How to Mitigate Spear-Phishing via the FileFlex Enterprise Zero Trust Platform
FileFlex Enterprise is a remote access and sharing platform built from the ground up to be zero trust compliant. In addition to perimeter defenses, you use the FileFlex zero-trust approach and bring IT control over sharing. Zero Trust is a NIST standard that augments traditional perimeter-based security, by always authenticating and always verifying all transactions all the time or “never trust, always verify”.
Estimated reading time: 3 minutes
How the Spear-Phishing Attack Vector Works
Cyber-attacks are the fastest-growing crime
According to the global cybersecurity firm – the Herjavec Group – cyber-attacks are the fastest-growing crime in our society today and the hackers and criminals that commit cybercrimes are becoming more and more sophisticated. In fact, according to Cybersecurity Ventures, cybercrimes will be close to a staggering $6 trillion annually by 2021[1]. Even the best-defended companies are being affected.
Spear phishing is the top vector of attack
According to Symantec’s Internet Security Threat, the top vector is spear phishing used in 69% of targeted attacks[2]. Spear phishing uses email in 2 different ways to target specific individuals in your company – spear-phishing attachments, and spear-phishing links.
How a spear-phishing attack works
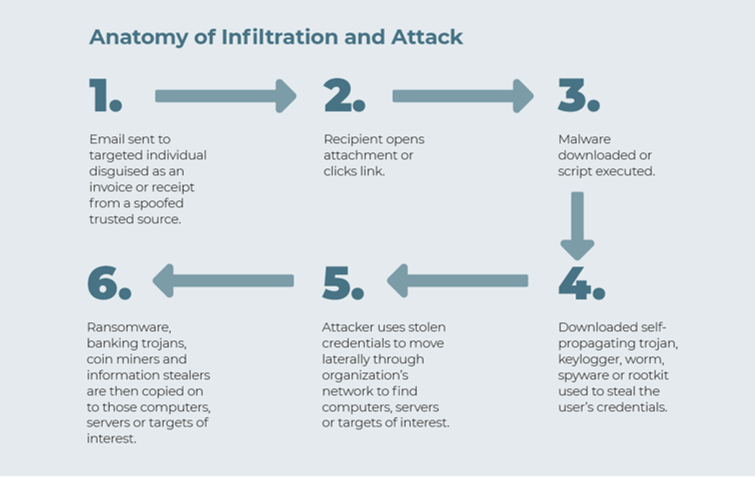
Here is how it works.
- In this attack vector, an email from a spoofed or impersonated trusted source is sent to a targeted individual in your organization. It is most often disguised as a legitimate notification such as an invoice or a receipt. If a link, it could look like a legitimate link from a cloud storage provider.
- The user then opens the attachment or clicks the link.
- The attachment or link executes a script and downloads malware. Microsoft Office users are the most at risk of falling victim to email-based malware, with Office files accounting for 48 percent of malicious email attachments[3] When the user opens the Office file, a macro will call a PowerShell script (a command-line shell and scripting language built on the .NET framework normally used for system administration) which in turn downloads the malicious payload. The use of a PowerShell script is up 1000% over last year[4].
- The malicious payload itself will be a self-propagating trojan, keylogger, worm, spyware, or rootkit to steal the user’s credentials.
- The credentials are then used by attackers for lateral movement to explore and move across a network to further infect computers/servers/targets of interest.
- Ransomware, banking trojans, cryptocurrency coinminers, and information stealers are then copied on to those computers/servers/targets of interest.
Opening files sent by spear phishing
Opening files sent by spear-phishing is by far the top vector of attack and the most common method of sharing files is either to attach the file to an email or to embed a link to a cloud-based file-sharing service. The email can spoof or impersonate the sender and disguise the attachment/link such that the receiver in your organization thinks it is a legitimate file from a trusted source.
How to Mitigate Spear-Phishing with the FileFlex Enterprise Zero-Trust Platform
FileFlex Enterprise allows you to restrict or reduce the use of links and attachments
FileFlex Enterprise helps mitigate malware introduced through the use of spoofed email senders with embedded links to cloud-based file-sharing services and the use of disguised email attachments because instead of relying on anti-virus software now you can restrict or limit the use of links and attachments within your organization and force user authentication through FileFlex. Instead of relying on perimeter defenses, you use a zero-trust approach and bring IT control over sharing.
FileFlex Enterprise sharing forces zero-trust user authentication and layered security
FileFlex Enterprise mitigates this method of delivering malware because instead of allowing share recipients access to files through email links and attachments you are giving them IT-controlled access to files in their source locations or upload permission to virtual data rooms to verified trusted senders. The access is always through the FileFlex application and never through the use of attachments or links and access to the sharing itself goes through user authentication, optional device authentication, U2F, and layered security. It is the perfect tool if you are augmenting your perimeter-based security paradigm with zero trust by always authenticating and always verifying all transactions all the time or “never trust, always verify”.
FileFlex Enterprise addresses spoofing and impersonation
For example, with an external sender, you can have them upload to a FileFlex Enterprise data room. Sending and fulfilling the request through FileFlex Enterprise forces sender authentication. Zero-trust user authentication addresses spoofing and impersonation and mitigates spear-phishing.
Watch a detailed explanation
In the podinar produced by the Edge Computing Association below, Tom Ward, VP of Marketing for Qnext explains vectors of attack, including spear-phishing, and how you can address them using FileFlex Enterprise.
[1] https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
[2] https://www.symantec.com/security-center/threat-report