this approach, businesses not only enhance their security posture but also build a resilient foundation for innovation and growth in a digital-first world.
For further information read 9 Top Reasons Why Your Organization Needs Zero Trust Least Privilege Access, Top 8 Reasons Your Organization Needs Zero Trust Activity Tracking, Embracing Zero Trust Data Access for IT-Controlled Chain-of-Command, Why You Need Zero Trust Data Access Micro-Segmentation, and Distributed Administration of Remote Unstructured Data Access for the Complex Supply Chain.
*Version Data Breach Investigations Report
Learn More About FileFlex Sign Up for a Free Trial